有线无线用户统一接入简介
在实际的使用场景中,有线网络和无线网络环境通常是共同存在的。例如在办公区内PC电脑、打印机等设备通常通过有线方式接入网络,而笔记本、手机终端等移动设备通常是通过无线方式接入网络。通过部署有线无线用户统一接入的网络环境,可以同时为有线用户和无线用户提供网络接入的服务,实现对有线用户和无线用户的统一管理。
配置注意事项
本举例使用Portal认证,为保证实际网络的安全性,请根据实际的需求配置合适的安全策略。
隧道转发模式下,管理VLAN和业务VLAN不能配置为同一VLAN。直接转发模式下,管理VLAN和业务VLAN建议也不要配置为同一VLAN。
数据转发方式为直接转发时,建议在直接连接AP的设备接口上配置端口隔离,如果不配置端口隔离,可能会在VLAN内存在不必要的广播报文,或者导致不同AP间的WLAN用户二层互通的问题。
配置管理VLAN和业务VLAN:
隧道转发模式下,业务报文会封装在CAPWAP数据隧道中进行传输,发送给AC,然后由AC再转发到上层网络或AP,所以只要配置AC与AP间的网络加入管理VLAN,AC与上层网络间的网络加入业务VLAN,就能正常传输业务报文和管理报文。直接转发模式下,业务报文不会进行CAPWAP封装,而是直接转发给上层网络或AP,所以需要配置AC与AP间的网络加入管理VLAN,AP与上层网络间的网络加入业务VLAN,才能正常传输业务报文和管理报文。
配置源接口方式:
V200R006版本中,配置源接口的方式是在WLAN视图下执行命令wlan ac source interface { loopback loopback-number | vlanif vlan-id }V200R007和V200R008版本中,配置源接口的方式是在系统视图下执行命令capwap source interface { loopback loopback-number | vlanif vlan-id }
纯组播报文由于协议要求在无线空口没有ACK机制保障,且无线空口链路不稳定,为了纯组播报文能够稳定发送,通常会以低速报文形式发送。如果网络侧有大量异常组播流量涌入,则会造成无线空口拥堵。为了减小大量低速组播报文对无线网络造成的冲击,建议配置组播报文抑制功能。配置前请确认是否有组播业务,如果有,请谨慎配置限速值。
业务数据转发方式采用直接转发时,建议在直连AP的交换机接口上配置组播报文抑制。业务数据转发方式采用隧道转发时,建议在AC的流量模板下配置组播报文抑制。
组网需求
某医院由于业务要求,需要在其医院大楼内同时部署有线和无线网络。为方便管理维护,管理员希望能够在AC上集中管理有线用户和无线用户,有线用户采取免认证方式,无线用户采用Portal认证方式,并且无线用户能够在AC内漫游。
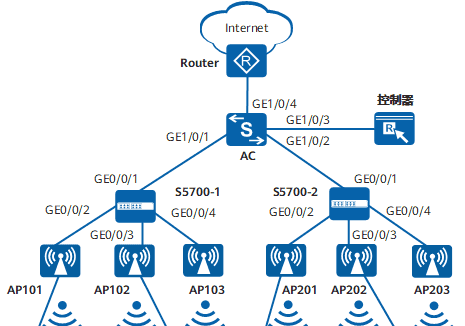
如图1所示,AC上行连接出口网关Router;下行通过接入交换机S5700-1和S5700-2连接和管理AP,其中,S5700-1部署在一楼,S5700-2部署在二楼。在每个房间内部署AP2010DN为房间内用户同时提供有线接入和无线接入,在楼道中部署AP5030DN提供无线网络覆盖。S5700-1和S5700-2均为PoE交换机,为连接的AP供电。
为使整体网络规划简洁,便于管理,接入交换机只做二层透传,所有网关配置在AC上。
AC作为DHCP服务器为AP、STA和PC分配IP地址。
图1 配置有线无线用户统一接入组网图
数据规划
|
表2 网络数据规划表 |
|||
|
项目 |
接口号 |
所属VLAN |
说明 |
|
AC |
GE1/0/1 |
100、201 |
连接S5700-1 |
|
GE1/0/2 |
100、202 |
连接S5700-2 |
|
|
GE1/0/3 |
200 |
连接控制器 |
|
|
GE1/0/4 |
300 |
连接出口网关 |
|
|
S5700-1 |
GE0/0/1 |
100、201 |
连接AC |
|
GE0/0/2 |
100、201 |
连接AP101 |
|
|
GE0/0/3 |
100、201 |
连接AP102 |
|
|
GE0/0/4 |
100、201 |
连接AP103 |
|
|
S5700-2 |
GE0/0/1 |
100、202 |
连接AC |
|
GE0/0/2 |
100、202 |
连接AP201 |
|
|
GE0/0/3 |
100、202 |
连接AP202 |
|
|
GE0/0/4 |
100、202 |
连接AP203 |
|
|
AP101、AP102 |
Eth0/0/0 Eth0/0/1 GE0/0/0 |
201 |
GE0/0/0连接S5700-1 Eth0/0/0和Eth0/0/1连接下行有线用户 AP101和AP102为AP2010DN,部署在一楼房间内,同时提供有线和无线接入 |
|
AP103 |
– |
– |
AP103为AP5030DN,部署在一楼楼道中,提供无线接入 |
|
AP201、AP202 |
Eth0/0/0 Eth0/0/1 GE0/0/0 |
202 |
GE0/0/0连接S5700-2 Eth0/0/0和Eth0/0/1连接下行有线用户 AP201和AP202为AP2010DN,部署在二楼房间内,同时提供有线和无线接入 |
|
AP203 |
– |
– |
AP203为AP5030DN,部署在二楼楼道中,提供无线接入 |
|
表3 业务数据规划表 |
||
|
项目 |
数据 |
说明 |
|
AC的源接口IP地址 |
10.23.100.1/24 |
– |
|
国家码 |
CN |
– |
|
WMM模板 |
名称:wmm |
– |
|
射频模板 |
名称:radio |
– |
|
安全模板 |
名称:security安全与认证策略:OPEN |
– |
|
流量模板 |
名称:traffic |
– |
|
服务集 |
名称:floor_1SSID:hospital-wlanWLAN虚接口:WLAN-ESS1业务数据转发模式:隧道转发 |
用于一楼的无线网络覆盖 |
| 名称:floor_2SSID:hospital-wlanWLAN虚接口:WLAN-ESS2业务数据转发模式:隧道转发 |
用于二楼的无线网络覆盖 |
|
|
DHCP服务器 |
AC作为DHCP服务器,为AP、STA和PC分配地址 |
– |
|
AP的网关及IP地址池范围 |
VLANIF100:10.23.100.1/24 10.23.100.2~10.23.100.254/24 |
– |
|
无线用户的网关及IP地址池范围 |
VLANIF101:10.23.101.1/24 10.23.101.2~10.23.101.254/24 |
– |
|
VLANIF102:10.23.102.1/24 10.23.102.2~10.23.102.254/24 |
– |
|
|
有线用户的网关及IP地址池范围 |
VLANIF201:10.23.201.1/24 10.23.201.2~10.23.201.254/24 |
– |
|
VLANIF202:10.23.202.1/24 10.23.202.2~10.23.202.254/24 |
– |
|
|
服务器参数 |
认证服务器: IP地址:10.23.200.1端口号:1812RADIUS共享密钥:YsHsjx_202206 |
业务控制器同时提供RADIUS服务器和Portal服务器的功能,所以认证服务器、计费服务器、授权服务器和Portal服务器的IP地址都为业务控制器的IP地址。配置RADIUS计费服务器,以便获取终端用户的上下线信息。认证服务器和计费服务器的端口号必须与RADIUS服务器的认证端口和计费端口一致。配置授权服务器以便RADIUS服务器向AC下发授权规则。授权服务器的RADIUS共享密钥必须与认证服务器和计费服务器的RADIUS共享密钥一致。 |
|
计费服务器: IP地址:10.23.200.1端口号:1813RADIUS共享密钥:YsHsjx_202206 |
||
|
授权服务器: IP地址:10.23.200.1RADIUS共享密钥:YsHsjx_202206 |
||
|
Portal服务器: IP地址:10.23.200.1AC处理Portal协议报文的端口号:2000AC向Portal服务器主动发送报文时使用的目的端口号:50200Portal认证共享密钥:YsHsjx_202206Portal服务器与AC对接的URL参数传输加解密密钥:YsHsjx_202206 |
||
|
表4 射频信道数据规划表 |
||
|
项目 |
数据 |
说明 |
|
AP101 |
射频0:信道1、功率等级10 |
使用WLAN planner网规工具规划各AP位置及AP射频的工作信道、功率等,配置信道模式和功率模式为固定模式,为每个AP配置各自的信道和功率。 |
|
AP102 |
射频0:信道6、功率等级10 |
|
|
AP103 |
射频0:信道11、功率等级10 射频1:信道153、功率等级10 |
|
|
AP201 |
射频0:信道1、功率等级10 |
|
|
AP202 |
射频0:信道6、功率等级10 |
|
|
AP203 |
射频0:信道11、功率等级10 射频1:信道157、功率等级10 |
|
配置思路
采用如下的思路配置有线无线用户统一接入示例:
配置各网络设备,使AP、接入交换机S5700-1、S5700-2、AC和上层网络设备之间实现网络互通。配置AC作为DHCP服务器,为AP、有线用户和无线用户分配IP地址。配置RADIUS服务器认证、计费和授权模板和Portal认证。配置WLAN基本业务,包括AC系统参数、AC上管理AP和WLAN业务参数。配置VAP并下发配置。验证配置结果,有线用户和无线用户都能够接入Internet。
操作步骤
配置各网络设备互通
# 配置交换机S5700-1和S5700-2的接口GE0/0/1~GE0/0/4都加入VLAN100(管理VLAN),S5700-1的接口GE0/0/1~GE0/0/4加入VLAN201(有线业务报文所属VLAN),S5700-2的接口GE0/0/1~GE0/0/4加入VLAN202(有线业务报文所属VLAN),其中直连AP的接口需要配置PVID,并建议直连AP的接口配置端口隔离以减少广播报文。以配置S5700-1为例,S5700-2的配置与S5700-1类似,具体请参考配置文件。
[HUAWEI] sysname S5700-1
[S5700-1] vlan batch 100 201
[S5700-1] interface gigabitethernet 0/0/1
[S5700-1-GigabitEthernet0/0/1] port link-type trunk
[S5700-1-GigabitEthernet0/0/1] port trunk allow-pass vlan 100 201
[S5700-1-GigabitEthernet0/0/1] quit
[S5700-1] interface gigabitethernet 0/0/2
[S5700-1-GigabitEthernet0/0/2] port link-type trunk
[S5700-1-GigabitEthernet0/0/2] port trunk allow-pass vlan 100 201
[S5700-1-GigabitEthernet0/0/2] port trunk pvid vlan 100 //直连AP的接口需要配置PVID
[S5700-1-GigabitEthernet0/0/2] port-isolate enable //配置端口隔离以减少广播报文
[S5700-1-GigabitEthernet0/0/2] quit
[S5700-1] interface gigabitethernet 0/0/3
[S5700-1-GigabitEthernet0/0/3] port link-type trunk
[S5700-1-GigabitEthernet0/0/3] port trunk allow-pass vlan 100 201
[S5700-1-GigabitEthernet0/0/3] port trunk pvid vlan 100
[S5700-1-GigabitEthernet0/0/3] port-isolate enable
[S5700-1-GigabitEthernet0/0/3] quit
[S5700-1] interface gigabitethernet 0/0/4
[S5700-1-GigabitEthernet0/0/4] port link-type trunk
[S5700-1-GigabitEthernet0/0/4] port trunk allow-pass vlan 100 201
[S5700-1-GigabitEthernet0/0/4] port trunk pvid vlan 100
[S5700-1-GigabitEthernet0/0/4] port-isolate enable
[S5700-1-GigabitEthernet0/0/4] quit
# 配置AC连接接入交换机S5700-1的接口GE1/0/1加入VLAN100和VLAN201,连接接入交换机S5700-2的接口GE1/0/2加入VLAN100和VLAN202,连接上层网络的接口GE1/0/4加入VLAN300,连接控制器的接口GE1/0/3加入VLAN200。
[HUAWEI] sysname AC
[AC] vlan batch 100 200 201 202 300
[AC] interface gigabitethernet 1/0/1
[AC-GigabitEthernet1/0/1] port link-type trunk
[AC-GigabitEthernet1/0/1] port trunk allow-pass vlan 100 201
[AC-GigabitEthernet1/0/1] quit
[AC] interface gigabitethernet 1/0/2
[AC-GigabitEthernet1/0/2] port link-type trunk
[AC-GigabitEthernet1/0/2] port trunk allow-pass vlan 100 202
[AC-GigabitEthernet1/0/2] quit
[AC] interface gigabitethernet 1/0/3
[AC-GigabitEthernet1/0/3] port link-type trunk
[AC-GigabitEthernet1/0/3] port trunk allow-pass vlan 200
[AC-GigabitEthernet1/0/3] quit
[AC] interface gigabitethernet 1/0/4
[AC-GigabitEthernet1/0/4] port link-type trunk
[AC-GigabitEthernet1/0/4] port trunk allow-pass vlan 300
[AC-GigabitEthernet1/0/4] quit
# 配置VLANIF200,用于AC和控制器通信。
[AC] interface vlanif200
[AC-Vlanif200] ip address 10.23.200.2 24 //配置IP地址用于AC和控制器通信
[AC-Vlanif200] quit
配置AC为DHCP Server,分别为PC、AP、STA分配IP地址
DNS服务器地址请根据实际需要配置。常用配置方法如下:
接口地址池场景,需要在VLANIF接口视图下执行命令dhcp server dns-list ip-address &<1-8>。全局地址池场景,需要在IP地址池视图下执行命令dns-list ip-address &<1-8>。
# 配置AC通过接口地址池为PC、AP、STA分配IP地址。
[AC] dhcp enable
[AC] vlan batch 101 102
[AC] interface vlanif 100 //配置接口地址池为AP分配IP地址
[AC-Vlanif100] description manage_ap
[AC-Vlanif100] ip address 10.23.100.1 24
[AC-Vlanif100] dhcp select interface
[AC-Vlanif100] quit
[AC] interface vlanif 101 //配置接口地址池为一楼无线用户STA分配IP地址
[AC-Vlanif101] description manage_floor1_sta
[AC-Vlanif101] ip address 10.23.101.1 24
[AC-Vlanif101] dhcp select interface
[AC-Vlanif101] quit
[AC] interface vlanif 102 //配置接口地址池为二楼无线用户STA分配IP地址
[AC-Vlanif102] description manage_floor2_sta
[AC-Vlanif102] ip address 10.23.102.1 24
[AC-Vlanif102] dhcp select interface
[AC-Vlanif102] quit
[AC] interface vlanif 201 //配置接口地址池为一楼有线用户PC分配IP地址
[AC-Vlanif201] description manage_floor1_pc
[AC-Vlanif201] ip address 10.23.201.1 24
[AC-Vlanif201] dhcp select interface
[AC-Vlanif201] quit
[AC] interface vlanif 202 //配置接口地址池为二楼有线用户PC分配IP地址
[AC-Vlanif202] description manage_floor2_pc
[AC-Vlanif202] ip address 10.23.202.1 24
[AC-Vlanif202] dhcp select interface
[AC-Vlanif202] quit
配置RADIUS服务器认证、计费和授权模板和Portal认证
# 配置AC的RADIUS服务器认证、计费和授权模板。
[AC] radius-server template radius1 //创建名为radius1的RADIUS服务器模板
[AC-radius-radius1] radius-server authentication 10.23.200.1 1812 source ip-address 10.23.200.2 weight 80 //配置RADIUS认证服务器,认证端口1812,AC使用10.23.200.2和RADIUS服务器通信
[AC-radius-radius1] radius-server accounting 10.23.200.1 1813 source ip-address 10.23.200.2 weight 80 //配置RADIUS计费服务器,以便获取终端用户的上下线信息,计费端口1813,AC使用10.23.200.2和RADIUS服务器通信
[AC-radius-radius1] radius-server shared-key cipher YsHsjx_202206 //配置RADIUS服务器预共享密钥
[AC-radius-radius1] undo radius-server user-name domain-included //设备向RADIUS服务器发送的用户名不包含域名,当RADIUS服务器不接受带域名的用户时需要配置
[AC-radius-radius1] quit
[AC] radius-server authorization 10.23.200.1 shared-key cipher YsHsjx_202206 //配置RADIUS授权服务器的地址,共享密钥为YsHsjx_202206,必须与认证密钥和计费密钥一致。配置授权服务器以便RADIUS服务器向AC下发授权规则
[AC] aaa
[AC-aaa] authentication-scheme radius1 //创建名为radius1的认证方案
[AC-aaa-authen-radius1] authentication-mode radius //控制器作为RADIUS服务器,认证方案必须配置为RADIUS
[AC-aaa-authen-radius1] quit
[AC-aaa] accounting-scheme radius1 //创建名为radius1的计费方案
[AC-aaa-accounting-radius1] accounting-mode radius //配置计费方案为RADIUS方式。为了方便RADIUS服务器维护账号的状态信息,例如上下线信息,强制帐号下线,计费模式必须配置为radius
[AC-aaa-accounting-radius1] quit
[AC-aaa] domain portal1 //创建名为portal1的域
[AC-aaa-domain-portal1] authentication-scheme radius1 //绑定认证方案radius1
[AC-aaa-domain-portal1] accounting-scheme radius1 //绑定计费方案radius1
[AC-aaa-domain-portal1] radius-server radius1 //绑定RADIUS服务器模板radius1
[AC-aaa-domain-portal1] quit
[AC-aaa] quit
# 配置Portal服务器。
[AC] web-auth-server portal1 //创建名为portal1的Portal服务器模板
[AC-web-auth-server-portal1] server-ip 10.23.200.1 //配置Portal服务器的IP地址
[AC-web-auth-server-portal1] port 50200 //配置设备向Portal服务器主动发送报文时使用的目的端口号为50200,缺省为50200
[AC-web-auth-server-portal1] shared-key cipher YsHsjx_202206 //配置AC与Portal服务器信息交互的共享密钥
[AC-web-auth-server-portal1] url http://10.23.200.1:8080/portal //配置指向Portal服务器的URL
[AC-web-auth-server-portal1] quit
# 在WLAN-ESS接口下绑定Portal服务器模板,使能Portal认证的功能,对无线用户进行Portal认证,有线用户进行免认证。
[AC] interface wlan-ess 1
[AC-Wlan-Ess1] domain name portal1 force //配置用户强制域为portal1
[AC-Wlan-Ess1] domain name portal1 //配置用户默认域为portal1
[AC-Wlan-Ess1] authentication portal //配置认证功能为Portal认证
[AC-Wlan-Ess1] web-auth-server portal1 direct //绑定名为portal1的Portal服务器模板并指定Portal认证方式为二层认证方式
[AC-Wlan-Ess1] quit
[AC] interface wlan-ess 2
[AC-Wlan-Ess2] domain name portal1 force //配置用户强制域为portal1
[AC-Wlan-Ess2] domain name portal1 //配置用户默认域为portal1
[AC-Wlan-Ess2] authentication portal //配置认证功能为Portal认证
[AC-Wlan-Ess2] web-auth-server portal1 direct //绑定名为portal1的Portal服务器模板并指定Portal认证方式为二层认证方式
[AC-Wlan-Ess2] quit
配置AC的系统参数
# 配置AC的国家码。
[AC] wlan ac-global country-code cn //配置AC的国家码,使AC管理的AP的射频特性符合不同国家或区域的法律法规要求,国家码缺省值为CNWarning: Modifying the country code will clear channel configurations of the AP radio using the country code and reset the AP. If th
e new country code does not support the radio, all configurations of the radio are cleared. Continue?[Y/N]:y
# 配置AC ID和运营商标识。
[AC] wlan ac-global ac id 1 carrier id other //AC ID缺省为0,修改为1
# 配置AC的源接口。
[AC] capwap source interface vlanif 100
[AC] wlan
在AC上管理AP
# 现场获取AP的MAC地址后,查看AP的设备类型ID。
[AC-wlan-view] display ap-type all
All AP types information:
——————————————————————————
ID Type
——————————————————————————
17 AP6010SN-GN
19 AP6010DN-AGN
21 AP6310SN-GN
23 AP6510DN-AGN
25 AP6610DN-AGN
27 AP7110SN-GN
28 AP7110DN-AGN
29 AP5010SN-GN
30 AP5010DN-AGN
31 AP3010DN-AGN
33 AP6510DN-AGN-US
34 AP6610DN-AGN-US
35 AP5030DN
36 AP5130DN
37 AP7030DE
38 AP2010DN
39 AP8130DN
40 AP8030DN
42 AP9330DN
43 AP4030DN
44 AP4130DN
45 AP3030DN
46 AP2030DN
——————————————————————————
Total number: 23
# 配置AP认证模式为MAC地址认证(缺省值,不需配置)。根据查询到的AP设备类型ID,离线添加AP。
[AC-wlan-view] ap id 101 type-id 38 mac 00e0-fc76-e320 //离线添加MAC地址为00e0-fc76-e320的AP2010DN,AP ID为101
[AC-wlan-ap-101] quit
[AC-wlan-view] ap id 102 type-id 38 mac 00e0-fc76-e340 //离线添加MAC地址为00e0-fc76-e340的AP2010DN,AP ID为102
[AC-wlan-ap-102] quit
[AC-wlan-view] ap id 103 type-id 35 mac 00e0-fc04-b520 //离线添加MAC地址为00e0-fc04-b520的AP5030DN,AP ID为103
[AC-wlan-ap-103] quit
[AC-wlan-view] ap id 201 type-id 38 mac 00e0-fc76-e360 //离线添加MAC地址为00e0-fc76-e360的AP2010DN,AP ID为201
[AC-wlan-ap-201] quit
[AC-wlan-view] ap id 202 type-id 38 mac 00e0-fc76-e380 //离线添加MAC地址为00e0-fc76-e380的AP2010DN,AP ID为202
[AC-wlan-ap-202] quit
[AC-wlan-view] ap id 203 type-id 35 mac 00e0-fc04-b540 //离线添加MAC地址为00e0-fc04-b540的AP5030DN,AP ID为203
[AC-wlan-ap-203] quit
# 配置AP域并将AP加入到AP域。
[AC-wlan-view] ap-region id 1 //创建AP域1,部署在一楼的AP都加入到AP域1
[AC-wlan-ap-region-1] ap-region-name floor1 //AP域1命名为floor1
[AC-wlan-ap-region-1] quit
[AC-wlan-view] ap id 101
[AC-wlan-ap-101] region-id 1 //AP 101加入到AP域1中
[AC-wlan-ap-101] quit
[AC-wlan-view] ap id 102
[AC-wlan-ap-102] region-id 1
[AC-wlan-ap-102] quit
[AC-wlan-view] ap id 103
[AC-wlan-ap-103] region-id 1
[AC-wlan-ap-103] quit
[AC-wlan-view] ap-region id 2 //创建AP域2,部署在二楼的AP都加入到AP域2
[AC-wlan-ap-region-2] ap-region-name floor2
[AC-wlan-ap-region-2] quit
[AC-wlan-view] ap id 201
[AC-wlan-ap-201] region-id 2
[AC-wlan-ap-201] quit
[AC-wlan-view] ap id 202
[AC-wlan-ap-202] region-id 2
[AC-wlan-ap-202] quit
[AC-wlan-view] ap id 203
[AC-wlan-ap-203] region-id 2
[AC-wlan-ap-203] quit
# 将AP上电后,当查看到AP的“AP State”字段为“normal”,表明AP在AC中正常上线。
[AC-wlan-view] display ap all
All AP(s) information:
Normal[6],Fault[0],Commit-failed[0],Committing[0],Config[0],Download[0]
Config-failed[0],Standby[0],Type-not-match[0],Ver-mismatch[0]
——————————————————————————
AP AP AP Profile AP AP
/Region
ID Type MAC ID State Sysname
——————————————————————————
101 AP2010DN 00e0-fc76-e320 0/1 normal ap-101
102 AP2010DN 00e0-fc76-e340 0/1 normal ap-102
103 AP5030DN 00e0-fc04-b520 0/1 normal ap-103
201 AP2010DN 00e0-fc76-e360 0/2 normal ap-201
202 AP2010DN 00e0-fc76-e380 0/2 normal ap-202
203 AP5030DN 00e0-fc04-b540 0/2 normal ap-203
——————————————————————————
Total number: 6,printed: 6
# 配置AP2010DN的上行有线口GE0/0/0和下行接口Eth0/0/0、Eth0/0/1允许有线业务报文通过。
[AC-wlan-view] ap id 101
[AC-wlan-ap-101] lineate-port ethernet 0 pvid vlan 201 //AP2010DN下行接口用于连接PC等有线用户终端,需要配置PVID,VLAN201用于传输一楼的有线业务报文
[AC-wlan-ap-101] lineate-port ethernet 0 vlan untagged 201 //AP2010DN下行接口用于连接PC等有线用户终端,需要配置untagged
[AC-wlan-ap-101] lineate-port ethernet 1 pvid vlan 201
[AC-wlan-ap-101] lineate-port ethernet 1 vlan untagged 201
[AC-wlan-ap-101] lineate-port gigabitethernet 0 vlan tagged 201 //AP2010DN上行接口用于连接上行网络设备,需要配置tagged
[AC-wlan-ap-101] quit
[AC-wlan-view] ap id 102
[AC-wlan-ap-102] lineate-port ethernet 0 pvid vlan 201
[AC-wlan-ap-102] lineate-port ethernet 0 vlan untagged 201
[AC-wlan-ap-102] lineate-port ethernet 1 pvid vlan 201
[AC-wlan-ap-102] lineate-port ethernet 1 vlan untagged 201
[AC-wlan-ap-102] lineate-port gigabitethernet 0 vlan tagged 201
[AC-wlan-ap-102] quit
[AC-wlan-view] ap id 201
[AC-wlan-ap-201] lineate-port ethernet 0 pvid vlan 202 //AP2010DN下行接口用于连接PC等有线用户终端,需要配置PVID,VLAN202用于传输二楼的有线业务报文
[AC-wlan-ap-201] lineate-port ethernet 0 vlan untagged 202
[AC-wlan-ap-201] lineate-port ethernet 1 pvid vlan 202
[AC-wlan-ap-201] lineate-port ethernet 1 vlan untagged 202
[AC-wlan-ap-201] lineate-port gigabitethernet 0 vlan tagged 202
[AC-wlan-ap-201] quit
[AC-wlan-view] ap id 202
[AC-wlan-ap-202] lineate-port ethernet 0 pvid vlan 202
[AC-wlan-ap-202] lineate-port ethernet 0 vlan untagged 202
[AC-wlan-ap-202] lineate-port ethernet 1 pvid vlan 202
[AC-wlan-ap-202] lineate-port ethernet 1 vlan untagged 202
[AC-wlan-ap-202] lineate-port gigabitethernet 0 vlan tagged 202
[AC-wlan-ap-202] quit
配置WLAN业务参数
# 创建名为“wmm”的WMM模板。
[AC-wlan-view] wmm-profile name wmm id 1
[AC-wlan-wmm-prof-wmm] quit
# 创建名为“radio”的射频模板,绑定WMM模板“wmm”。
[AC-wlan-view] radio-profile name radio id 1
[AC-wlan-radio-prof-radio] wmm-profile name wmm
[AC-wlan-radio-prof-radio] power-mode fixed //配置射频的功率模式为固定模式
[AC-wlan-radio-prof-radio] channel-mode fixed //配置射频的功率模式为固定模式
[AC-wlan-radio-prof-radio] quit
[AC-wlan-view] quit
# 创建WLAN-ESS接口1和2。
[AC] interface wlan-ess 1
[AC-Wlan-Ess1] port trunk allow-pass vlan 101 102 //配置wlan-ess接口允许所有的无线业务VLAN通过,是AC内漫游的必备条件之一
[AC-Wlan-Ess1] quit
[AC] interface wlan-ess 2
[AC-Wlan-Ess2] port trunk allow-pass vlan 101 102
[AC-Wlan-Ess2] quit
# 创建名为“security”的安全模板。
[AC] wlan
[AC-wlan-view] security-profile name security id 1 //接口下已经使能了Portal认证,所以安全策略使用缺省的OPEN方式,不认证,不加密
[AC-wlan-sec-prof-security] quit
# 创建名为“traffic”的流量模板。
[AC-wlan-view] traffic-profile name traffic id 1
[AC-wlan-traffic-prof-traffic] quit
# 创建名为“floor1”和“floor2”的服务集并绑定业务VLAN、WLAN-ESS接口、安全模板和流量模板,转发模式为隧道转发。
[AC-wlan-view] service-set name floor1 id 1 //创建名为floor1的服务集
[AC-wlan-service-set-floor1] ssid hospital-wlan //配置SSID为hospital-wlan
[AC-wlan-service-set-floor1] wlan-ess 1 //绑定WLAN-ESS接口
[AC-wlan-service-set-floor1] security-profile name security //绑定名为security的安全模板
[AC-wlan-service-set-floor1] traffic-profile name traffic //绑定名为traffic的流量模板
[AC-wlan-service-set-floor1] service-vlan 101 //绑定业务VLAN101
[AC-wlan-service-set-floor1] forward-mode tunnel //配置转发模式为隧道转发,缺省为直接转发
[AC-wlan-service-set-floor1] user-isolate //配置同一个虚拟接入点下的所有用户二层隔离
[AC-wlan-service-set-floor1] quit
[AC-wlan-view] service-set name floor2 id 2
[AC-wlan-service-set-floor2] ssid hospital-wlan //配置SSID为hospital-wlan,所有服务集配置相同的SSID,是AC内漫游的必备条件之一
[AC-wlan-service-set-floor2] wlan-ess 2
[AC-wlan-service-set-floor2] security-profile name security //绑定名为security的安全模板,所有服务集绑定相同的安全模板,是AC内漫游的必备条件之一
[AC-wlan-service-set-floor2] traffic-profile name traffic
[AC-wlan-service-set-floor2] service-vlan 102
[AC-wlan-service-set-floor2] forward-mode tunnel
[AC-wlan-service-set-floor2] user-isolate
[AC-wlan-service-set-floor2] quit
配置VAP并下发
# 配置VAP。
[AC-wlan-view] ap 101 radio 0 //配置AP2010DN的射频0
[AC-wlan-radio-101/0] radio-profile name radio //配置射频上绑定射频模板
[AC-wlan-radio-101/0] service-set name floor1 //配置射频上绑定服务集,射频绑定服务集后,会生成一个VAP
[AC-wlan-radio-101/0] channel 20mhz 1 //根据WLAN planner网规工具规划的结果配置信道
[AC-wlan-radio-101/0] power-level 10 //根据WLAN planner网规工具规划的结果配置功率
[AC-wlan-radio-101/0] quit
[AC-wlan-view] ap 102 radio 0
[AC-wlan-radio-102/0] radio-profile name radio
[AC-wlan-radio-102/0] service-set name floor1
[AC-wlan-radio-102/0] channel 20mhz 6
[AC-wlan-radio-102/0] power-level 10
[AC-wlan-radio-102/0] quit
[AC-wlan-view] ap 103 radio 0
[AC-wlan-radio-103/0] radio-profile name radio
[AC-wlan-radio-103/0] service-set name floor1
[AC-wlan-radio-103/0] channel 20mhz 11
[AC-wlan-radio-103/0] power-level 10
[AC-wlan-radio-103/0] quit
[AC-wlan-view] ap 103 radio 1 //AP5030支持两个射频,此步配置射频1
[AC-wlan-radio-103/1] radio-profile name radio
[AC-wlan-radio-103/1] service-set name floor1
[AC-wlan-radio-103/1] channel 20mhz 153
[AC-wlan-radio-103/1] power-level 10
[AC-wlan-radio-103/1] quit
[AC-wlan-view] ap 201 radio 0
[AC-wlan-radio-201/0] radio-profile name radio
[AC-wlan-radio-201/0] service-set name floor2
[AC-wlan-radio-201/0] channel 20mhz 1
[AC-wlan-radio-201/0] power-level 10
[AC-wlan-radio-201/0] quit
[AC-wlan-view] ap 202 radio 0
[AC-wlan-radio-202/0] radio-profile name radio
[AC-wlan-radio-202/0] service-set name floor2
[AC-wlan-radio-202/0] channel 20mhz 6
[AC-wlan-radio-202/0] power-level 10
[AC-wlan-radio-202/0] quit
[AC-wlan-view] ap 203 radio 0
[AC-wlan-radio-203/0] radio-profile name radio
[AC-wlan-radio-203/0] service-set name floor2
[AC-wlan-radio-203/0] channel 20mhz 11
[AC-wlan-radio-203/0] power-level 10
[AC-wlan-radio-203/0] quit
[AC-wlan-view] ap 203 radio 1
[AC-wlan-radio-203/1] radio-profile name radio
[AC-wlan-radio-203/1] service-set name floor2
[AC-wlan-radio-203/1] channel 20mhz 157
[AC-wlan-radio-203/1] power-level 10
[AC-wlan-radio-203/1] quit
# 下发配置。
[AC-wlan-view] commit all //在AC上配置关于AP的WLAN业务配置后,需要下发配置到AP上才能最终生效
Warning: Committing configuration may cause service interruption, continue?[Y/N]
:y
验证配置结果
# 配置完成后,通过display vap all命令,可以查看到VAP已创建成功。
[AC-wlan-view] display vap all
All VAP Information(Total-8):
SS: Service-set BP: Bridge-profile MP: Mesh-profile
———————————————————————-
AP ID Radio ID SS ID BP ID MP ID WLAN ID BSSID Type
———————————————————————-
101 0 1 – – 1 00e0-fc76-e320 service
102 0 1 – – 1 00e0-fc76-e340 service
103 0 1 – – 1 00e0-fc04-b520 service
103 1 1 – – 1 00e0-fc04-b530 service
201 0 2 – – 1 00e0-fc76-e360 service
202 0 2 – – 1 00e0-fc76-e380 service
203 0 2 – – 1 00e0-fc04-b540 service
203 1 2 – – 1 00e0-fc04-b550 service
———————————————————————-
Total: 8
# STA搜索到名为“hospital-wlan”的无线网络并正常关联后,STA能够被分配相应的IP地址,用户输入密钥可以访问无线网络,在AC上执行display station assoc-info命令,可以查看到用户已经接入到无线网络“hospital-wlan”中。
[AC-wlan-view] display station assoc-info all
AP/Rf/WLAN: AP ID/Radio ID/WLAN ID
Rx/Tx: link receive rate/link transmit rate(Mbps)
——————————————————————————
STA MAC AP/Rf/WLAN Rx/Tx Mode RSSI IP address
SSID
——————————————————————————
00e0-fcc7-1e08 101/0/1 6/11 11n -89 10.23.101.254
hospital-wlan
——————————————————————————
Total stations: 1
# 无线用户STA和有线用户PC能够分配到IP地址,正常连接网络。
配置文件
接入交换机S5700-1的配置文件
#
sysname S5700-1
#
vlan batch 100 201
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 100 201
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk pvid vlan 100
port trunk allow-pass vlan 100 201
port-isolate enable group 1
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk pvid vlan 100
port trunk allow-pass vlan 100 201
port-isolate enable group 1
#
interface GigabitEthernet0/0/4
port link-type trunk
port trunk pvid vlan 100
port trunk allow-pass vlan 100 201
port-isolate enable group 1
#
return
接入交换机S5700-2的配置文件
#
sysname S5700-2
#
vlan batch 100 202
#
interface GigabitEthernet0/0/1
port link-type trunk
port trunk allow-pass vlan 100 202
#
interface GigabitEthernet0/0/2
port link-type trunk
port trunk pvid vlan 100
port trunk allow-pass vlan 100 202
port-isolate enable group 1
#
interface GigabitEthernet0/0/3
port link-type trunk
port trunk pvid vlan 100
port trunk allow-pass vlan 100 202
port-isolate enable group 1
#
interface GigabitEthernet0/0/4
port link-type trunk
port trunk pvid vlan 100
port trunk allow-pass vlan 100 202
port-isolate enable group 1
#
return
AC的配置文件
#
sysname AC
#
vlan batch 100 to 102 200 to 202 300
#
wlan ac-global carrier id other ac id 1
#
dhcp enable
#
radius-server template radius1
radius-server shared-key cipher %#%#ut)92(w&0@UJ}J7}^3Z9x`9~Y$`2D1AGwDQ[+S.%#%#
radius-server authentication 10.23.200.1 1812 source ip-address 10.23.200.2 weight 80
radius-server accounting 10.23.200.1 1813 source ip-address 10.23.200.2 weight 80
undo radius-server user-name domain-included
radius-server authorization 10.23.200.1 shared-key cipher %#%#[m1~SG]5CAzg~K35!b^Wa';{=+k_40QYK~}UX6T%#%#
#
web-auth-server portal1
server-ip 10.23.200.1
port 50200
shared-key cipher %#%#^B],0yW|oJ1;j:U&`%}(=@2t*]e.$TOVrx@(I6rT%#%#
url http://10.23.200.1:8080/portal
#
aaa
authentication-scheme radius1
authentication-mode radius
accounting-scheme radius1
accounting-mode radius
domain portal1
authentication-scheme radius1
accounting-scheme radius1
radius-server radius1
#
interface Vlanif100
description manage_ap
ip address 10.23.100.1 255.255.255.0
dhcp select interface
#
interface Vlanif101
description manage_floor1_sta
ip address 10.23.101.1 255.255.255.0
dhcp select interface
#
interface Vlanif102
description manage_floor2_sta
ip address 10.23.102.1 255.255.255.0
dhcp select interface
#
interface Vlanif200
ip address 10.23.200.2 255.255.255.0
#
interface Vlanif201
description manage_floor1_pc
ip address 10.23.201.1 255.255.255.0
dhcp select interface
#
interface Vlanif202
description manage_floor2_pc
ip address 10.23.202.1 255.255.255.0
dhcp select interface
#
interface GigabitEthernet1/0/1
port link-type trunk
port trunk allow-pass vlan 100 201
#
interface GigabitEthernet1/0/2
port link-type trunk
port trunk allow-pass vlan 100 202
#
interface GigabitEthernet1/0/3
port link-type trunk
port trunk allow-pass vlan 200
#
interface GigabitEthernet1/0/4
port link-type trunk
port trunk allow-pass vlan 300
#
interface Wlan-Ess1
port trunk allow-pass vlan 101 to 102
domain name portal1 force
domain name portal1
authentication portal
web-auth-server portal1 direct
#
interface Wlan-Ess2
port trunk allow-pass vlan 101 to 102
domain name portal1 force
domain name portal1
authentication portal
web-auth-server portal1 direct
#
capwap source interface vlanif100
#
wlan
ap-region id 1
ap-region-name floor1
ap-region id 2
ap-region-name floor2
ap id 101 type-id 38 mac 00e0-fc76-e320
region-id 1
lineate-port ethernet 0 pvid vlan 201
lineate-port ethernet 0 vlan untagged 201
lineate-port ethernet 1 pvid vlan 201
lineate-port ethernet 1 vlan untagged 201
lineate-port gigabitethernet 0 vlan tagged 201
ap id 102 type-id 38 mac 00e0-fc76-e340
region-id 1
lineate-port ethernet 0 pvid vlan 201
lineate-port ethernet 0 vlan untagged 201
lineate-port ethernet 1 pvid vlan 201
lineate-port ethernet 1 vlan untagged 201
lineate-port gigabitethernet 0 vlan tagged 201
ap id 103 type-id 35 mac 00e0-fc04-b520
region-id 1
ap id 201 type-id 38 mac 00e0-fc76-e360
region-id 2
lineate-port ethernet 0 pvid vlan 202
lineate-port ethernet 0 vlan untagged 202
lineate-port ethernet 1 pvid vlan 202
lineate-port ethernet 1 vlan untagged 202
lineate-port gigabitethernet 0 vlan tagged 202
ap id 202 type-id 38 mac 00e0-fc76-e380
region-id 2
lineate-port ethernet 0 pvid vlan 202
lineate-port ethernet 0 vlan untagged 202
lineate-port ethernet 1 pvid vlan 202
lineate-port ethernet 1 vlan untagged 202
lineate-port gigabitethernet 0 vlan tagged 202
ap id 203 type-id 35 mac 00e0-fc04-b540
region-id 2
wmm-profile name wmm id 1
traffic-profile name traffic id 1
security-profile name security id 1
service-set name floor1 id 1
forward-mode tunnel
wlan-ess 1
ssid hospital-wlan
user-isolate
traffic-profile id 1
security-profile id 1
service-vlan 101
service-set name floor2 id 2
forward-mode tunnel
wlan-ess 2
ssid hospital-wlan
user-isolate
traffic-profile id 1
security-profile id 1
service-vlan 102
radio-profile name radio id 1
channel-mode fixed
power-mode fixed
wmm-profile id 1
ap 101 radio 0
radio-profile id 1
power-level 10
service-set id 1 wlan 1
ap 102 radio 0
radio-profile id 1
channel 20MHz 6
power-level 10
service-set id 1 wlan 1
ap 103 radio 0
radio-profile id 1
channel 20MHz 11
power-level 10
service-set id 1 wlan 1
ap 103 radio 1
radio-profile id 1
channel 20MHz 153
power-level 10
service-set id 1 wlan 1
ap 201 radio 0
radio-profile id 1
power-level 10
service-set id 2 wlan 1
ap 202 radio 0
radio-profile id 1
channel 20MHz 6
power-level 10
service-set id 2 wlan 1
ap 203 radio 0
radio-profile id 1
channel 20MHz 11
power-level 10
service-set id 2 wlan 1
ap 203 radio 1
radio-profile id 1
channel 20MHz 157
power-level 10
service-set id 2 wlan 1
#
return
相关文章