Ubuntu安装
先打开VMware
再新建虚拟机
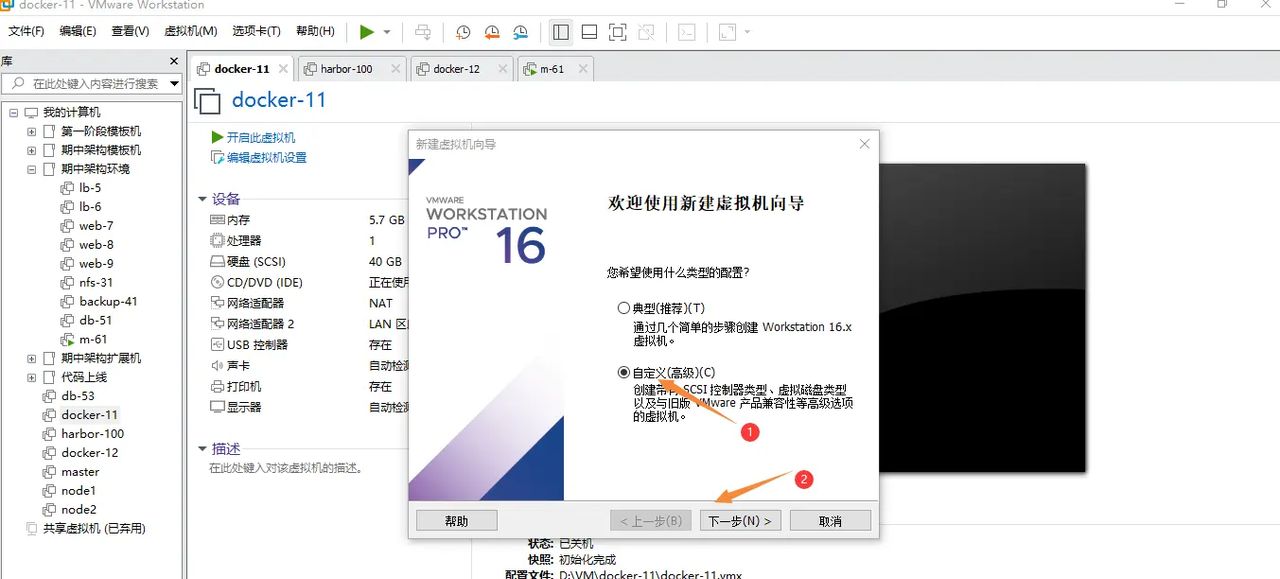
选择自定义—下一步
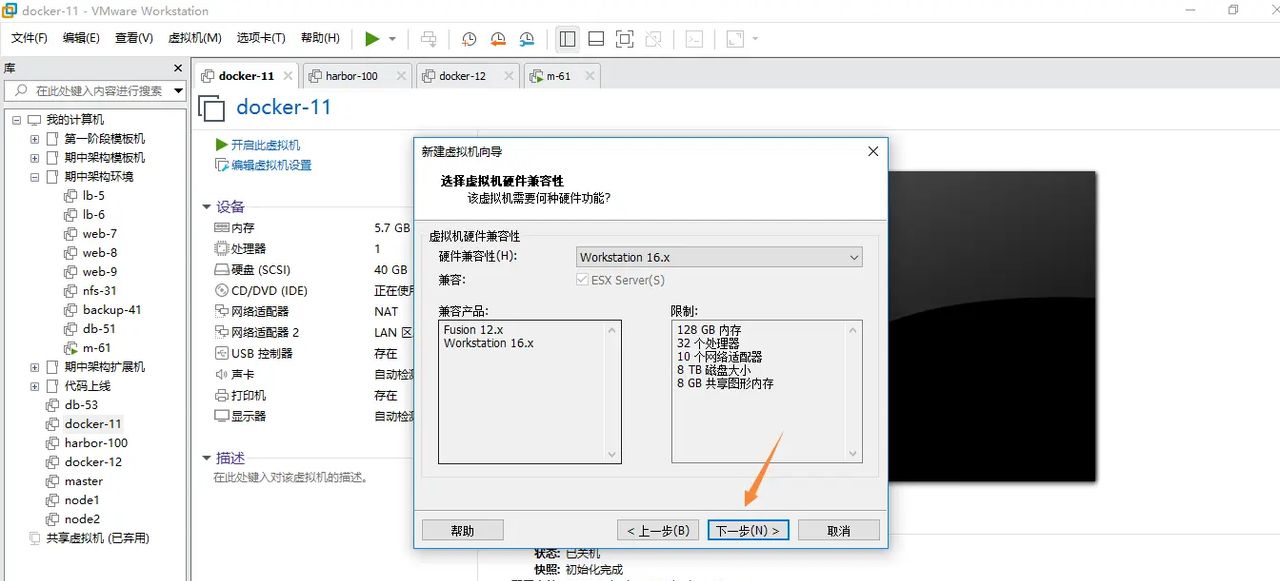
下一步
选择稍后安装
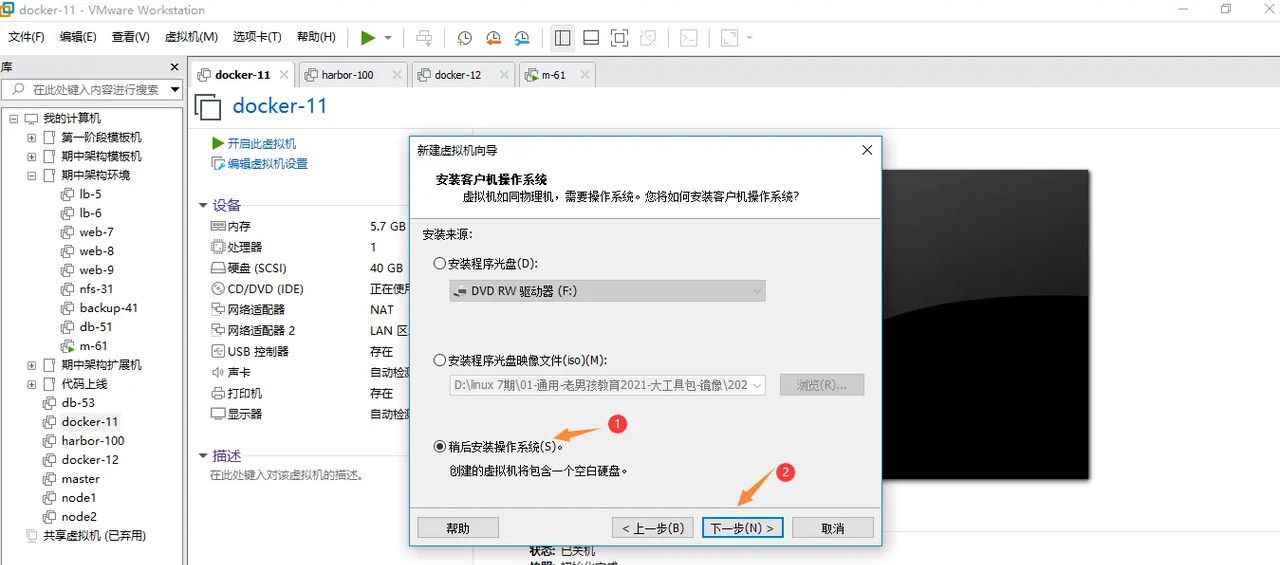
选择安装系统情况
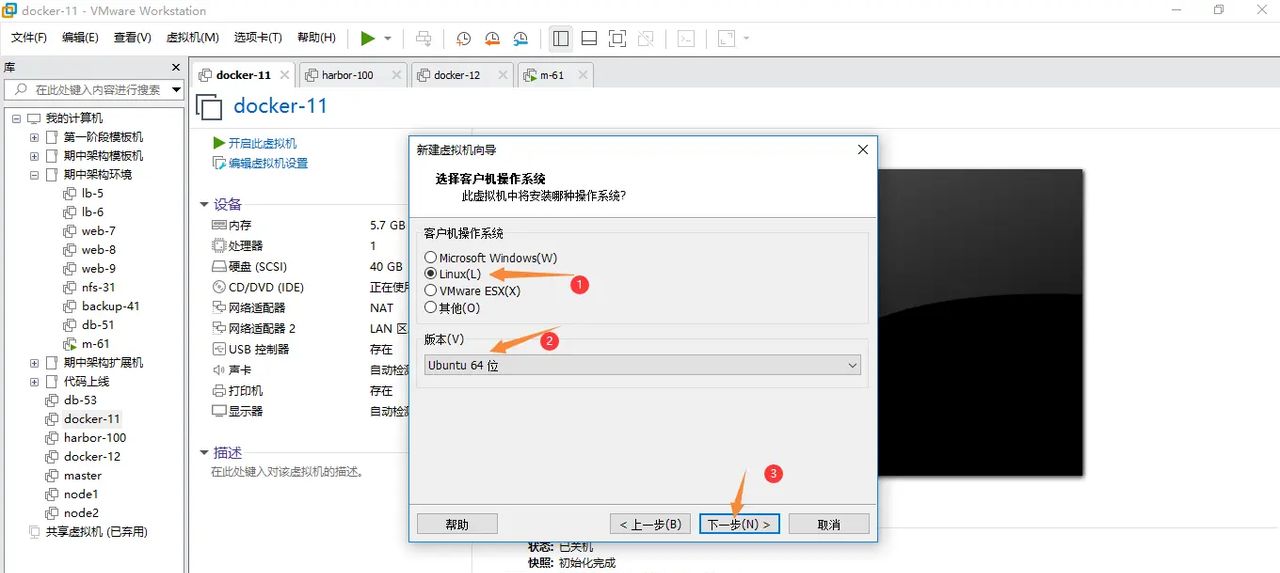
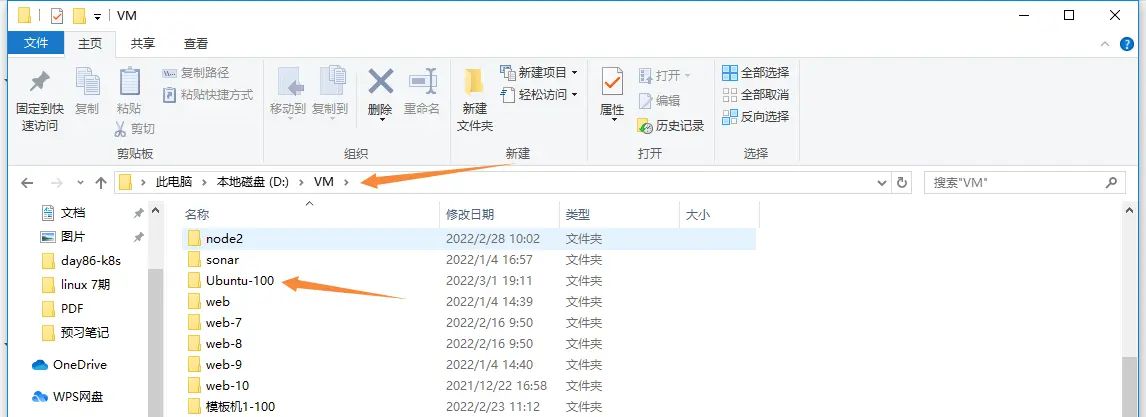
新建一个文件夹存储安装ubuntu
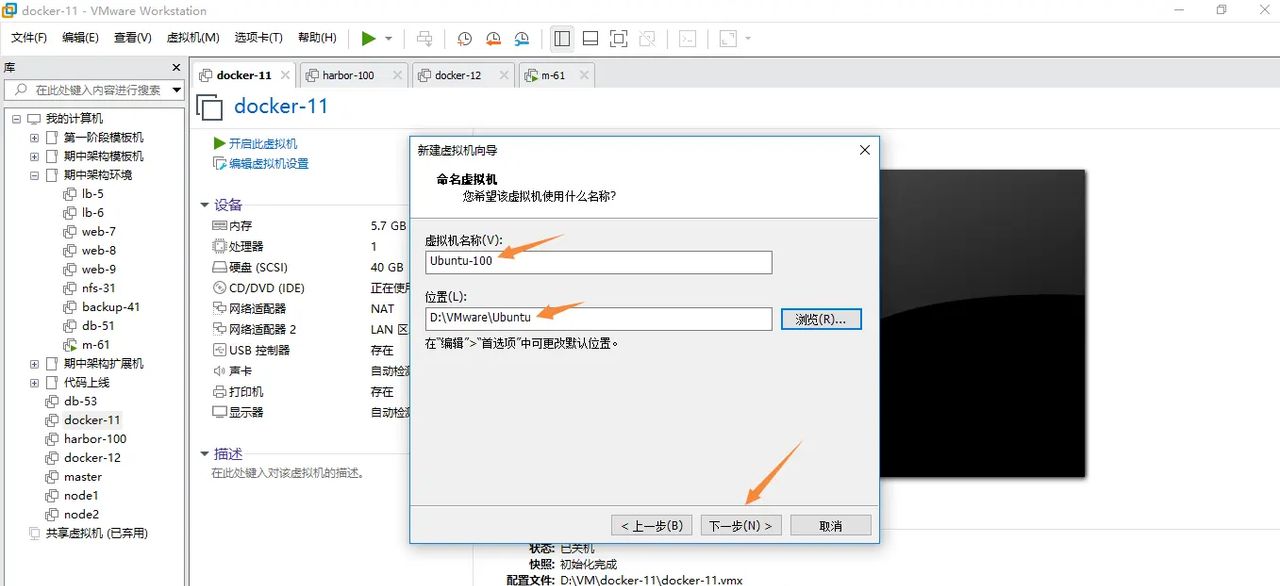
修改虚拟机名称,并选择虚拟机安装位置
选择处理器数量
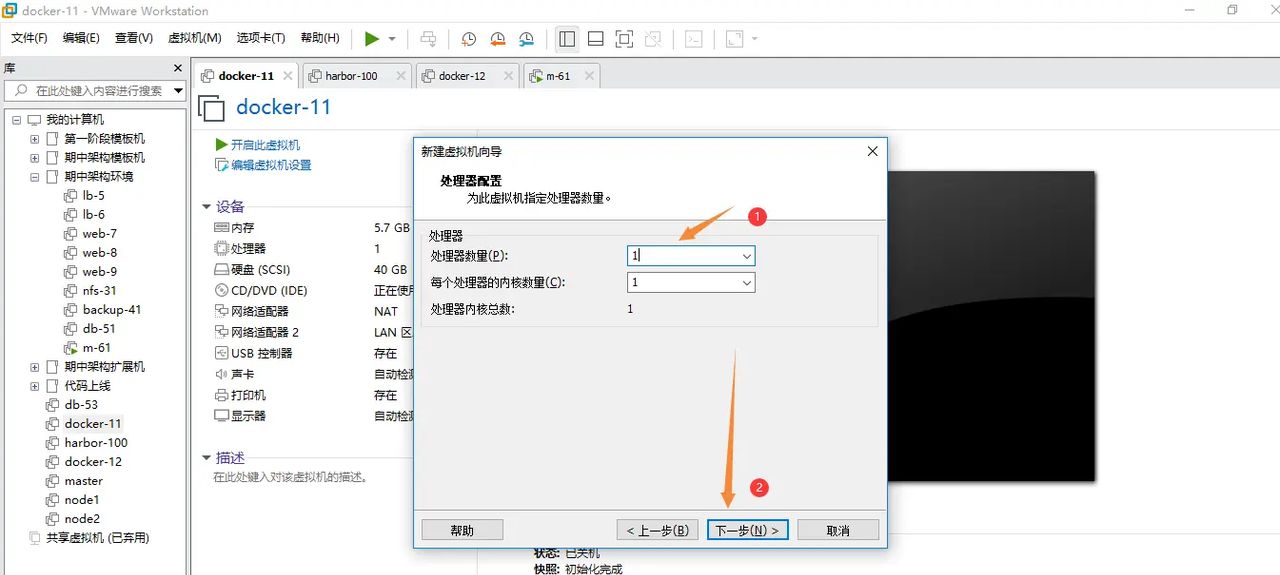
内存设置为2G
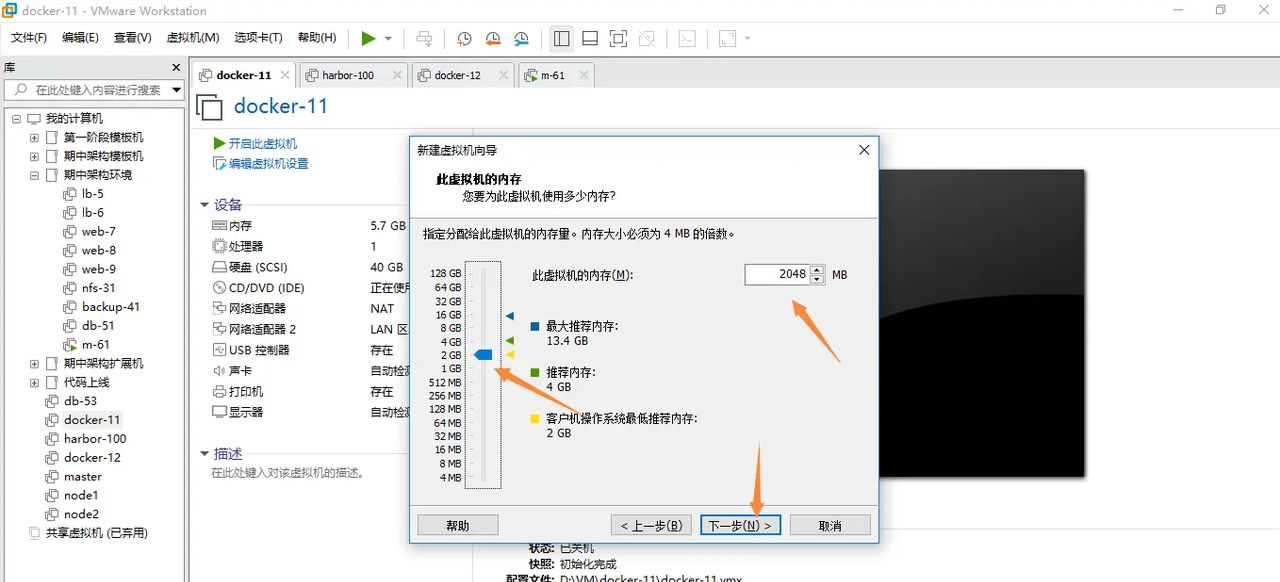
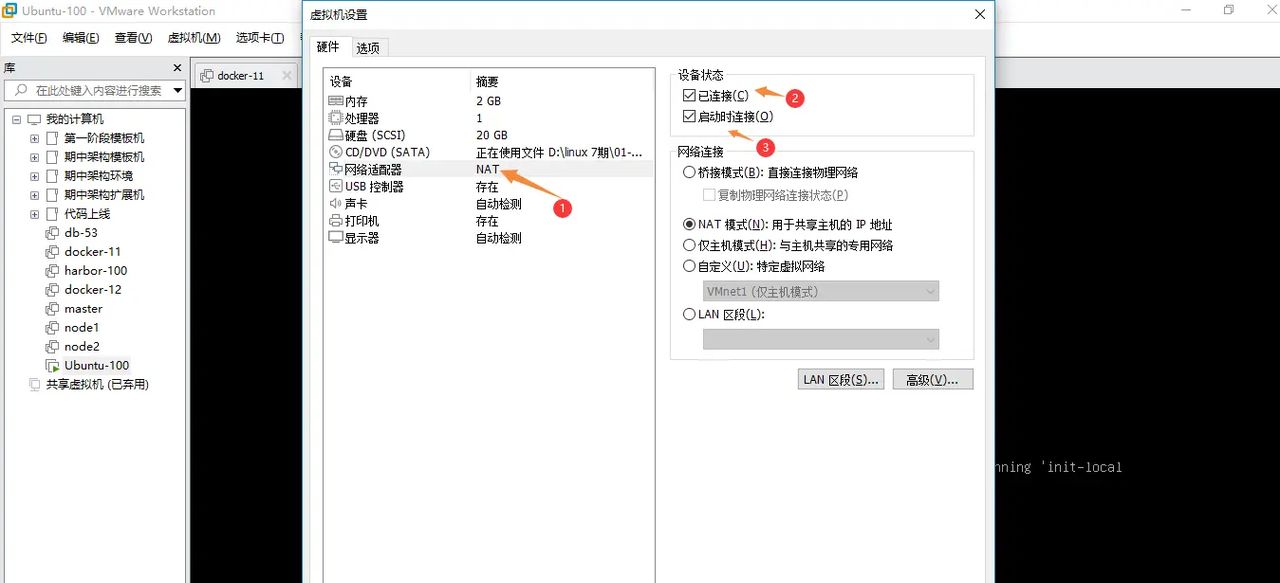
设置网络
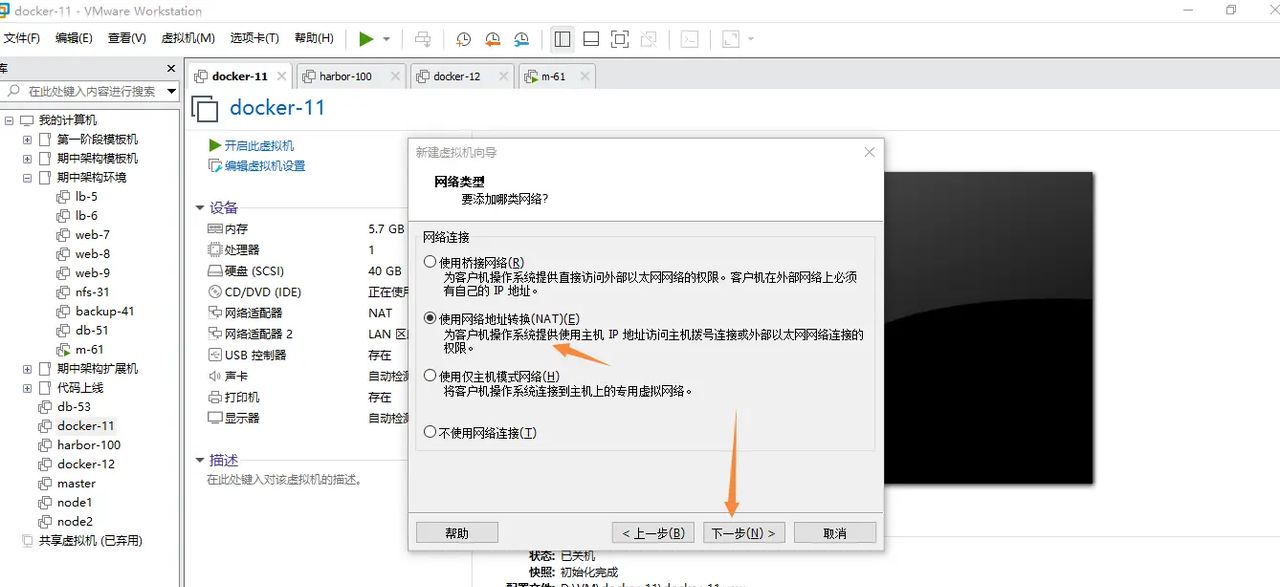
选择i/o控制器
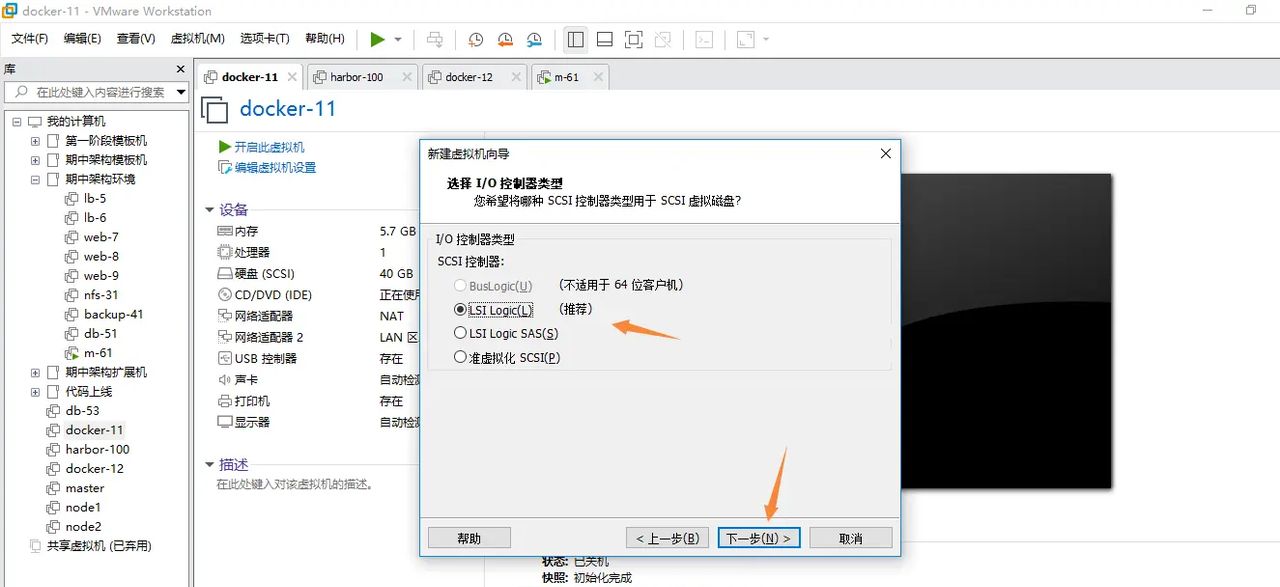
选择磁盘类型
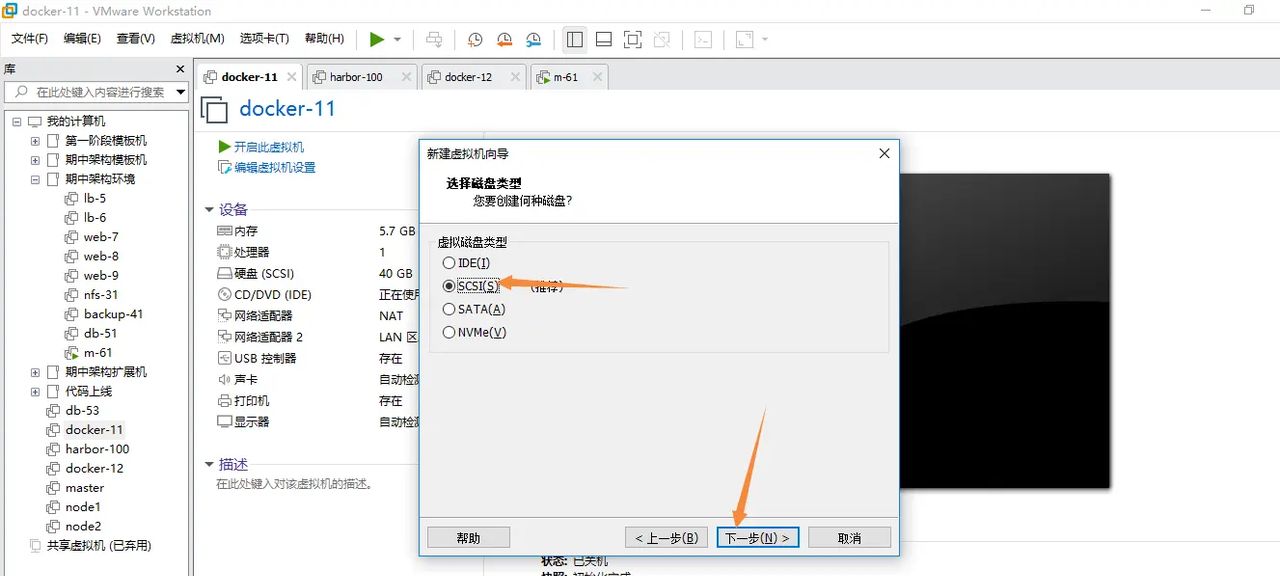
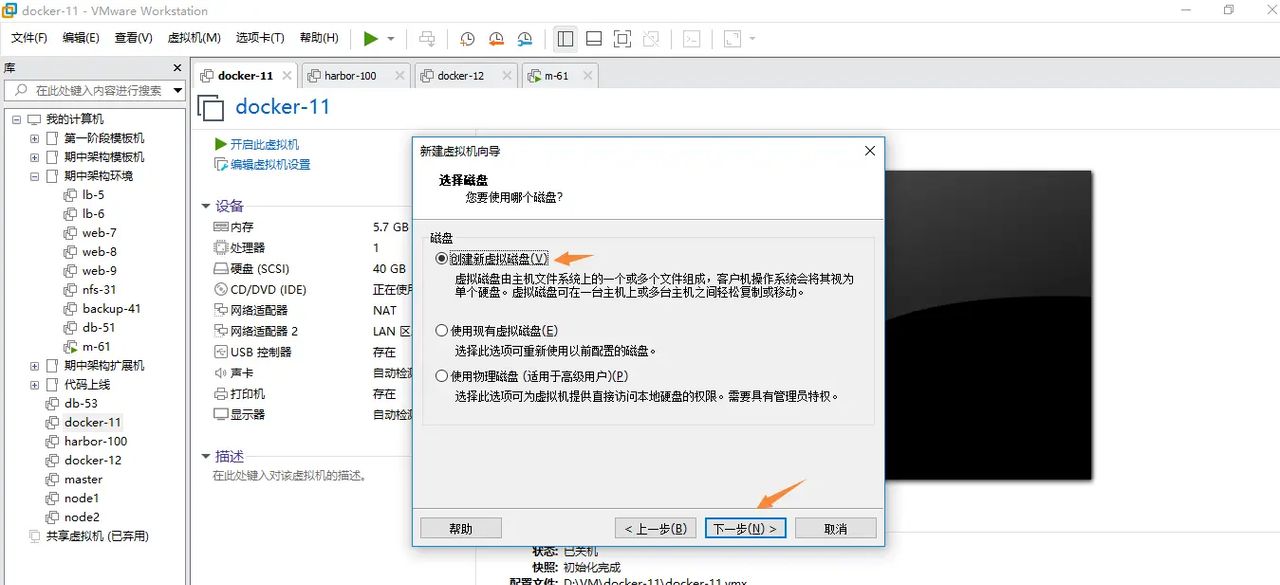
选择磁盘–创建新磁盘
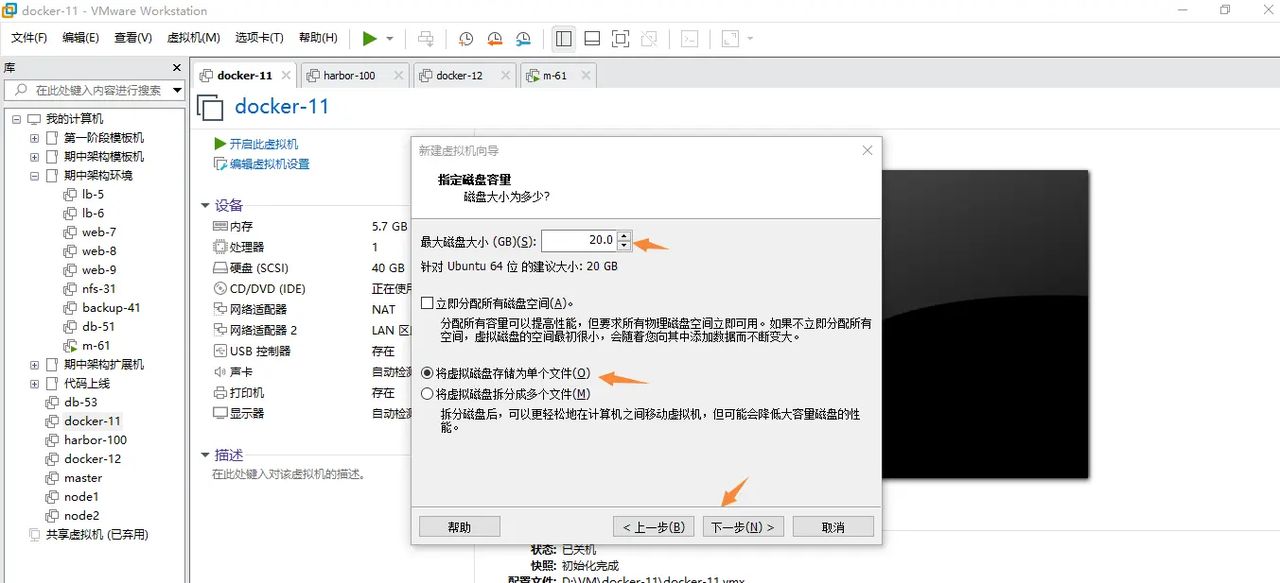
指定磁盘容量-选择单个文件
下一步
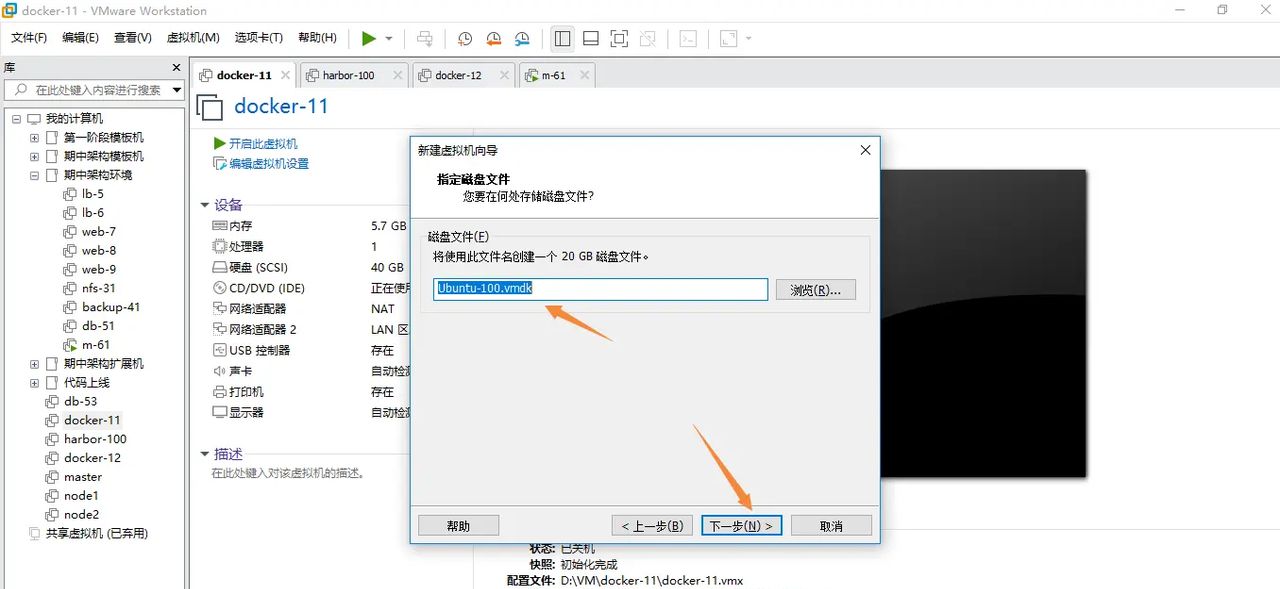
点击完成
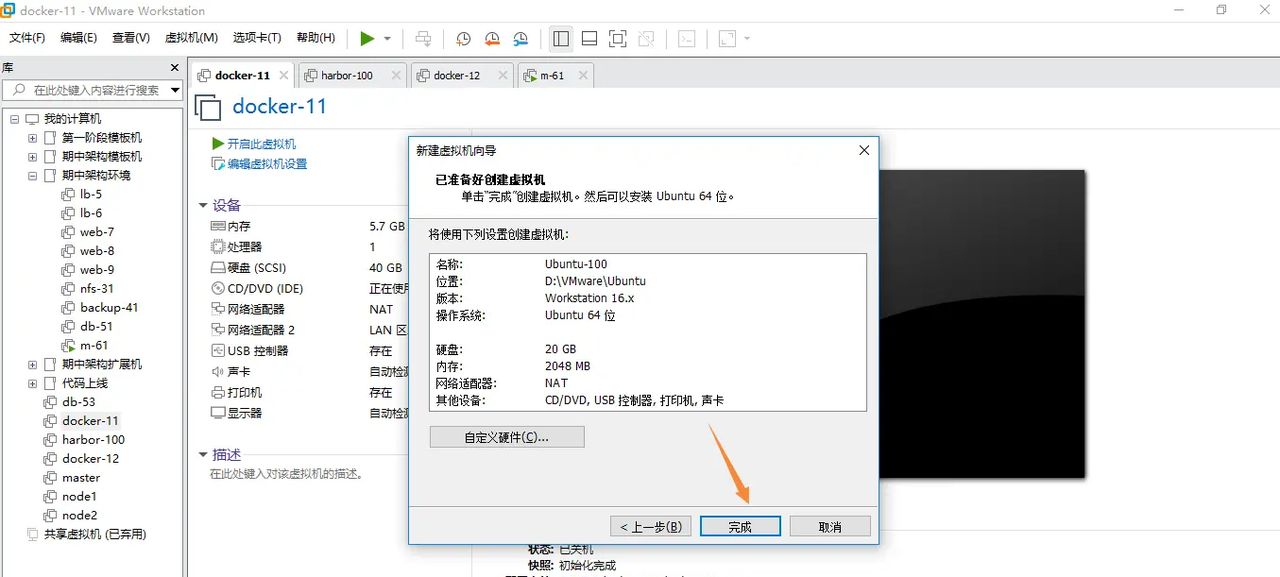
虚拟机创建完成
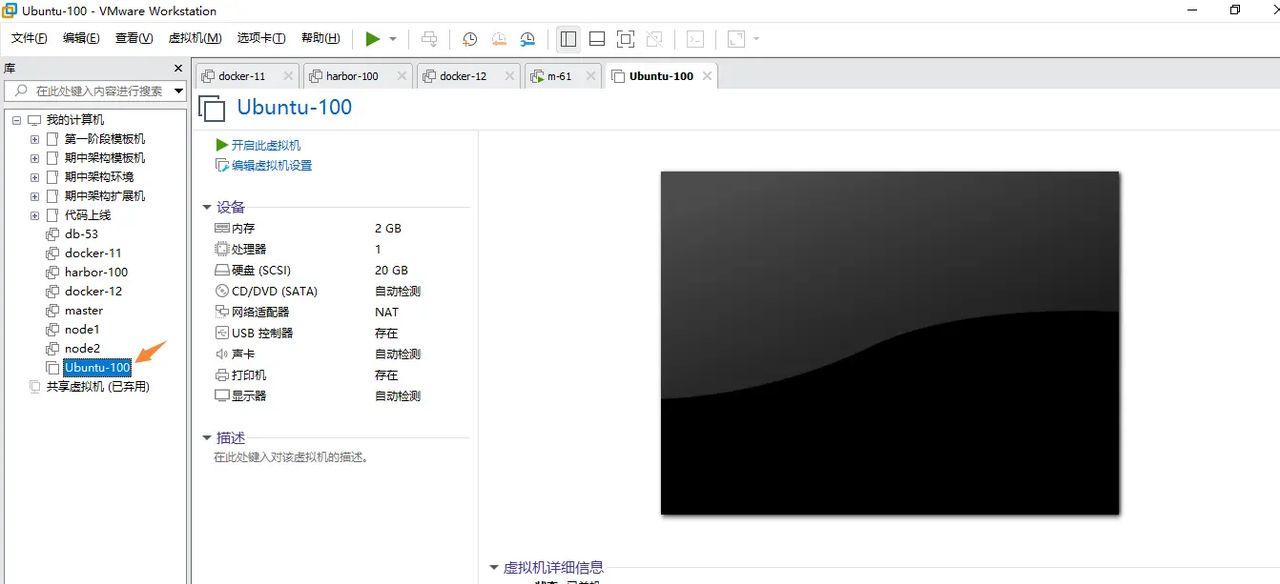
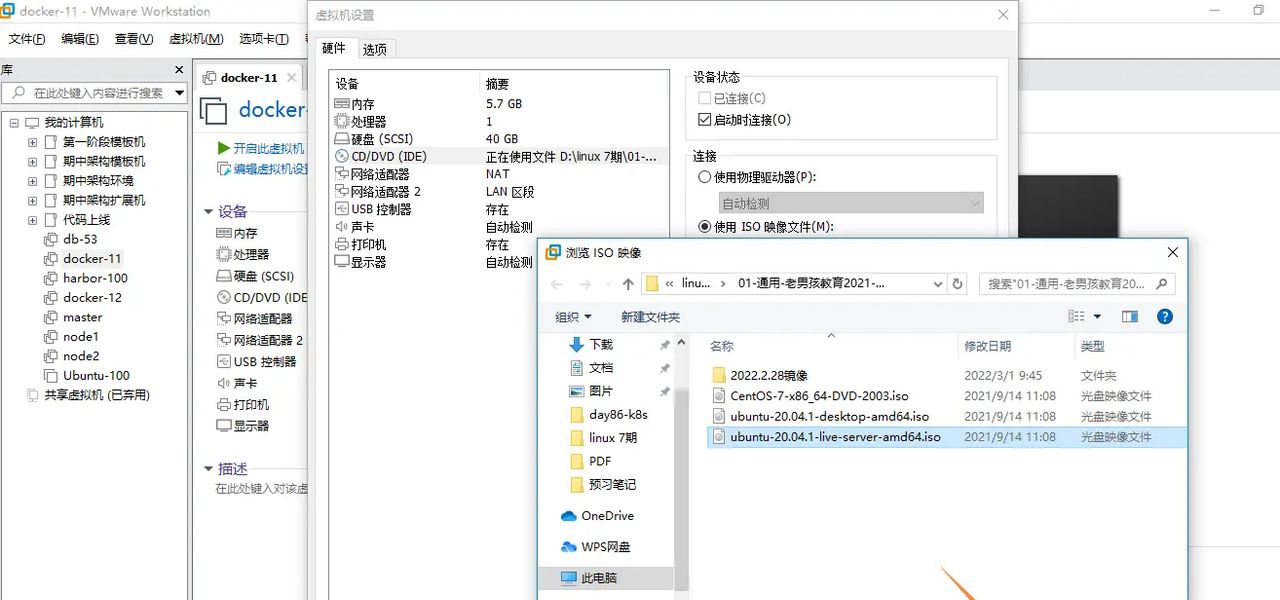
选择Ubuntu镜像
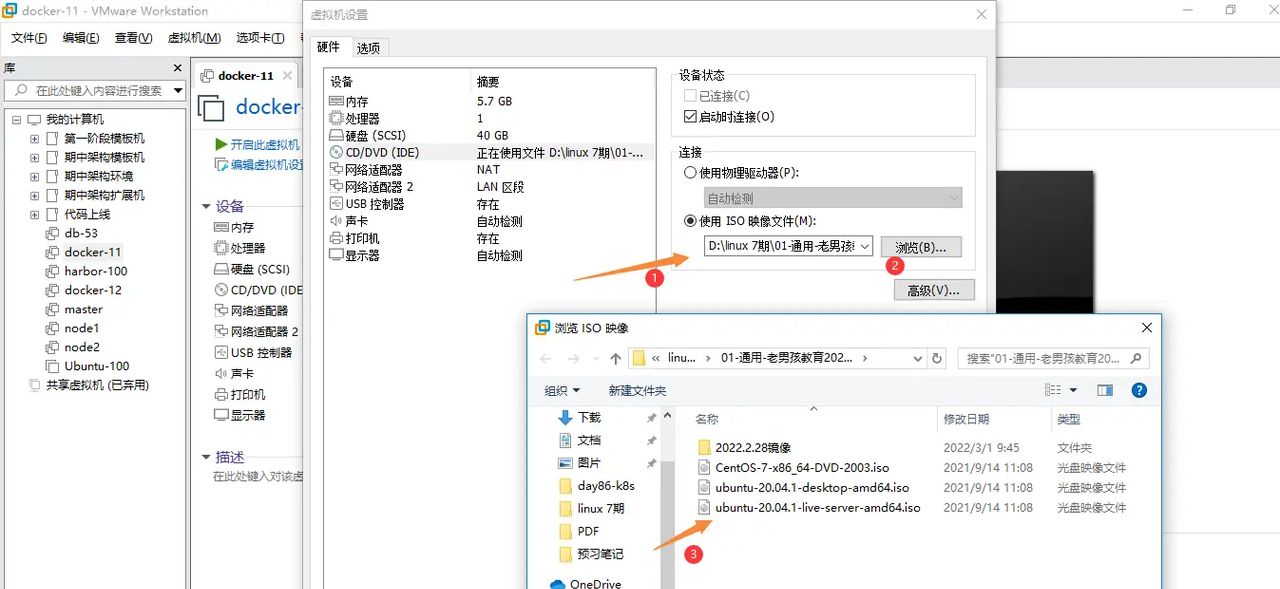
打开
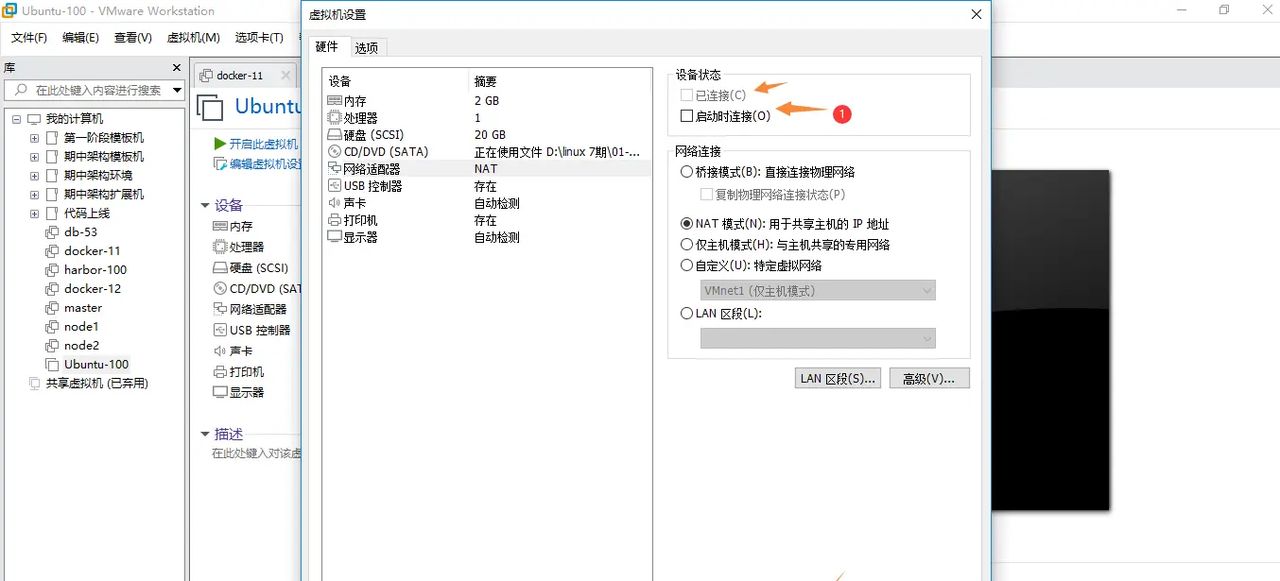
注意:要关闭网络连接,不然它会自动连接网络,会下载安装会很慢
修改网卡名称为eth0
开机出现logo后按f5键,然后按esc键,下方会出现boot的内容,添加如下内容即可修改网卡名称为传统的eth0,修改完后按回车键
net.ifnames=0 biosdevname=0
出现Ubuntu的logo,按f5,出现下面界面为准
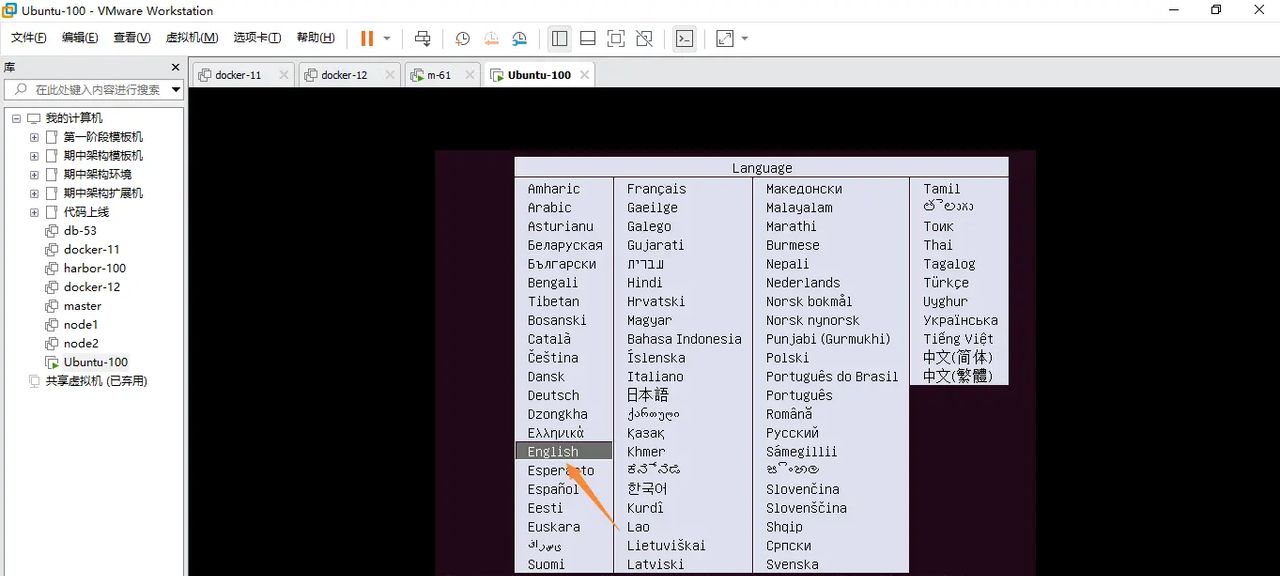
选择English回车
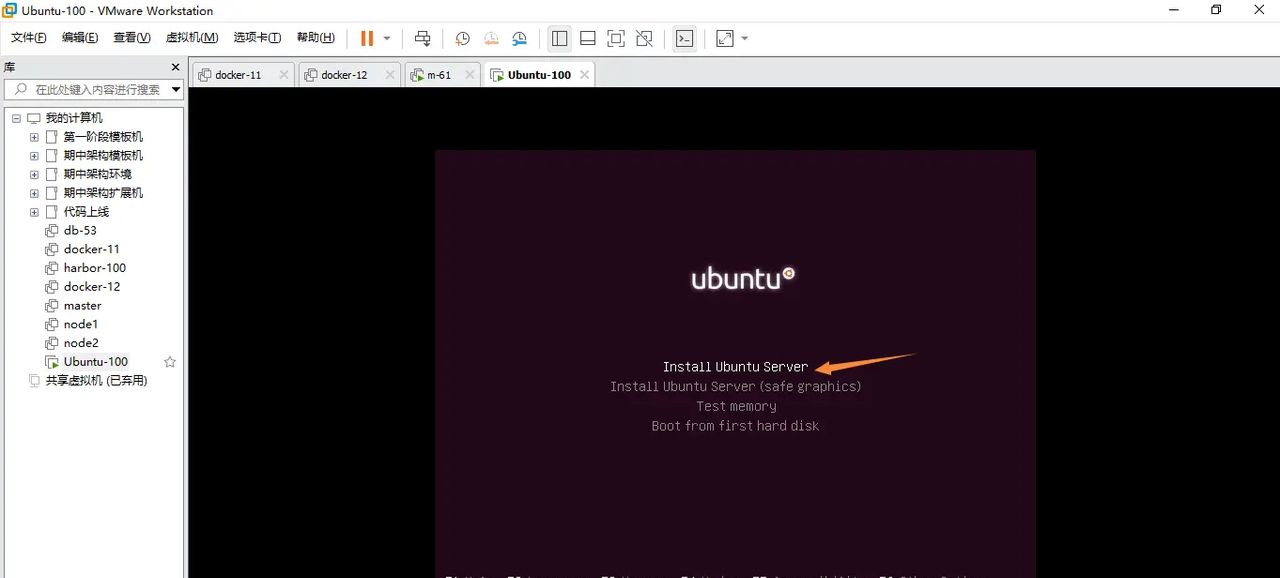
方向键选择第一个后,立即按f6,出现小菜单后
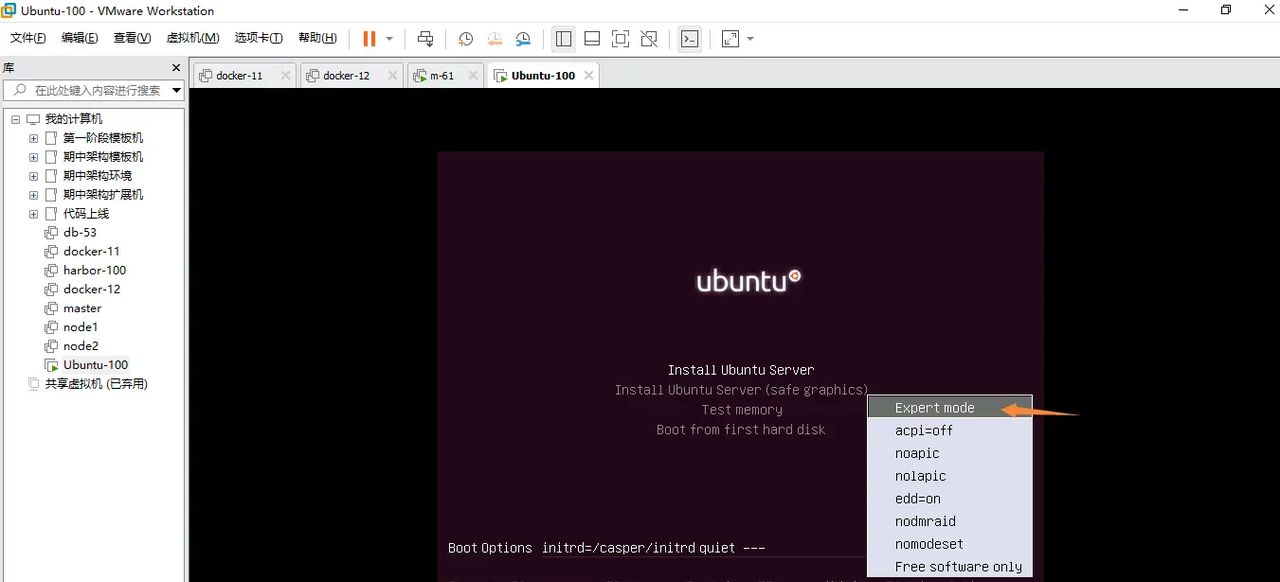
立即按电脑esc键 ,再修改网络
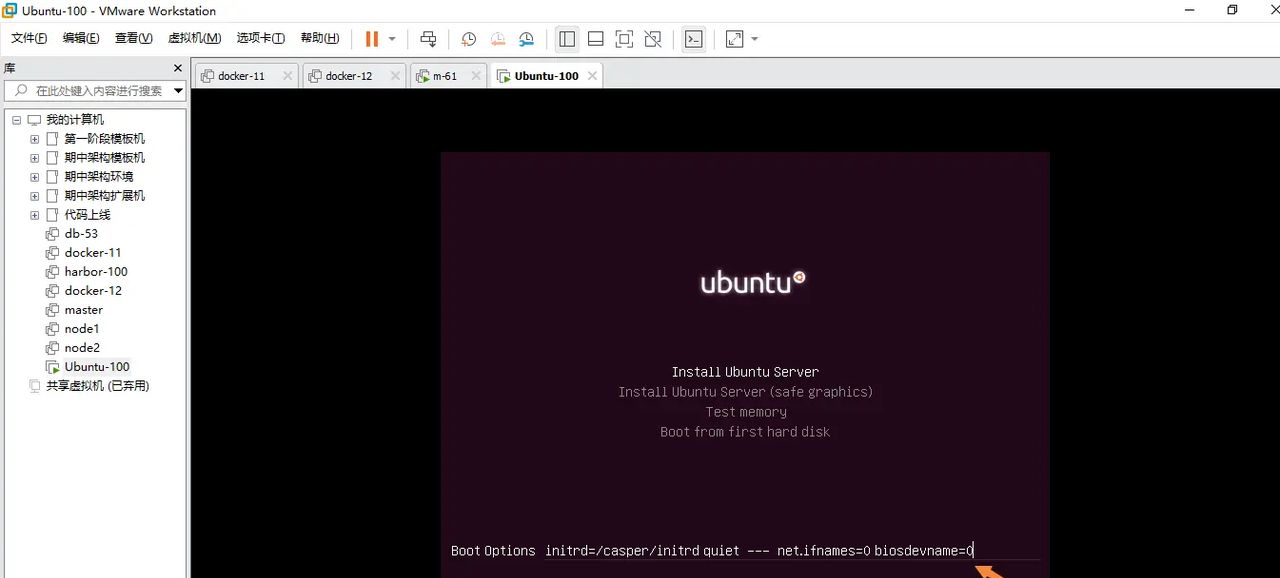
可以使用vmware粘贴命令
修改后,按回车

再次回车,出现下列界面,选择English
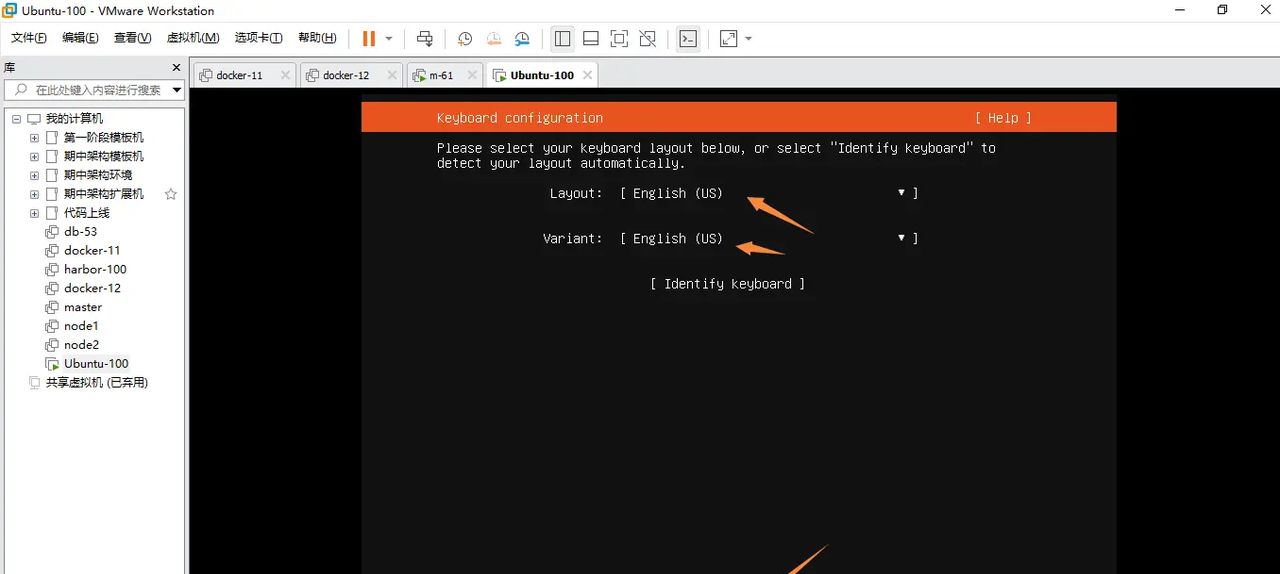
选择英文键盘
修改网络
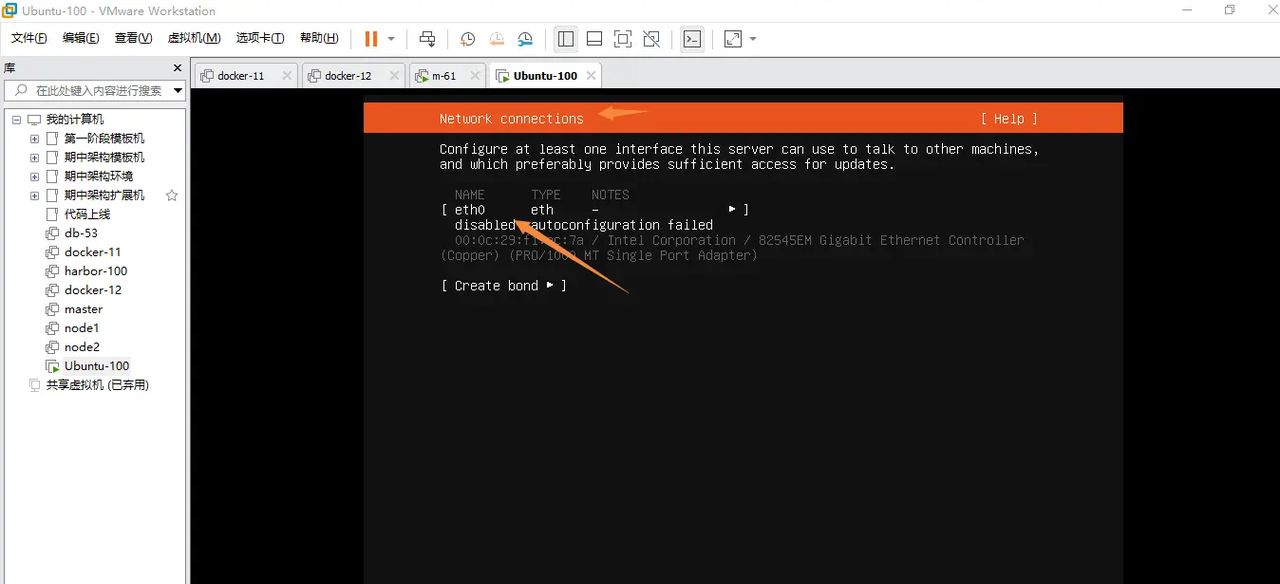
选择ipv4修改网络
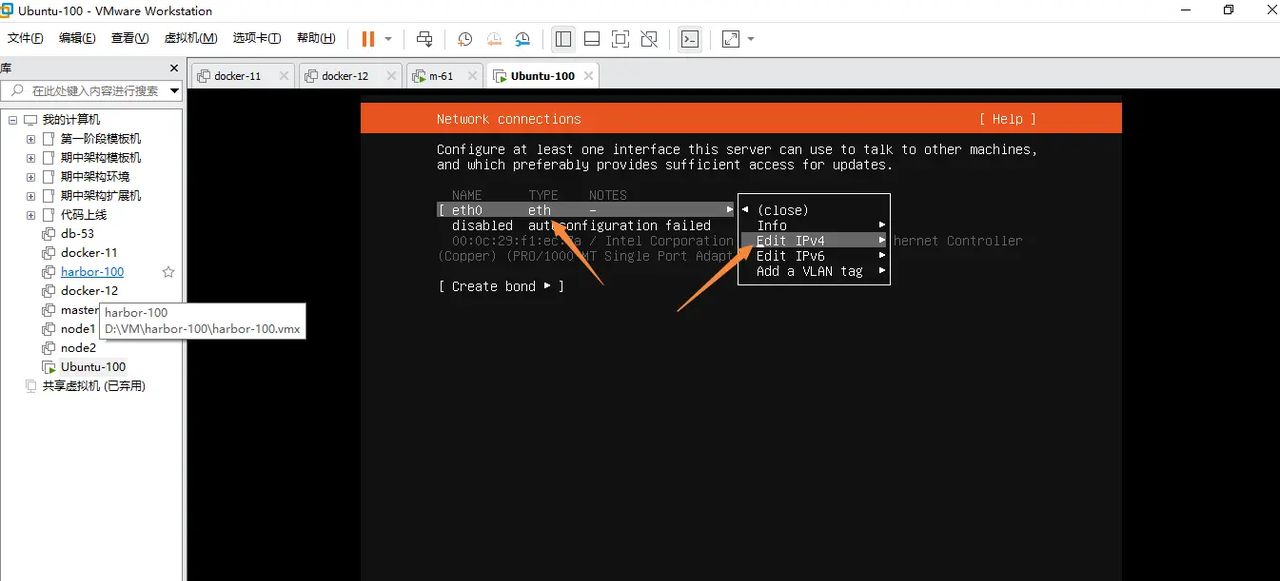
选择Manual,即自定义模式
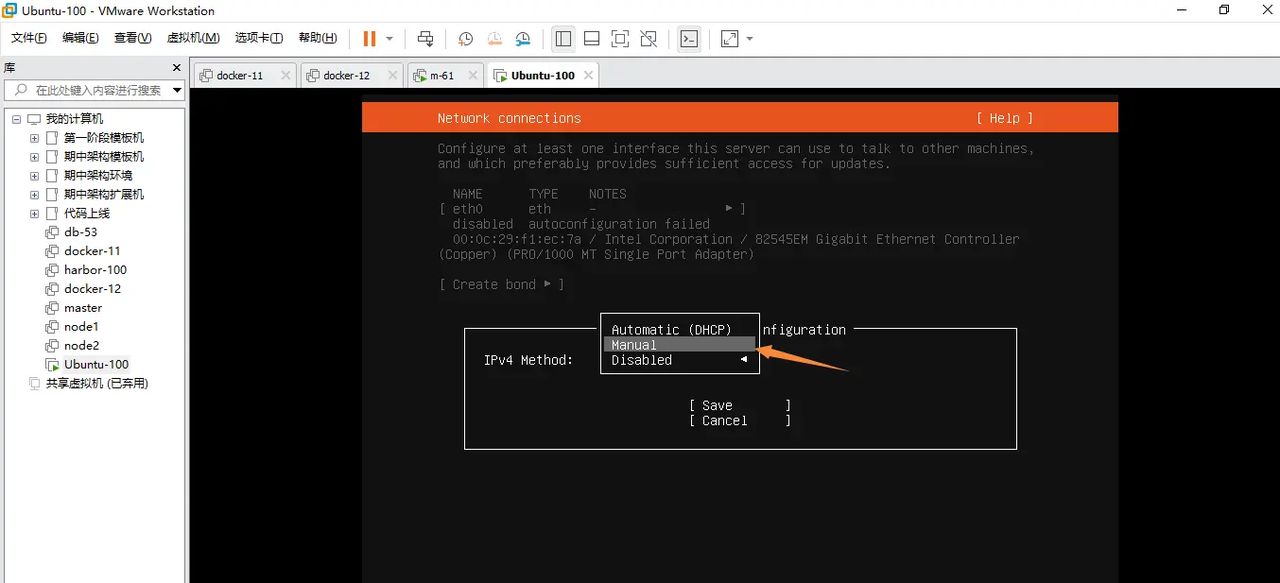
修改以下这样保存
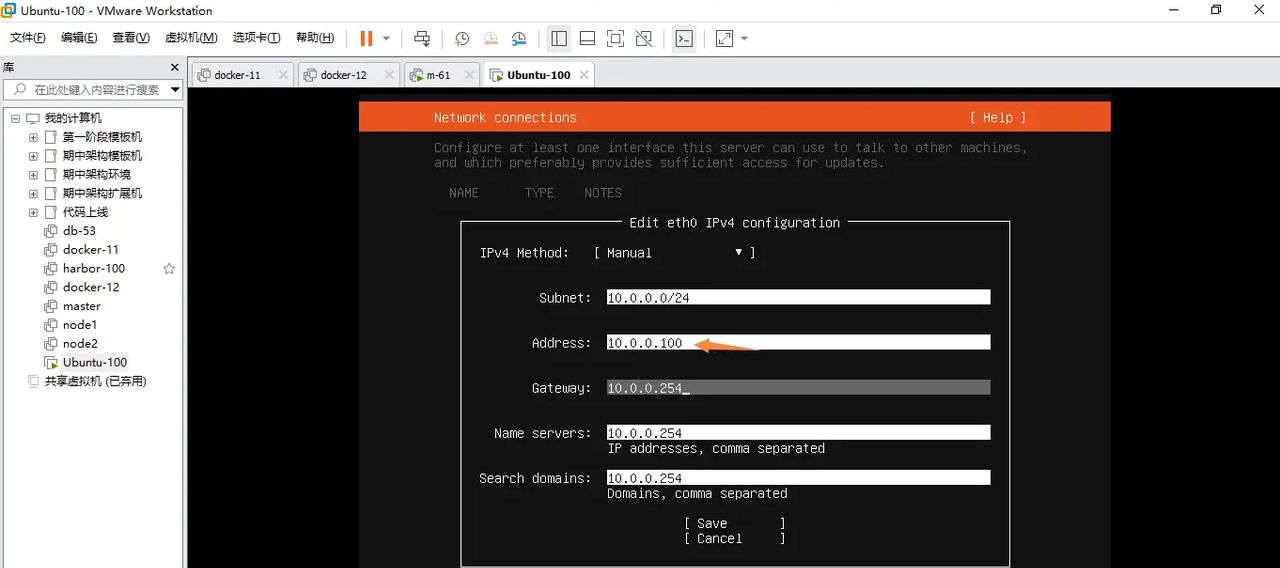
选择在没有网络的情况下继续
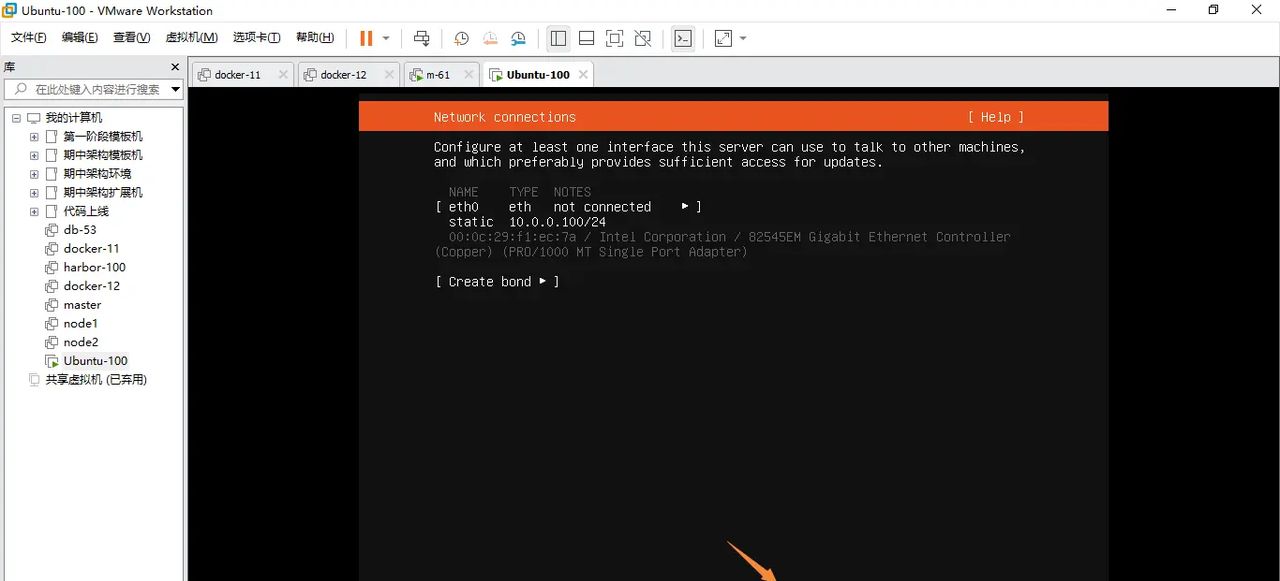
代理设置为空,继续
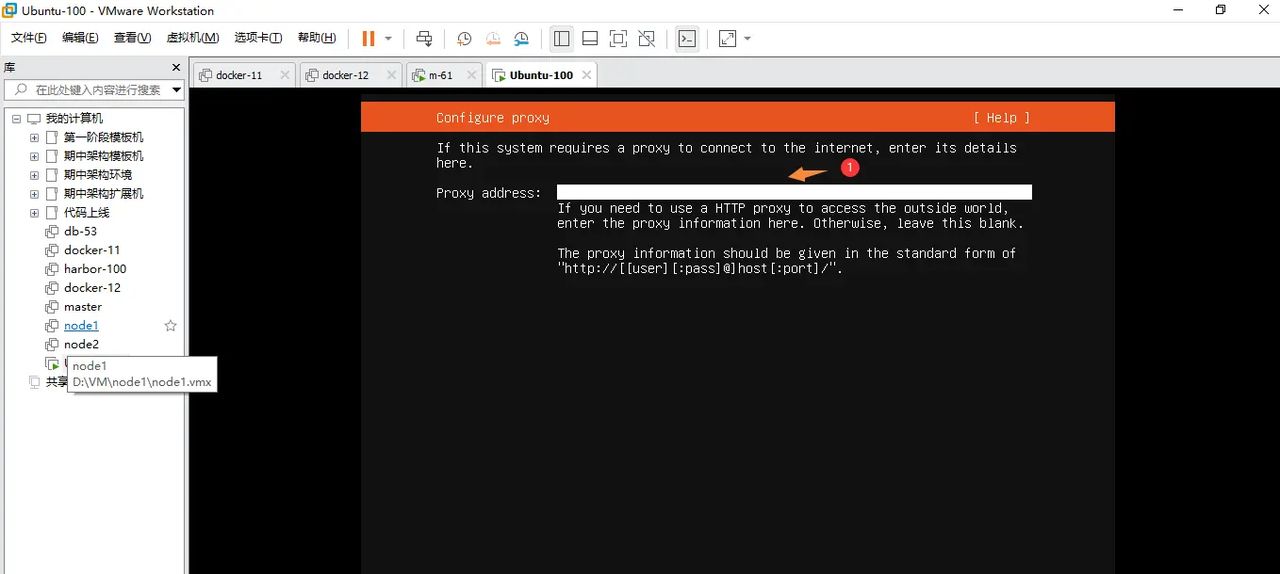
仓库地址先默认
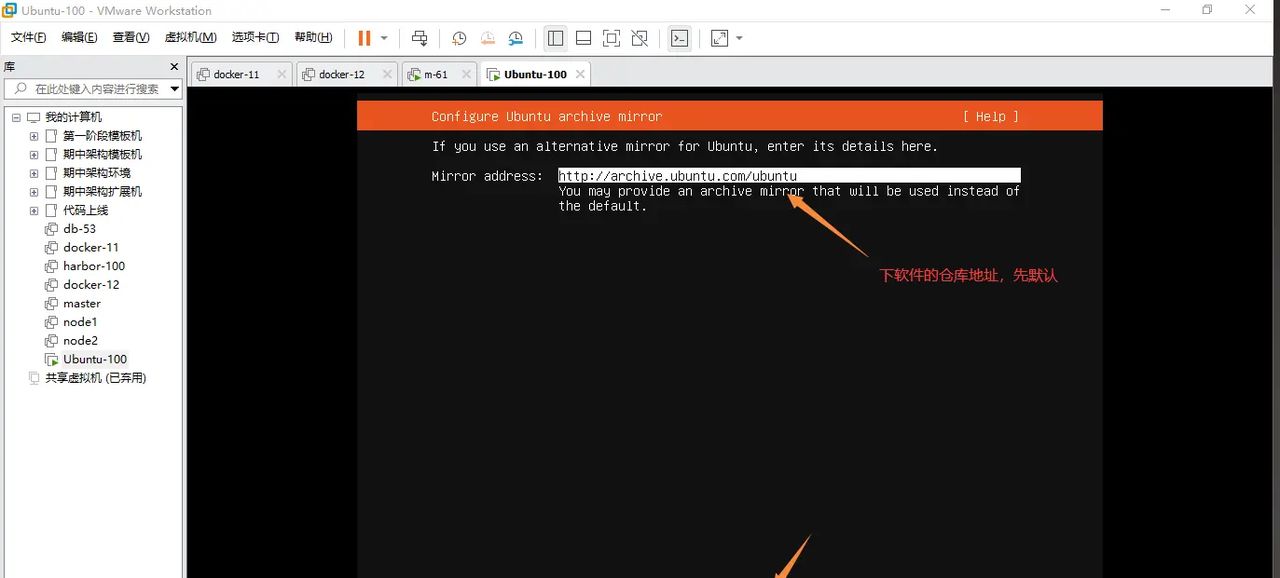
下一步选择
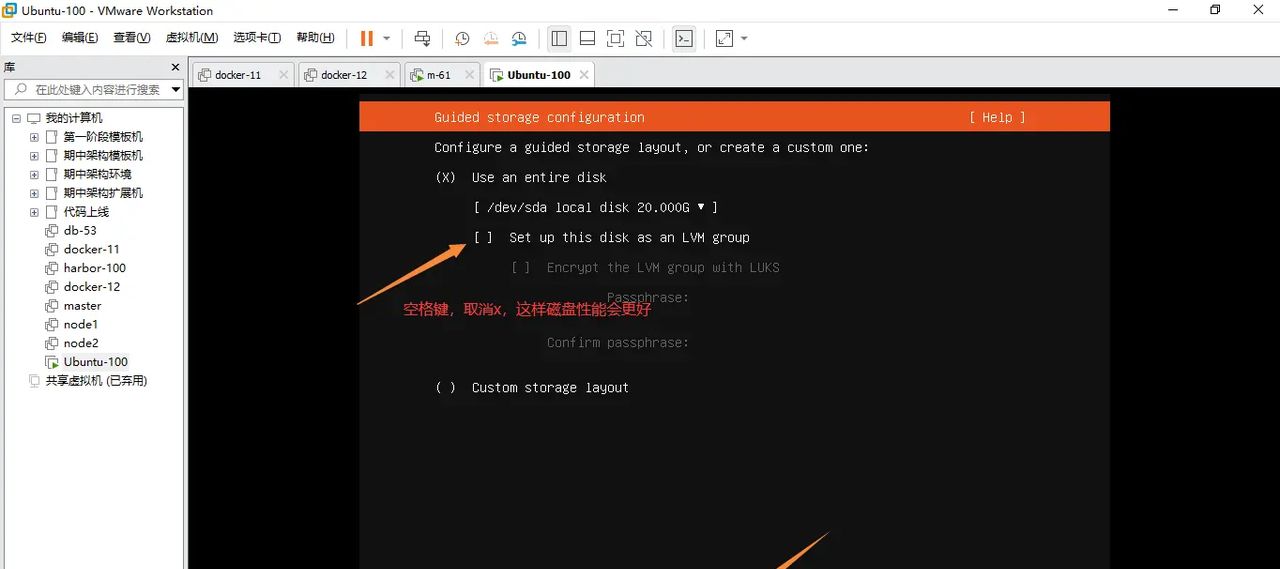
下一步,使用一块磁盘,不分区
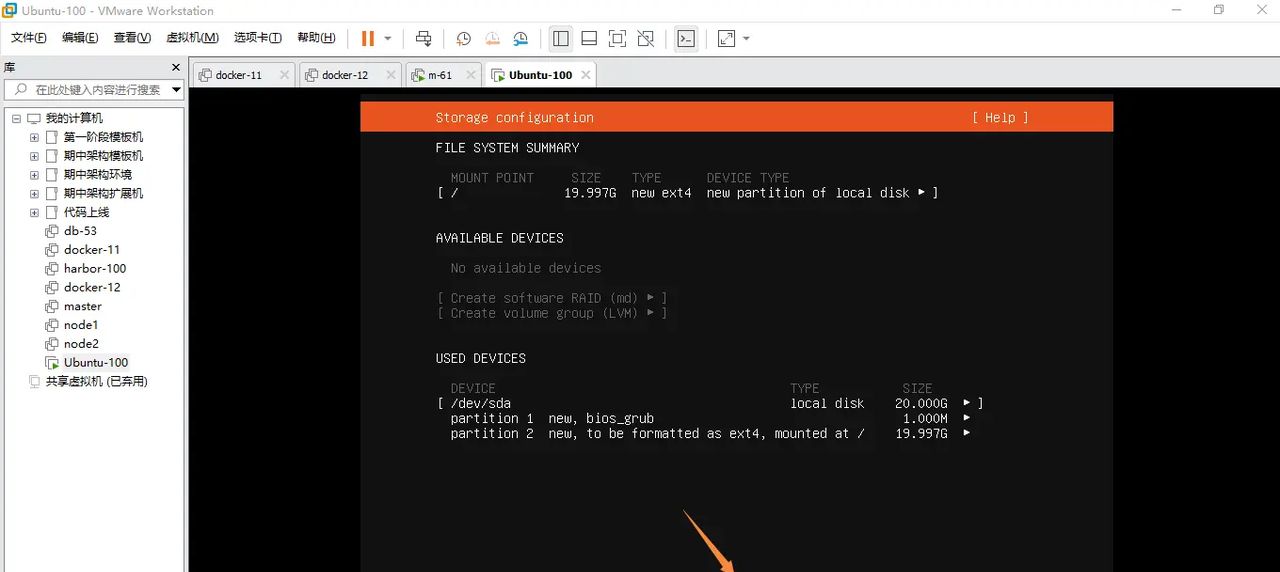
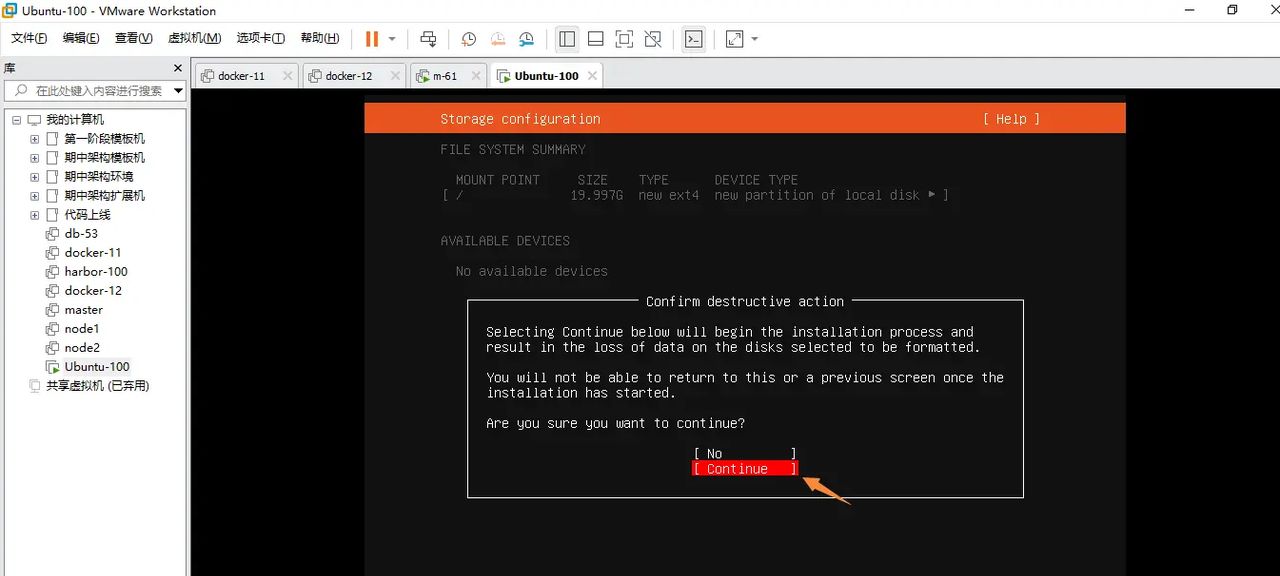
警告不用管,继续
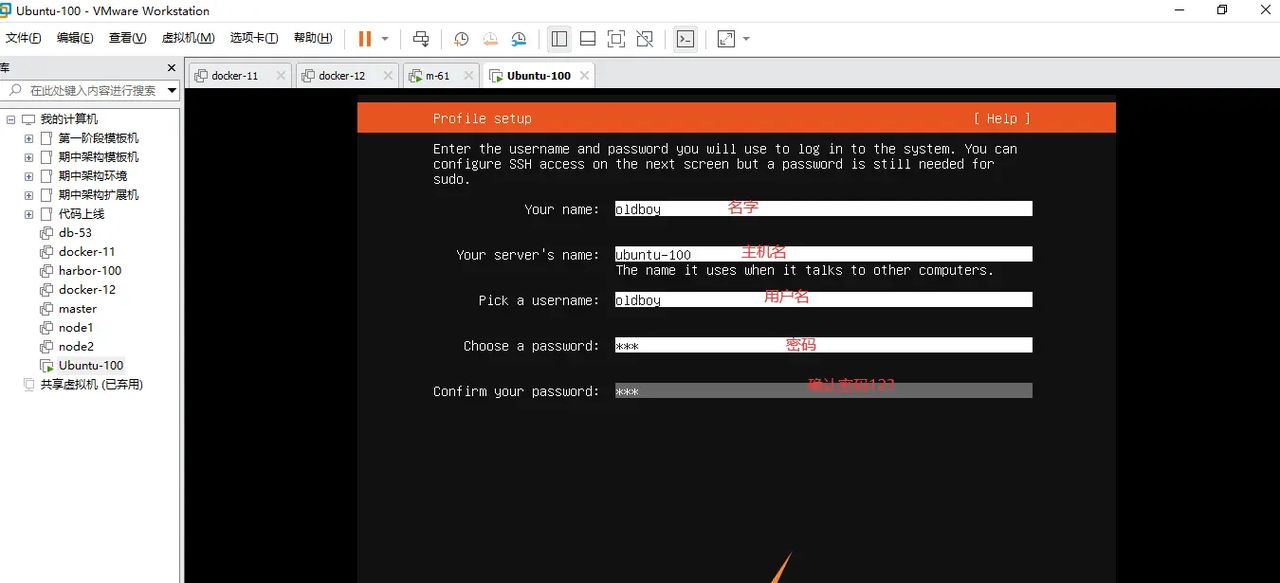
修改账号密码等
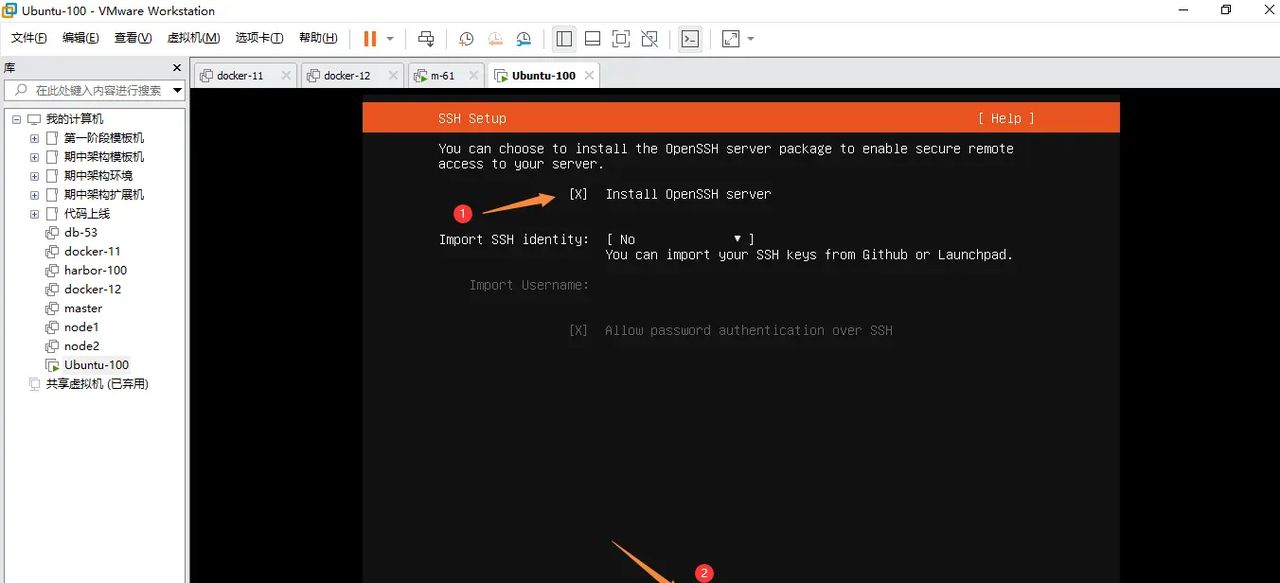
系统安装ssh,保证系统有ssh等会xshell可以连接上
等待一会,选择reboot now
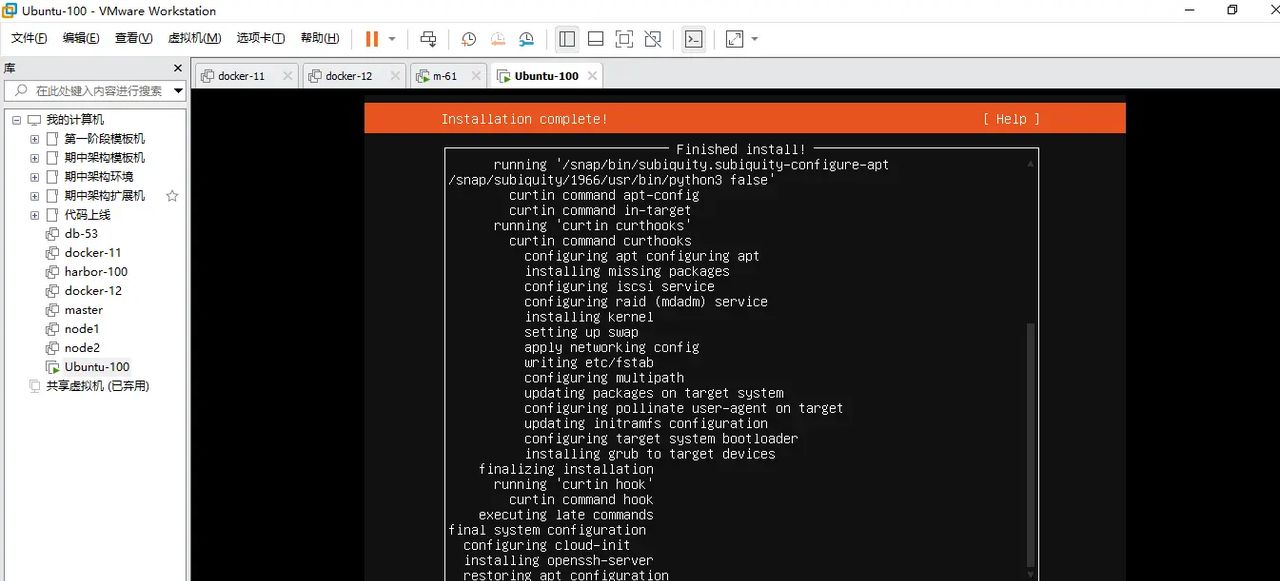
正在启动
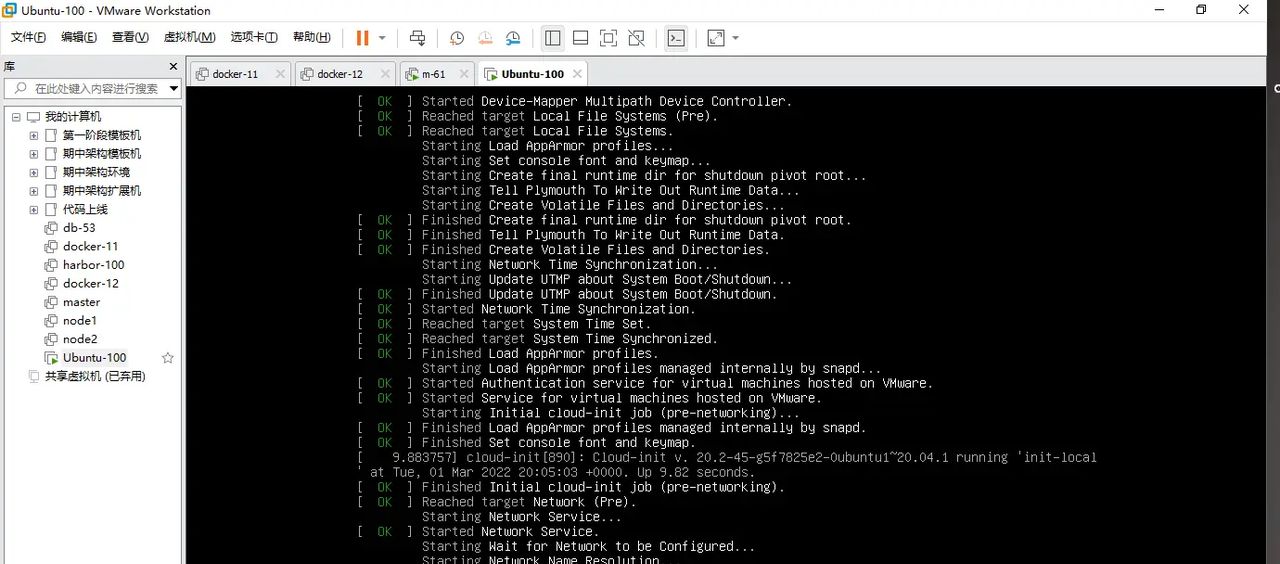
目前可以把网络打开,让它起来
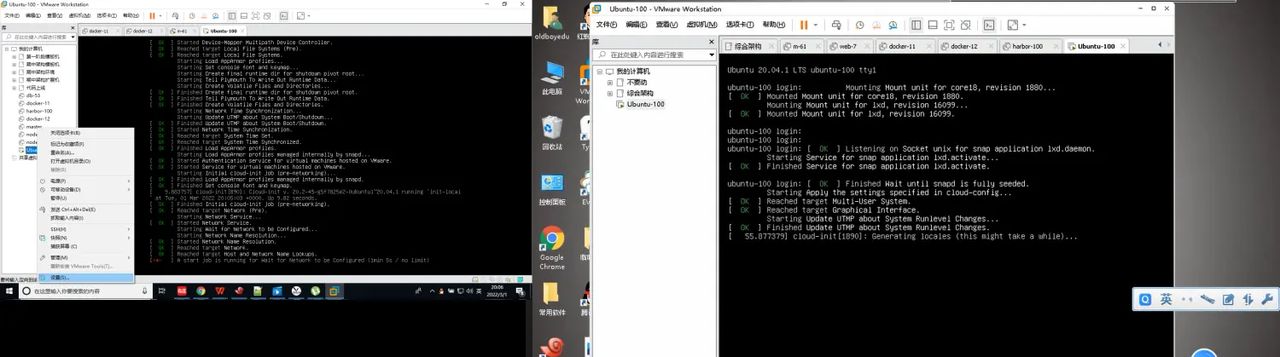
开机中
登录
登录成功
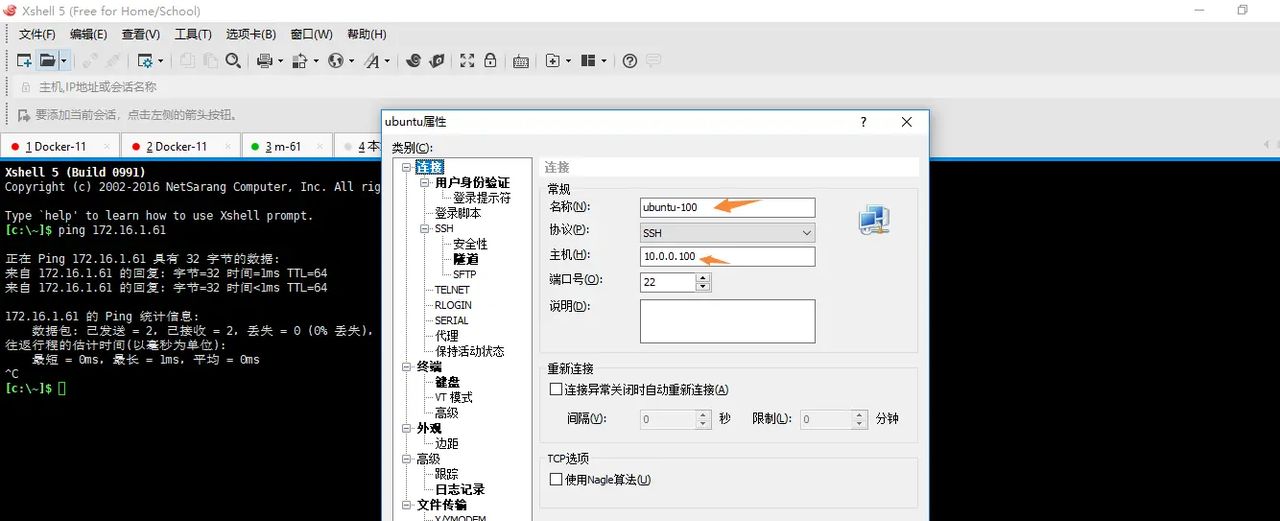
配置xshell连接Ubuntu
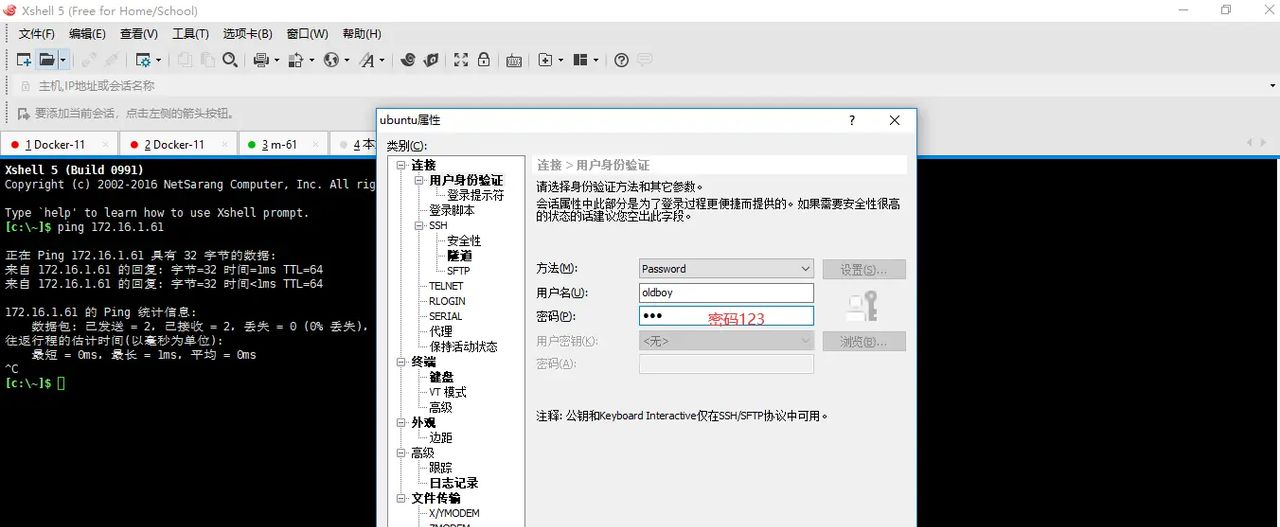
设置root密码为123

切换root用户登录
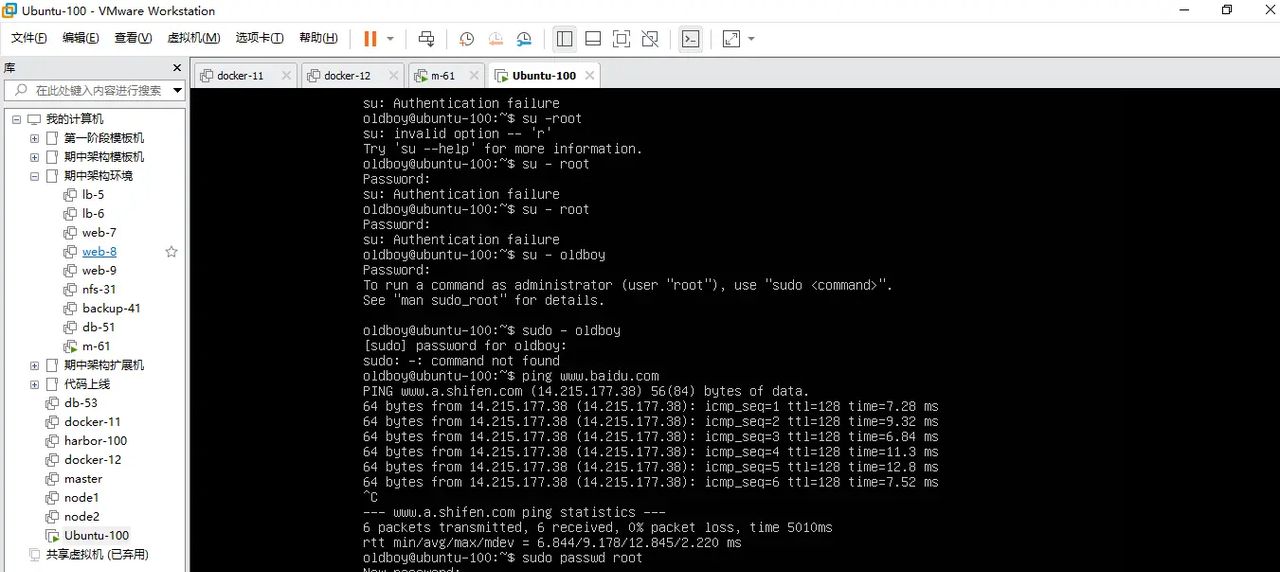
给普通用户修改密码
先登录root用户
再修改密码
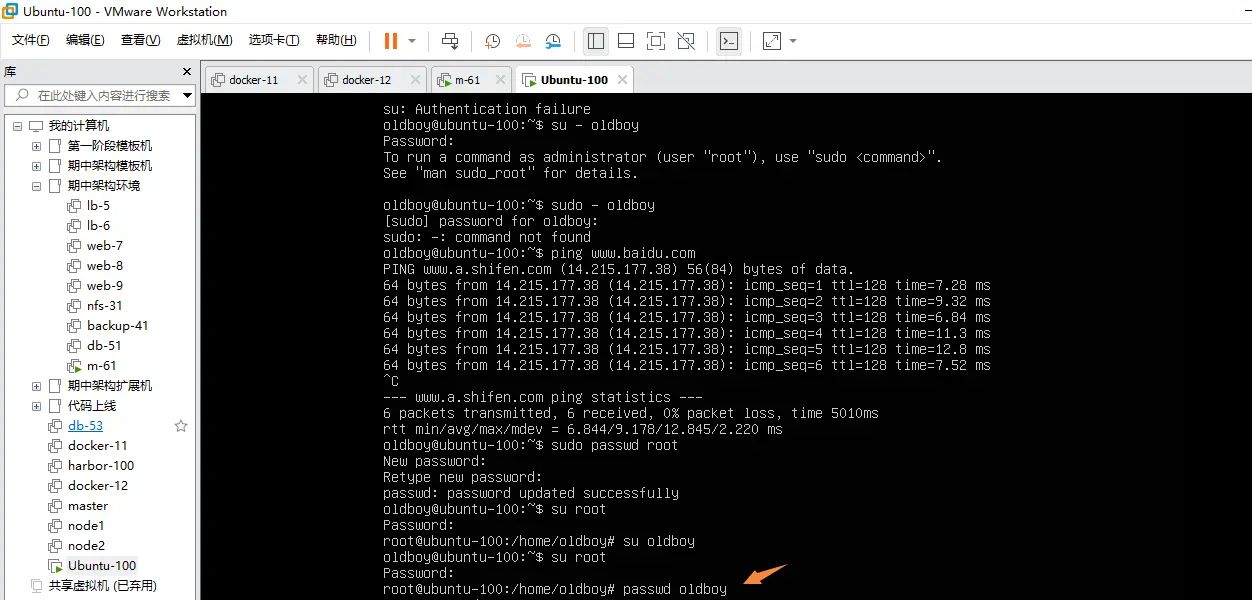
普通用户使用sudo命令修改文件,root也可以使用xshell连接
默认Ubuntu不让xshell连接
可以修改配置文件
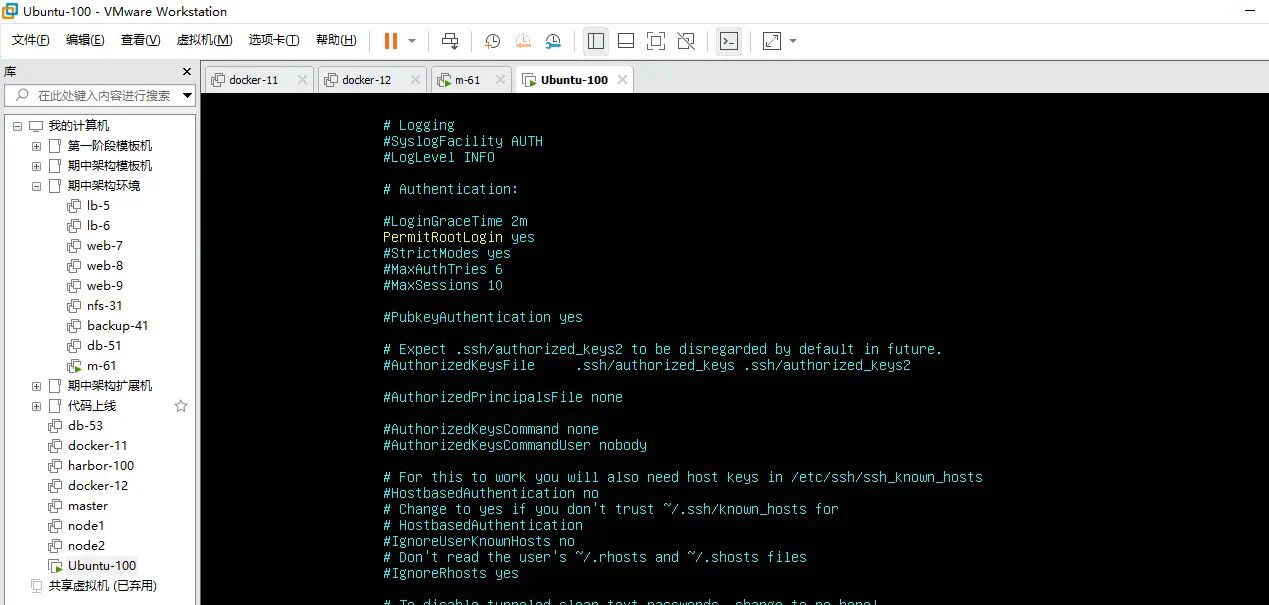
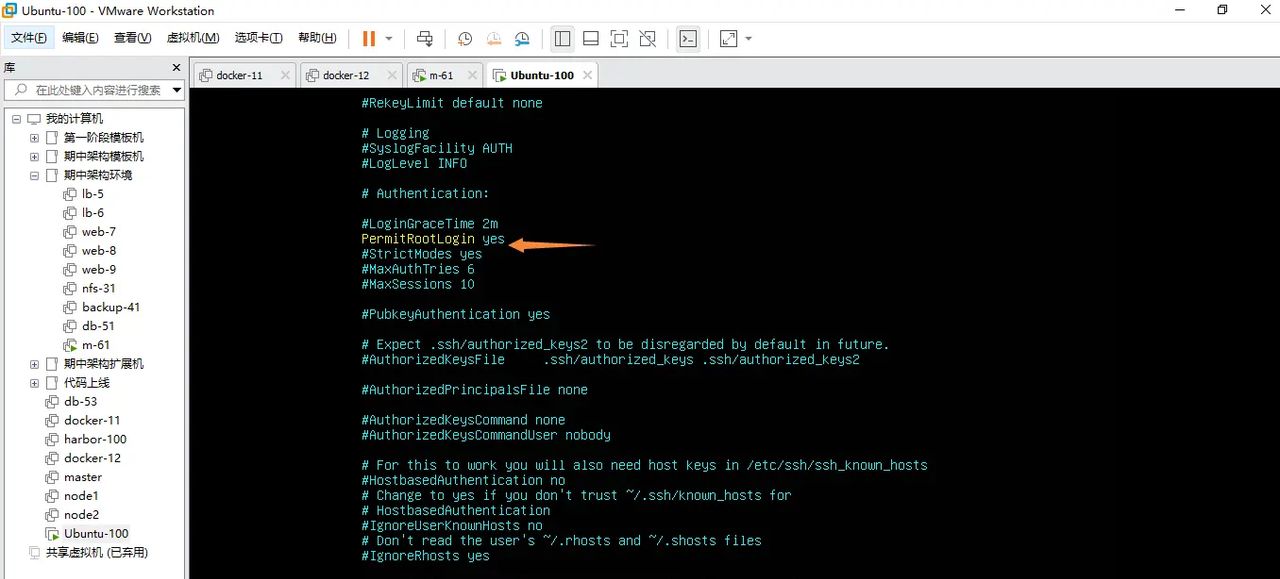
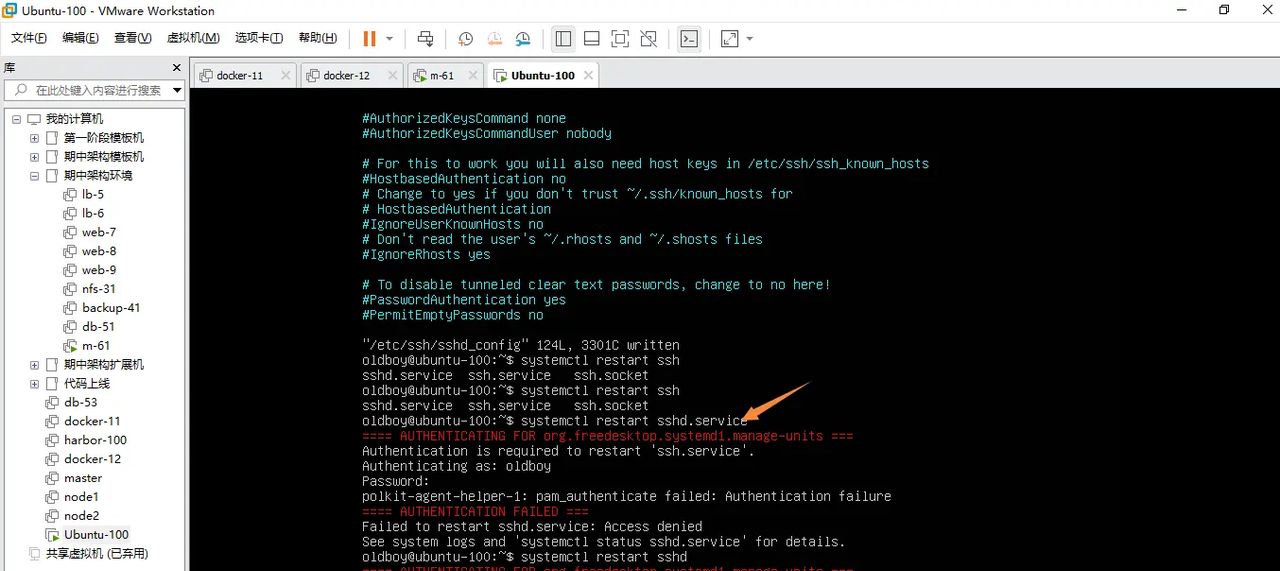
重启ssh
systemctl restart sshd
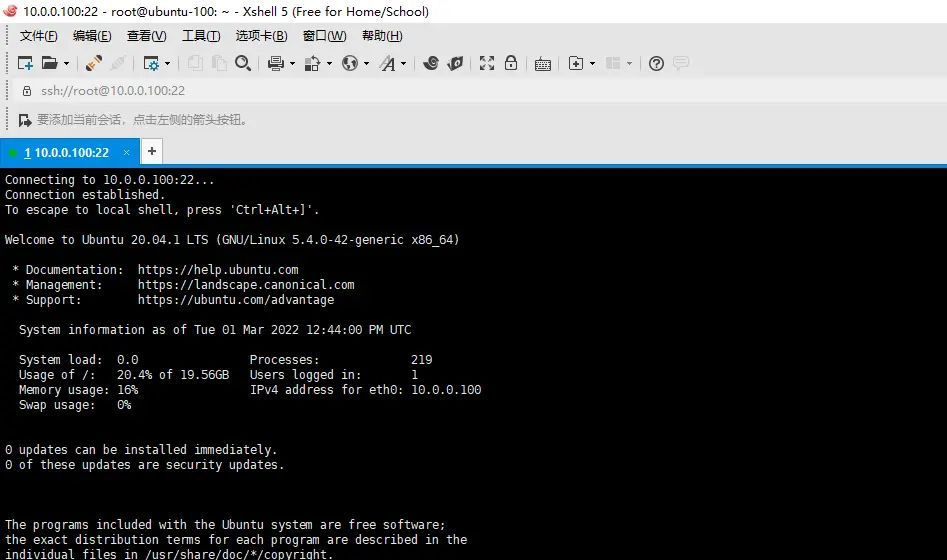
root 连接成功
oldboy也可以连接成功
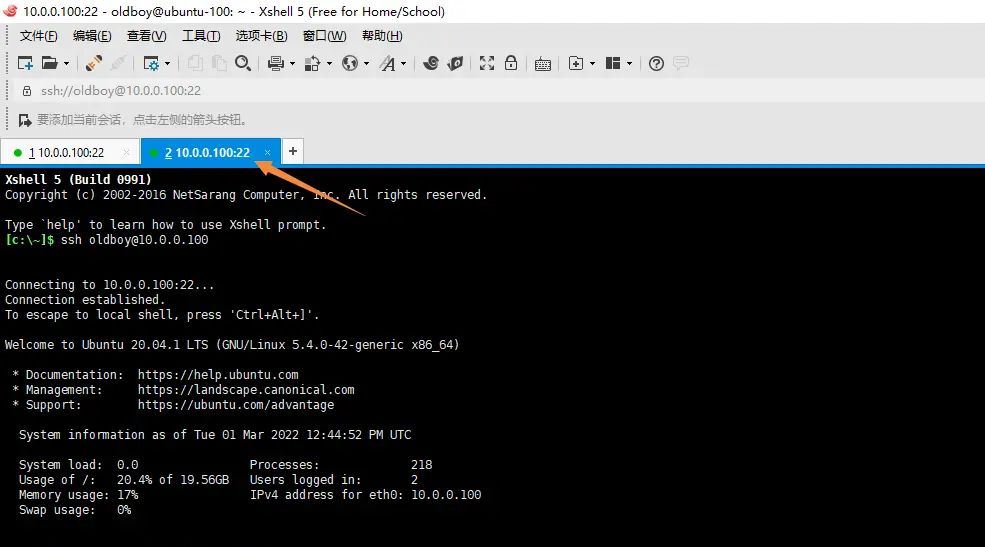
注意:oldboy连接不上去重启sshd
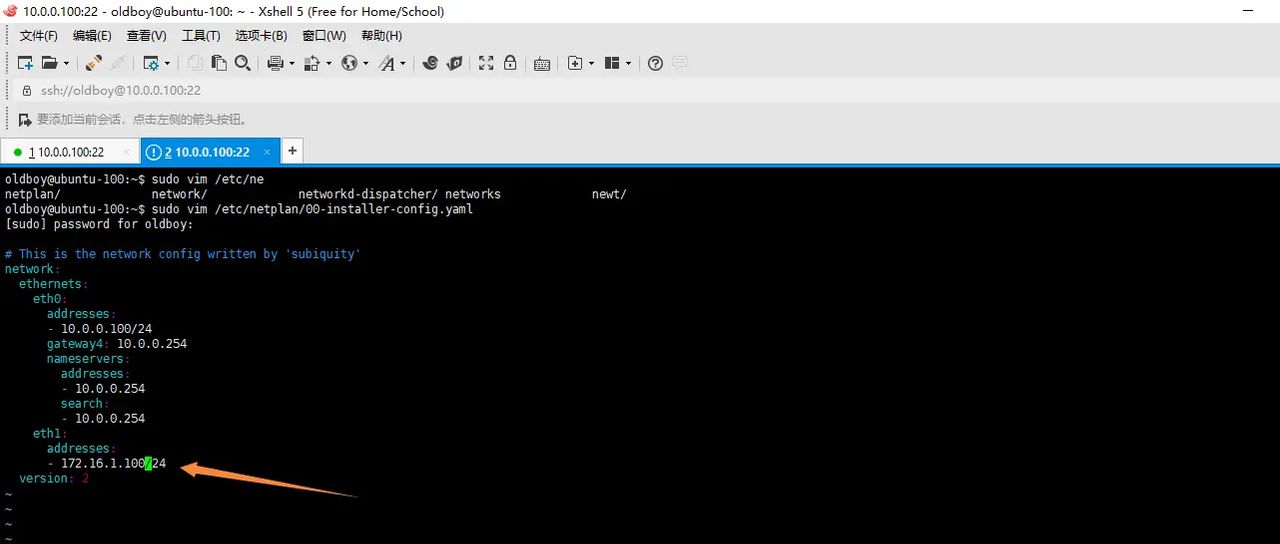
配置网卡是yml文件
sudo vim /etc/netplan/00-installer-config.yaml
第二块网卡地址已经配置好,重启生效
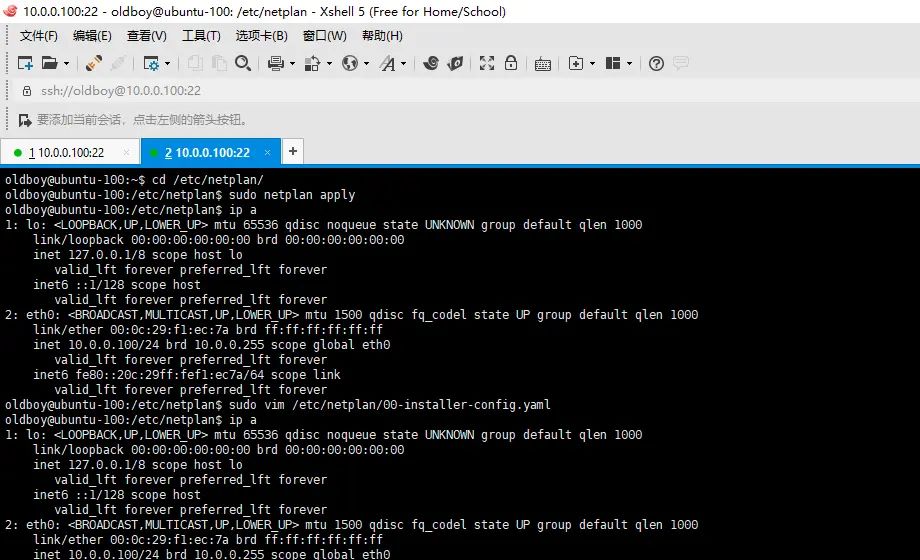
重启网卡
sudo netplan apply
注意:虚拟机也要配置一个网络适配器
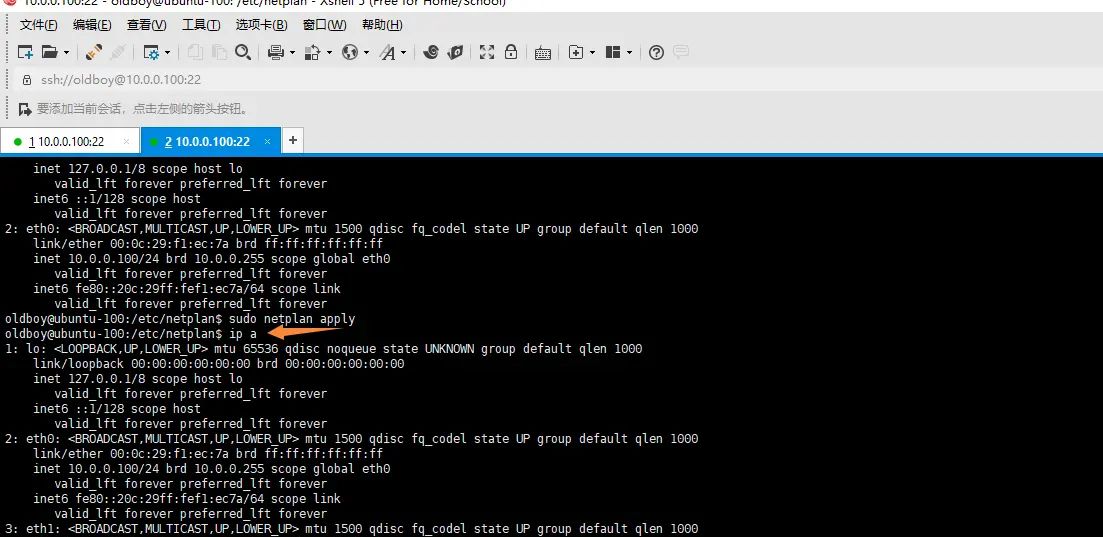
配置apt源
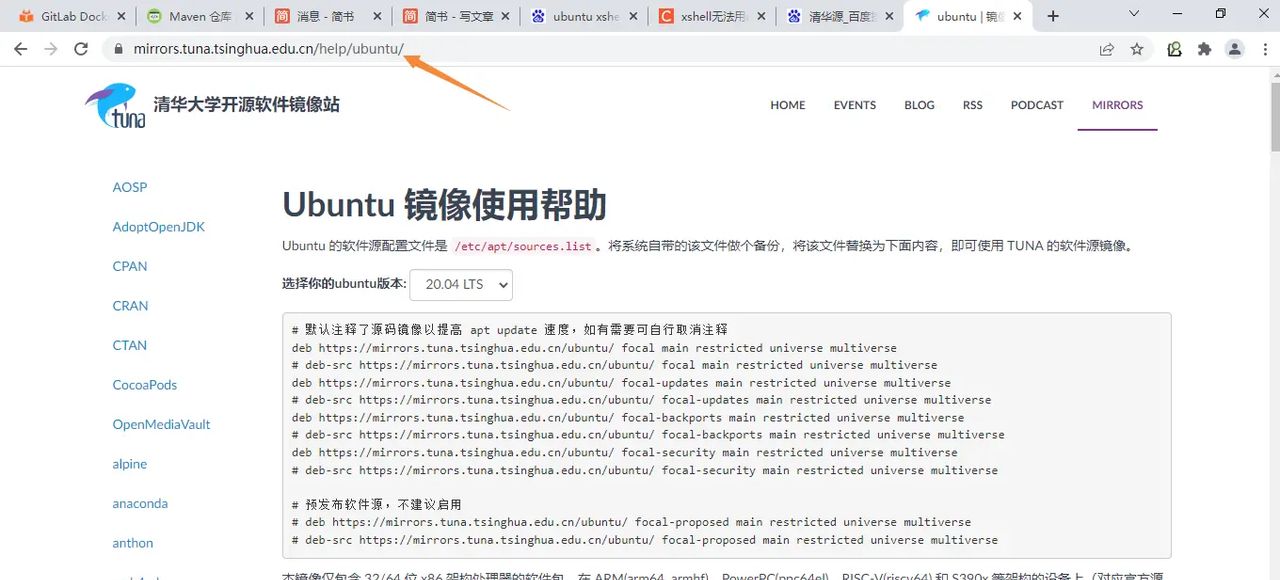
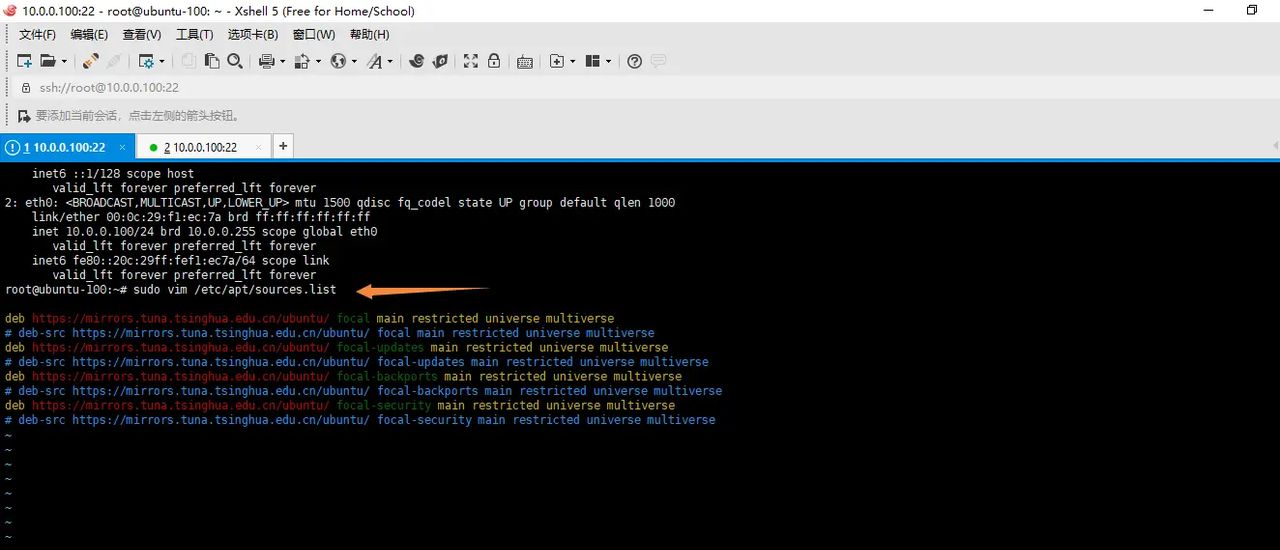
跟新软件包列表
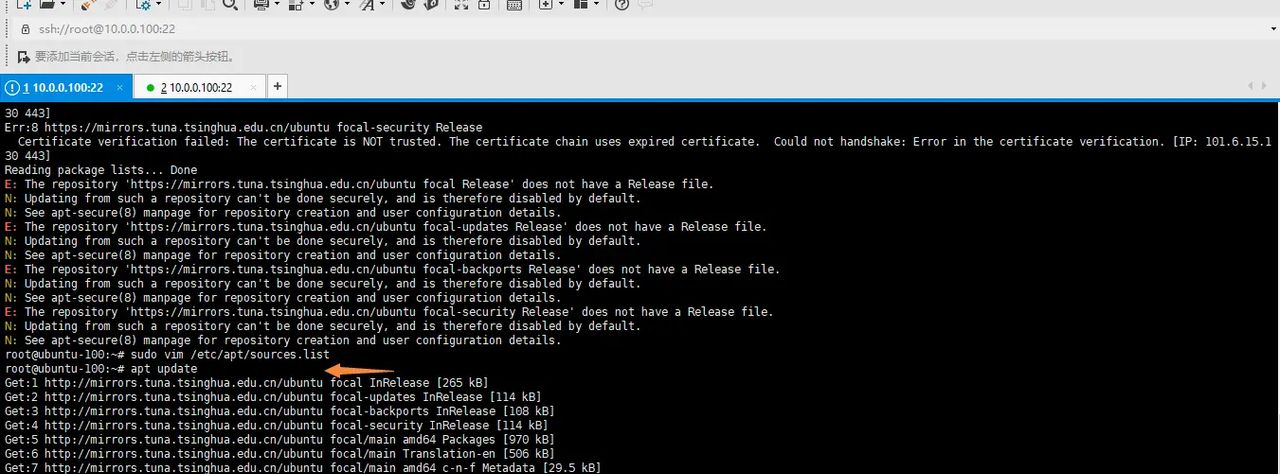
apt update
报错了
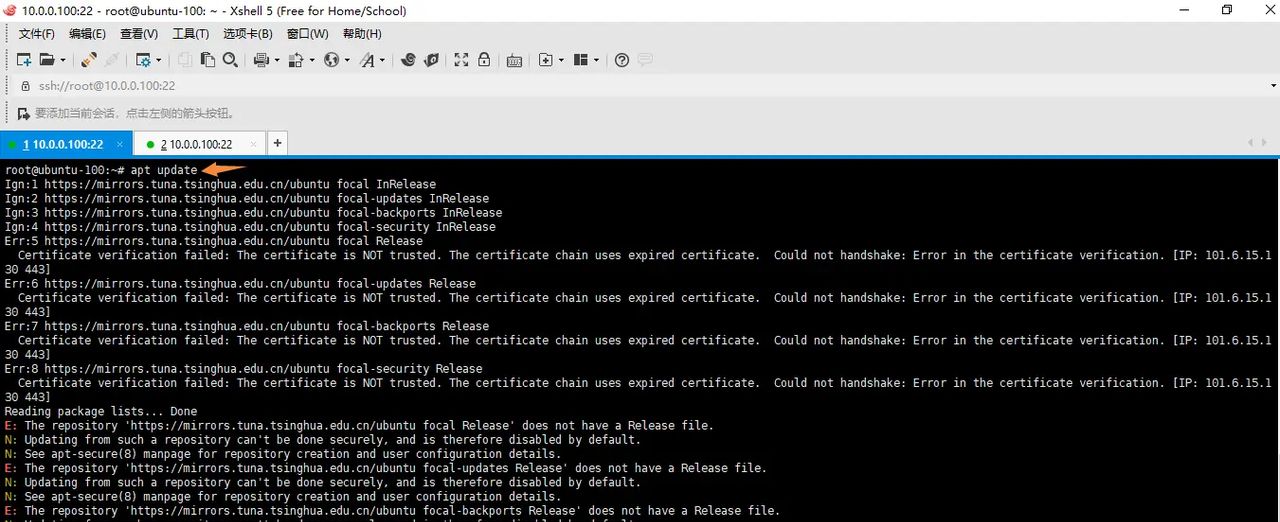
把https去掉s,并把注释的行去掉
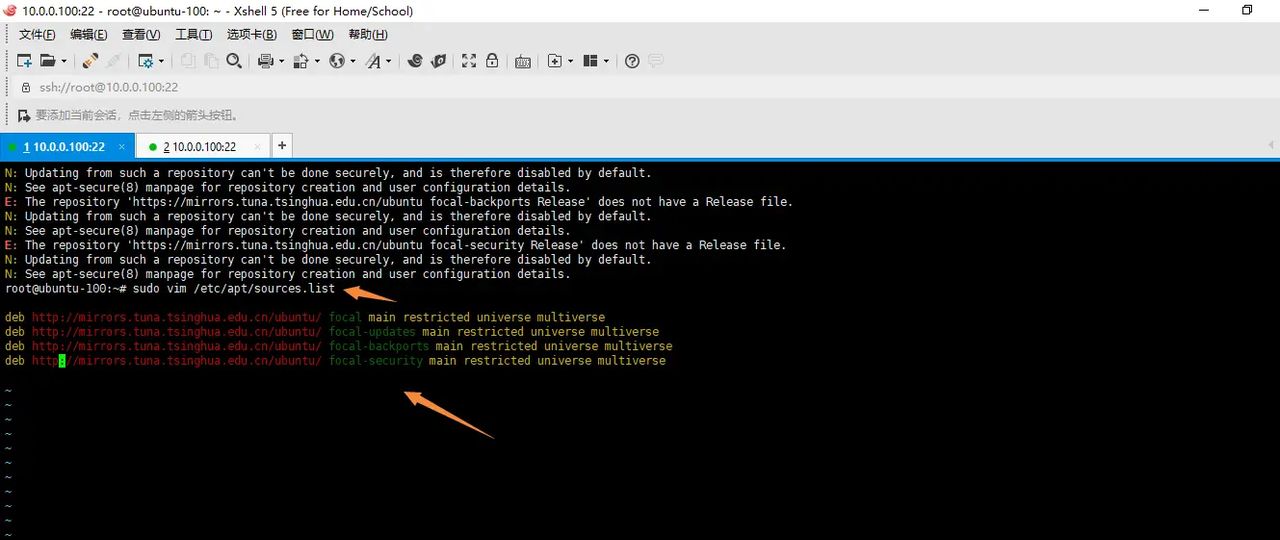
目前就不报错。并且速度很快
软件包格式
centos 是.rpm
ubuntu 是.deb
安装命令
centos yum install
ubunt apt install
更新缓存
centos yum makecache
ubuntu apt update
卸载软件
centos yum remove
ubuntu apt remove
清除缓存
centos yum clean all
ubuntu apt clean all
apt跟apt-get是一样功能
安装软件包
centos rmp -ivh
ubuntu dpkg -i
使用nginx测试
nginx下载地址
http://nginx.org/packages/
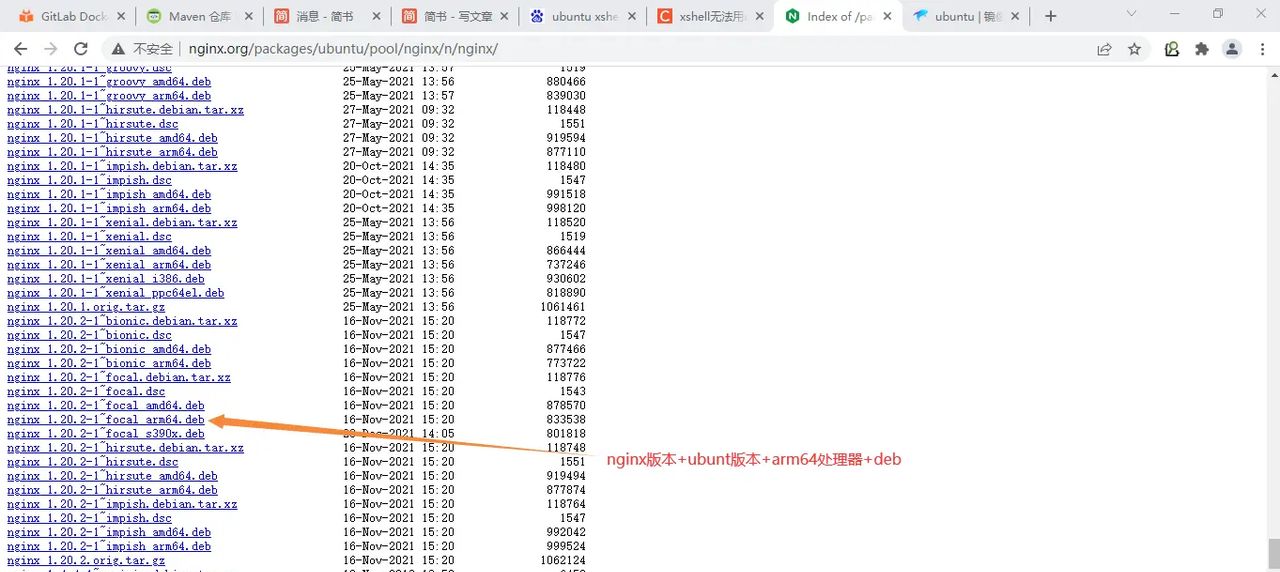
复制地址链接
http://nginx.org/packages/ubuntu/pool/nginx/n/nginx/nginx_1.20.2-1~focal_amd64.deb
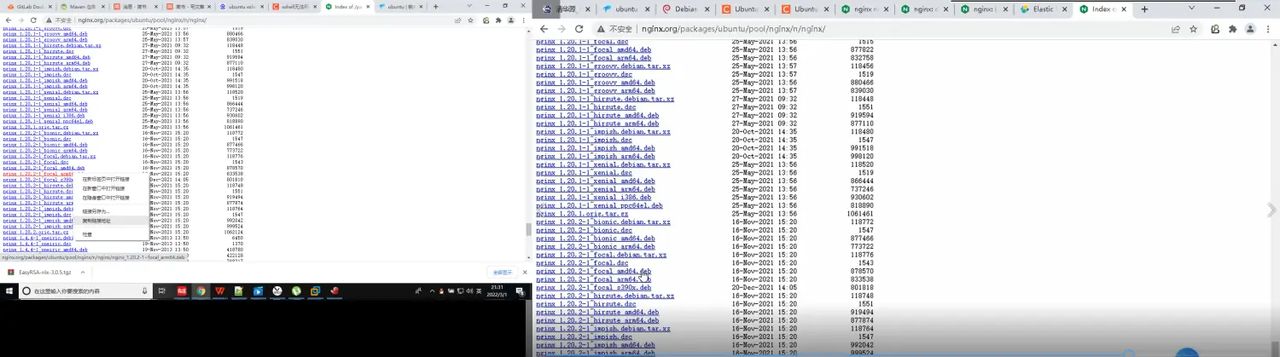
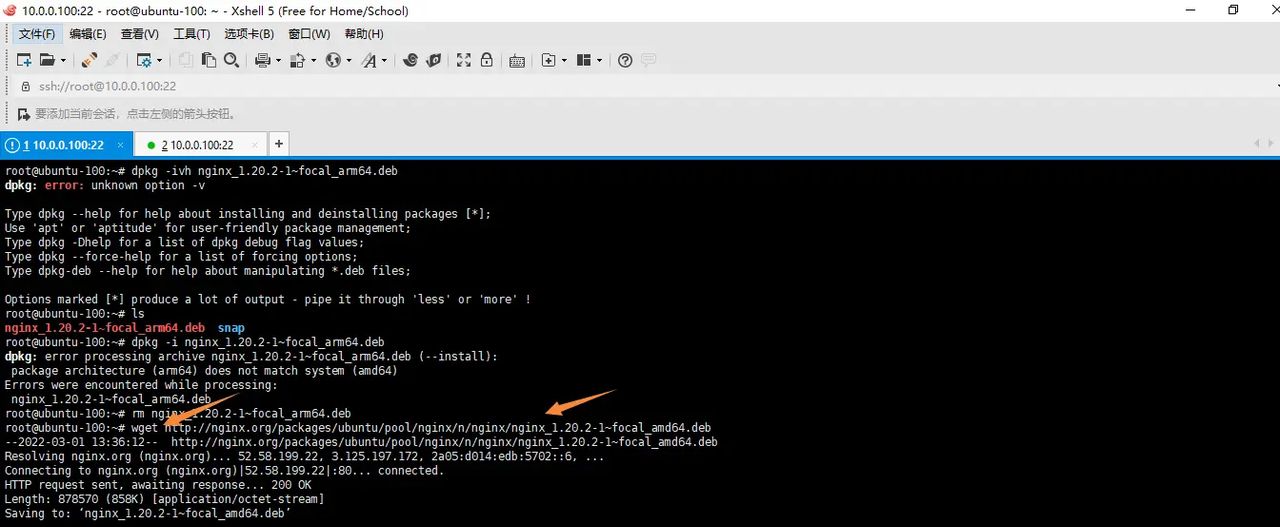
注意:处理器型号是amd64
安装
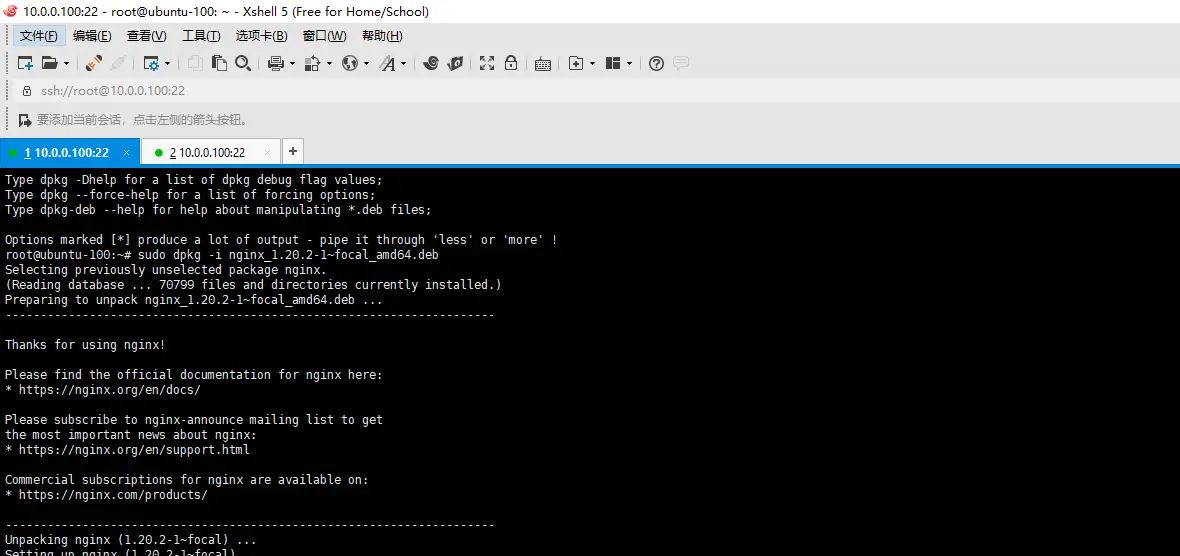
sudo dpkg -i nginx_1.20.2-1~focal_amd64.deb
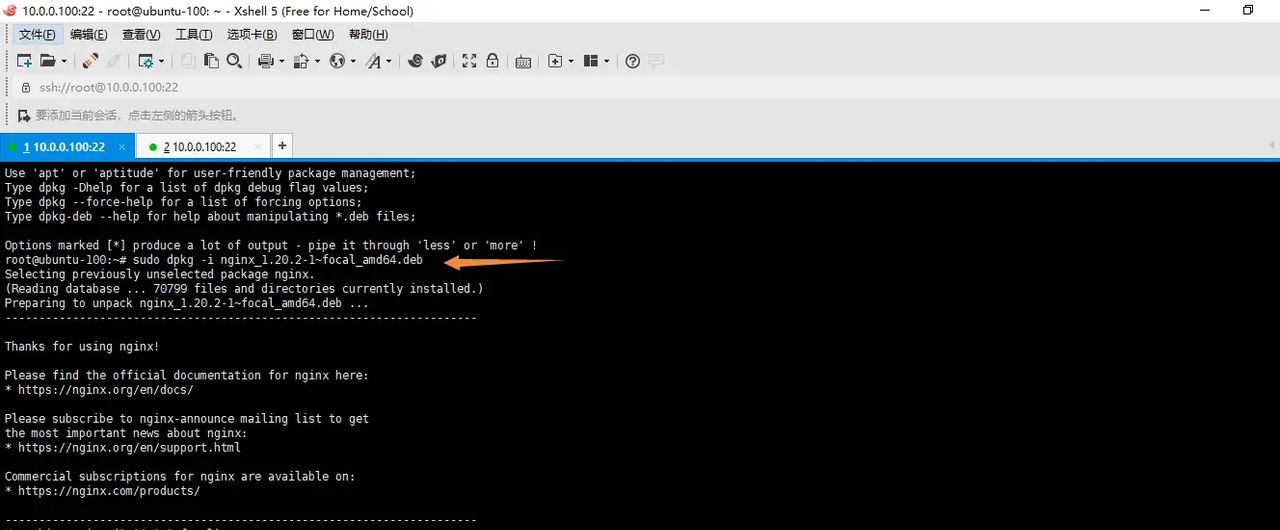
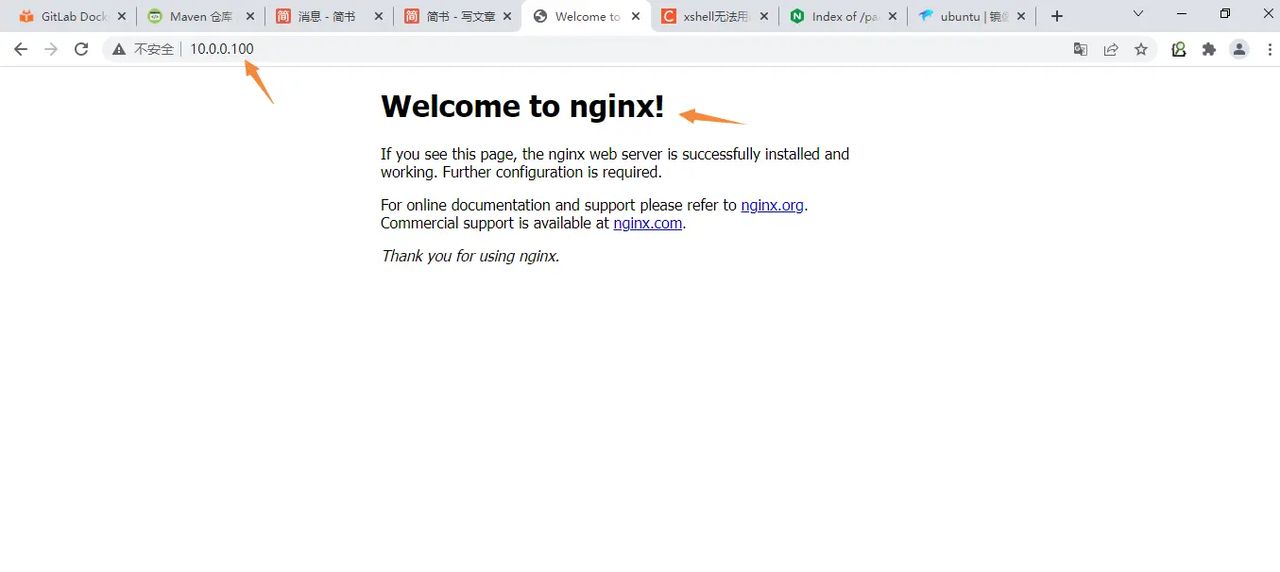
启动nginx测试
注意:安装可道云跟centos流程一样,但是不用装php,ubuntu内置php-7版本
注意:debian系统跟Ubuntu系统命令是一样的
openvpn
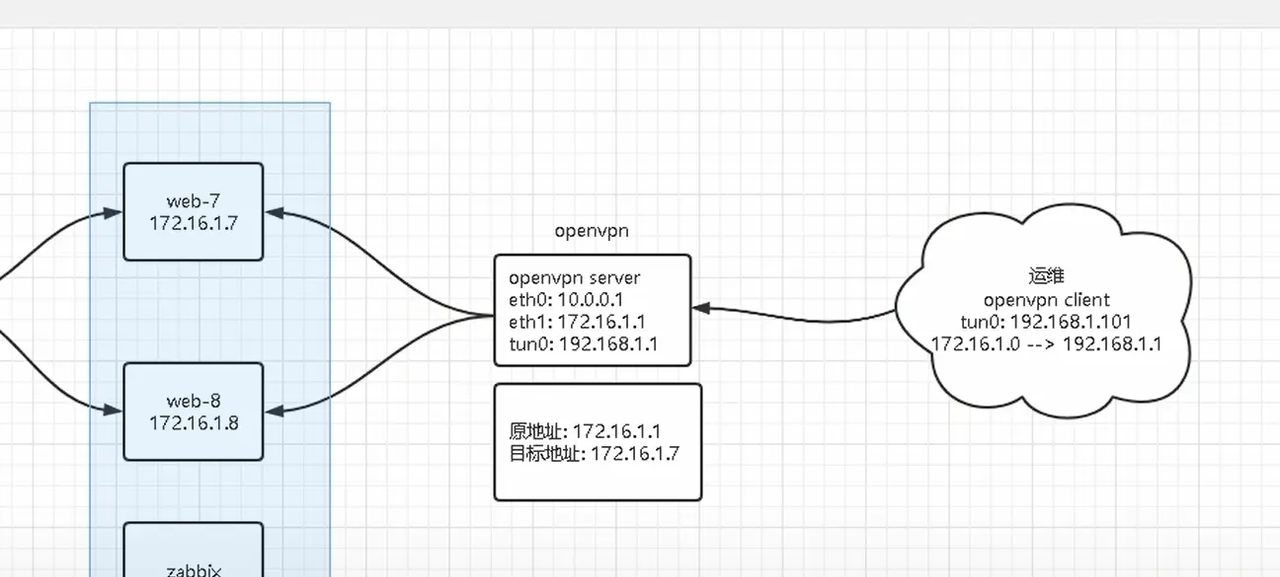
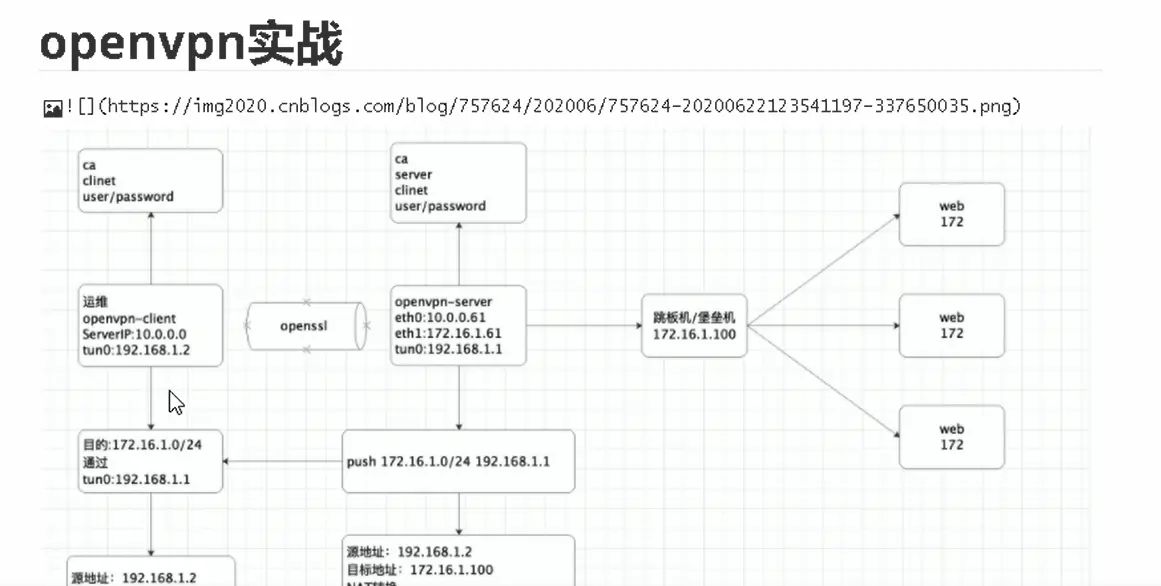
第1章 创建证书
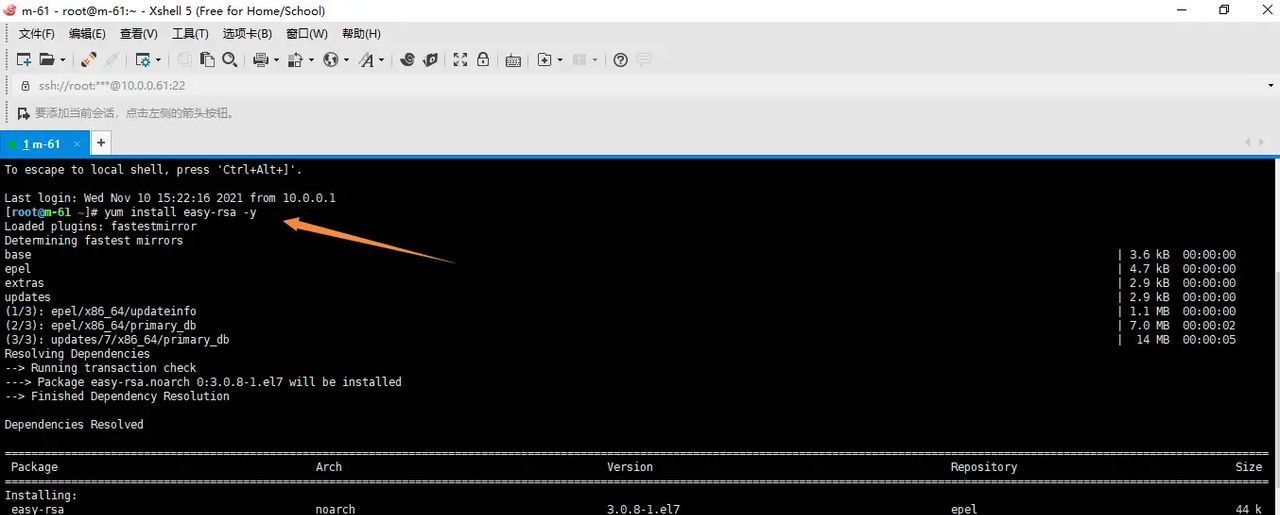
1.安装秘钥工具
yum install easy-rsa -y
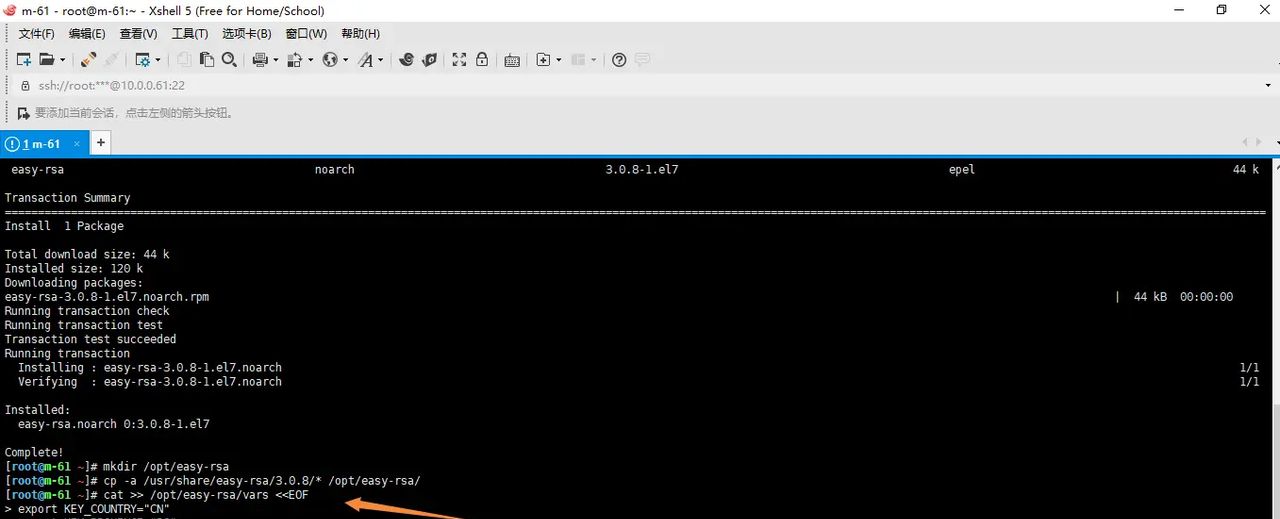
2.准备生成证书的变量文件
mkdir /opt/easy-rsa
cp -a /usr/share/easy-rsa/3.0.8/* /opt/easy-rsa/
cat >> /opt/easy-rsa/vars <<EOF
export KEY_COUNTRY="CN"
export KEY_PROVINCE="BJ"
export KEY_CITY="Beijing"
export KEY_ORG="oldboy"
export KEY_EMAIL="526195417@qq.com"
EOF
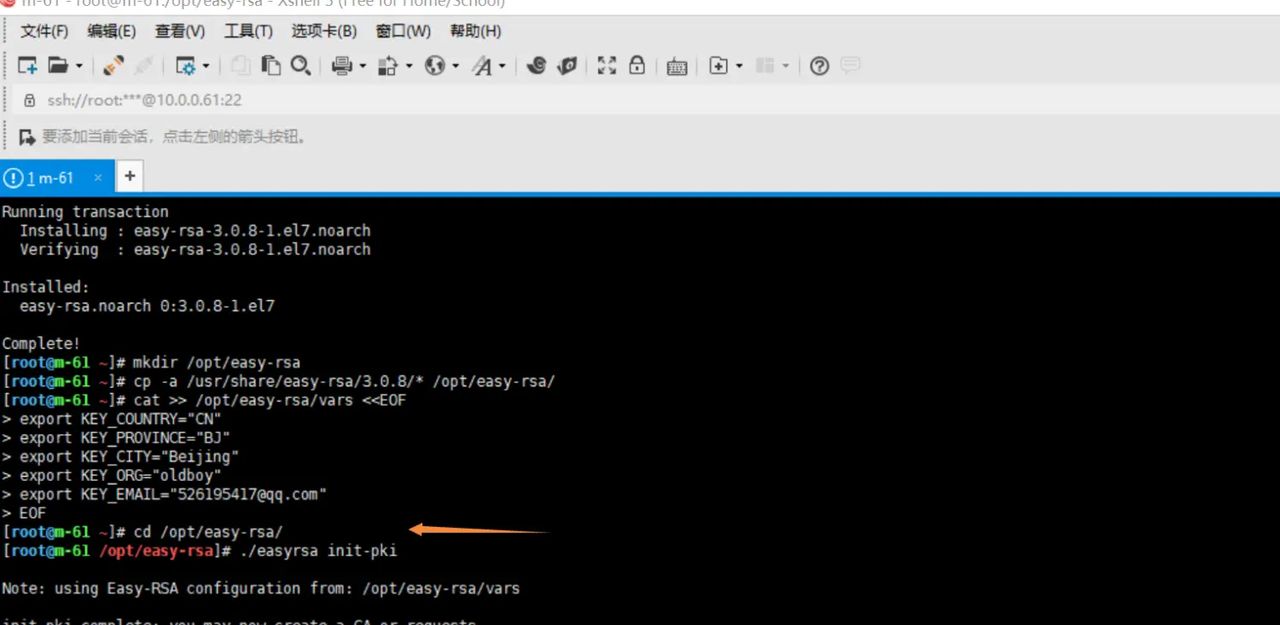
3.生成初始化证书
1.初始化,在当前目录创建PKI目录,用于存储证书
cd /opt/easy-rsa/
./easyrsa init-pki
2.创建根证书,会提示设置密码,大于4位,用于ca对之后生成的server和client证书签名时使用,其他可默认
./easyrsa build-ca

3.创建server端证书和私钥文件,nopass表明不加密私钥文件,其他可默认
./easyrsa gen-req server nopass
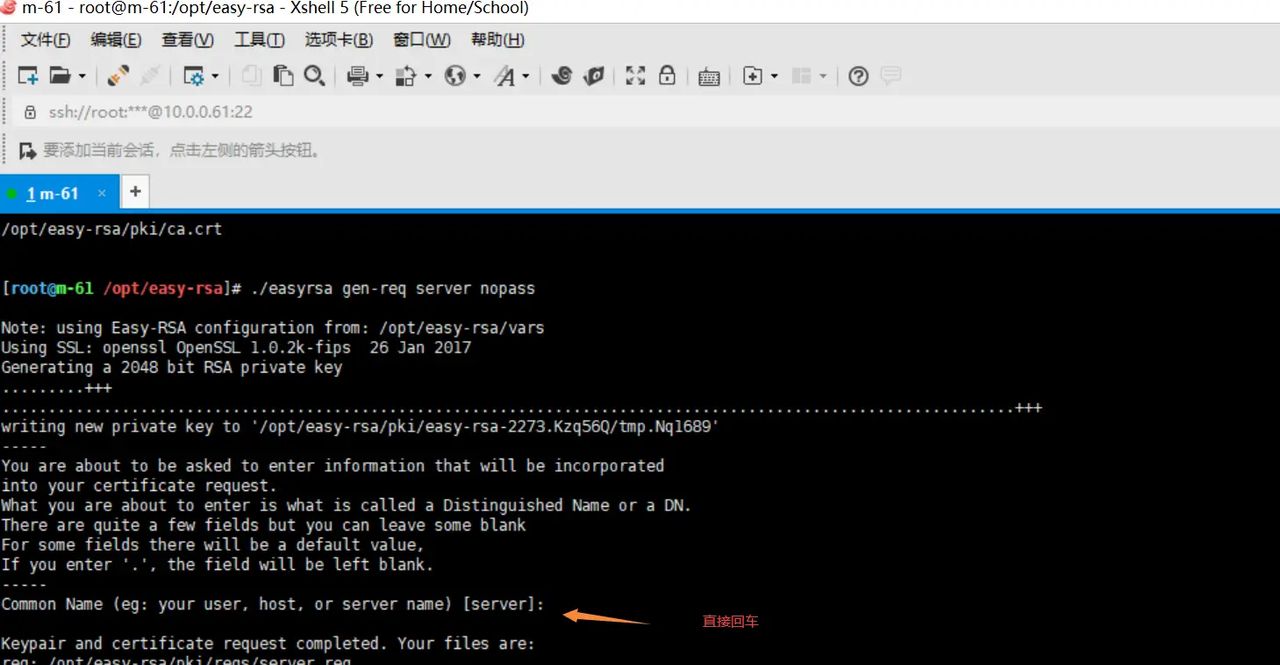
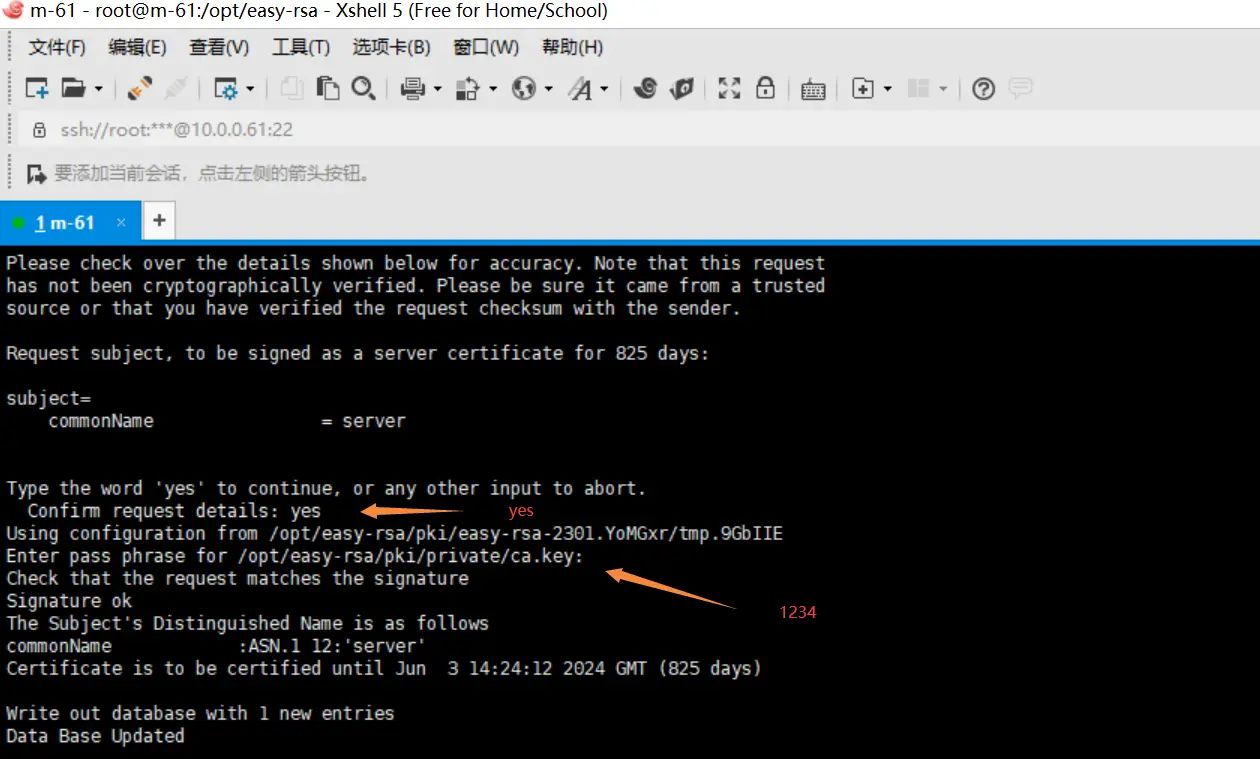
4.给server端证书签名,第一是对一些信息的确认,可以输入yes,然后创建ca根证书时设置的密码
./easyrsa sign server server
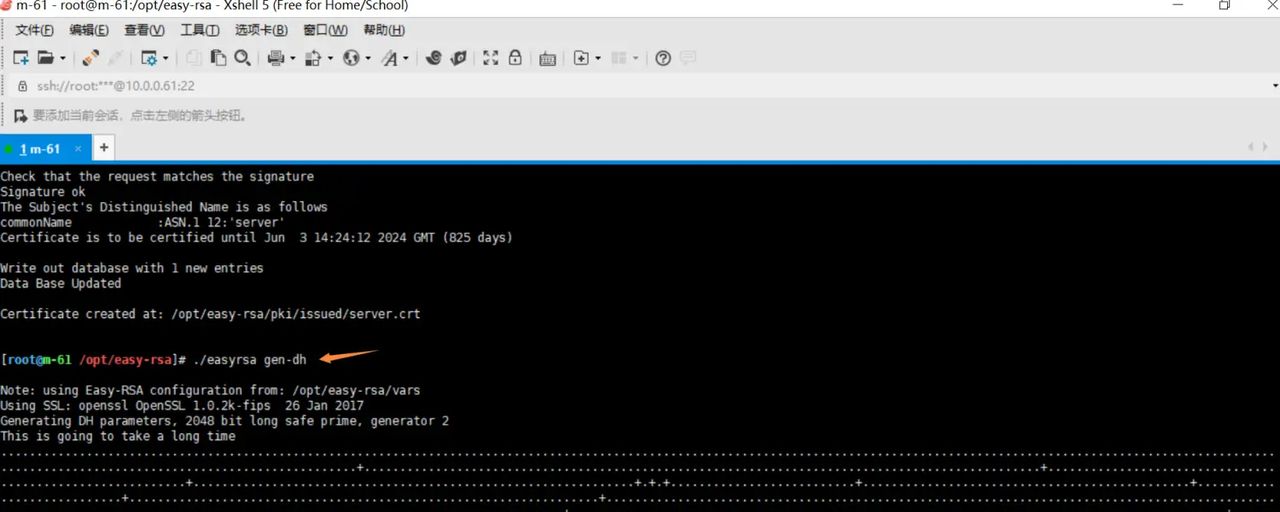
5.创建Diffie-Hellman文件,秘钥交换时的Diffie-Hellman算法
./easyrsa gen-dh
6.创建client端证书和私钥文件,nopass表明不加密私钥文件,其他可默认
./easyrsa gen-req client nopass
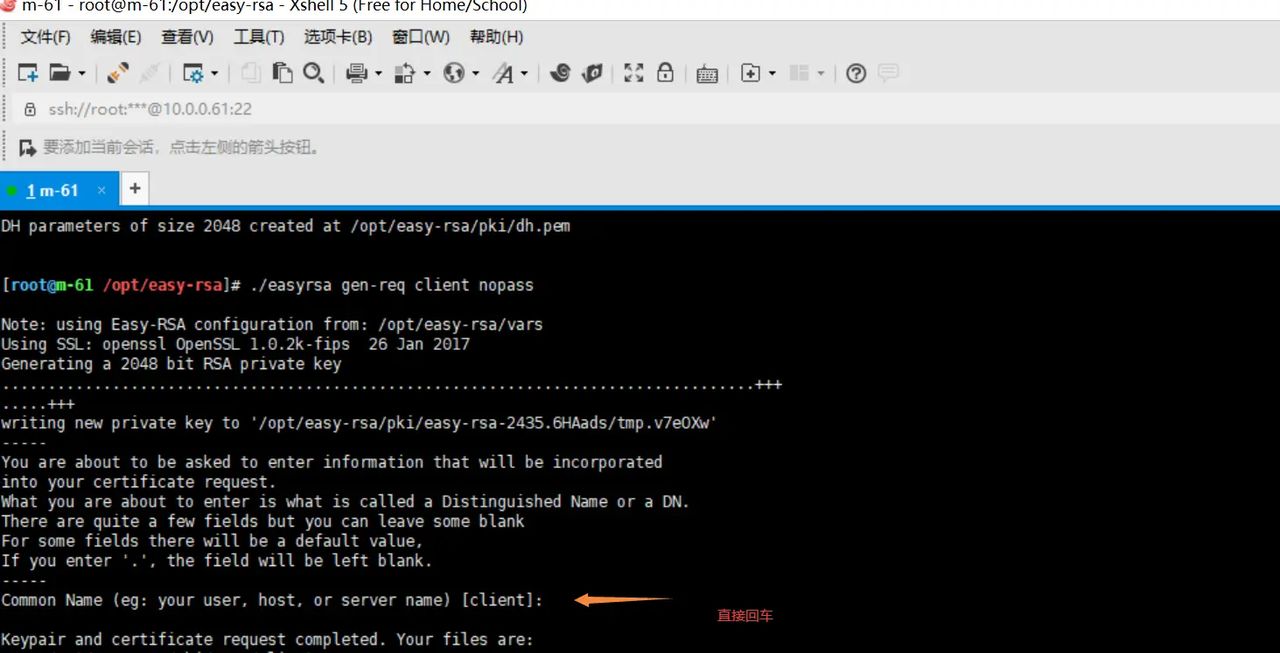
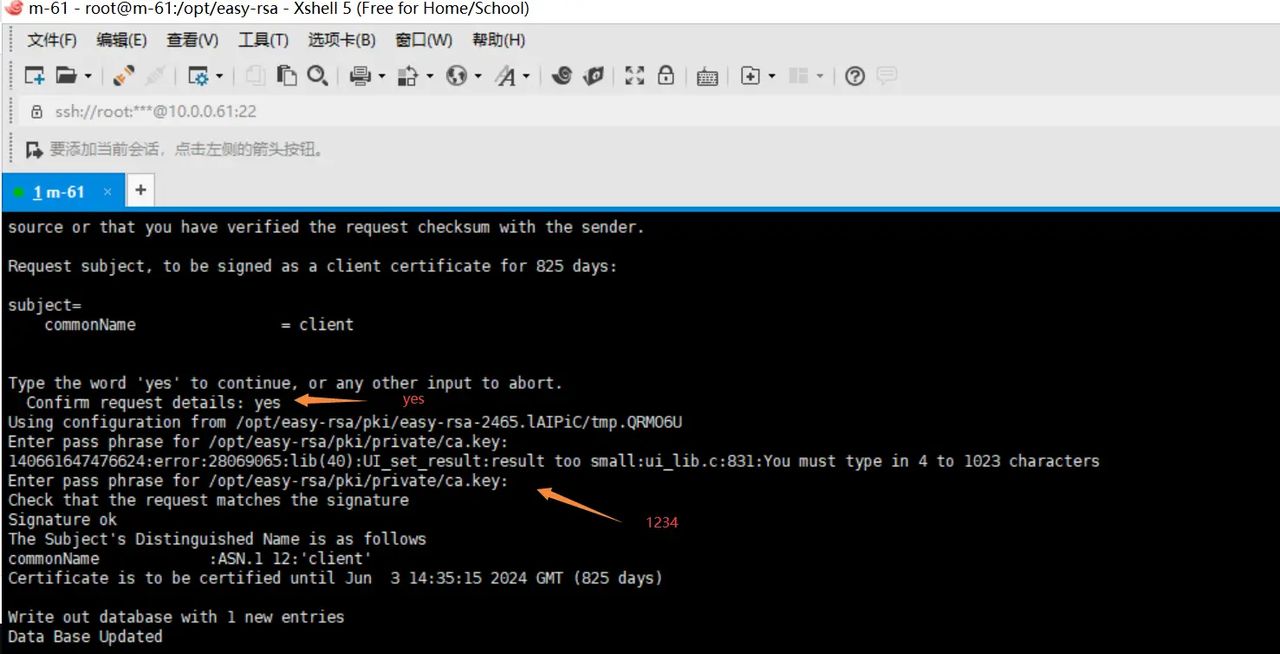
7.给client端证书签名 第一是对一些信息的确认,可以输入yes,然后创建ca根证书时设置的密码
./easyrsa sign client client
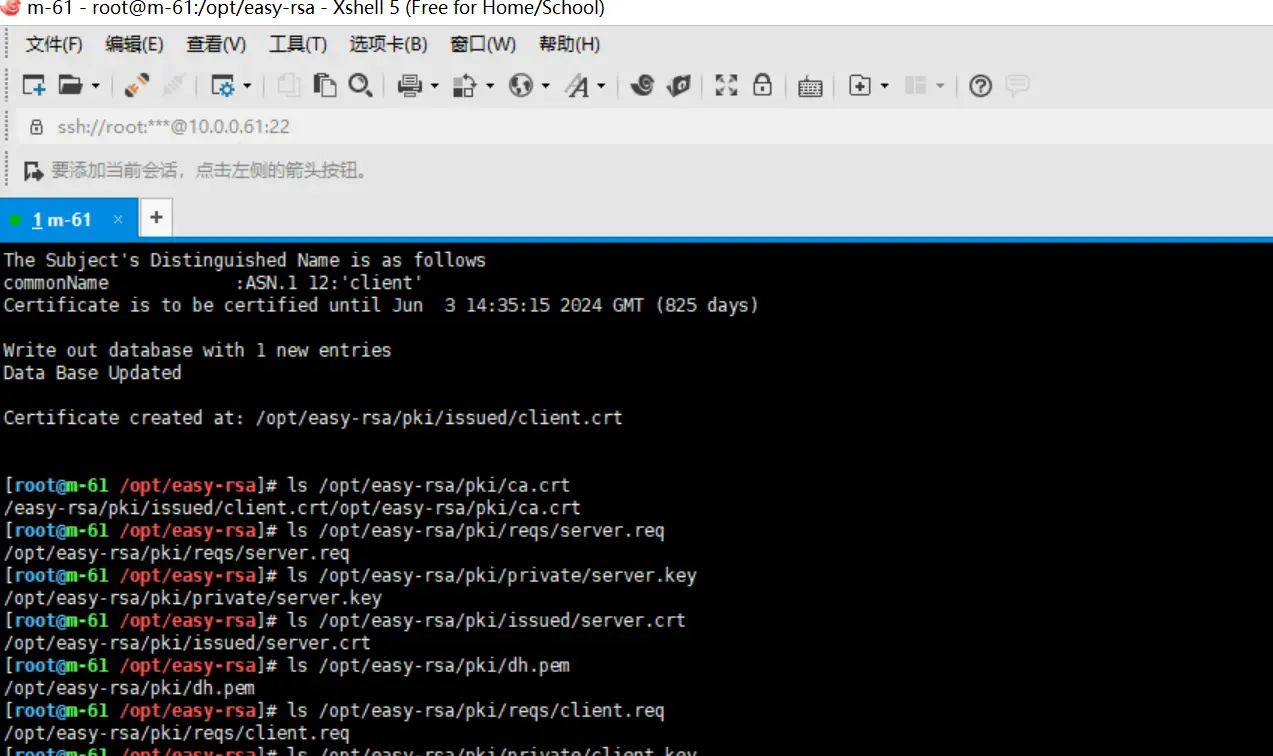
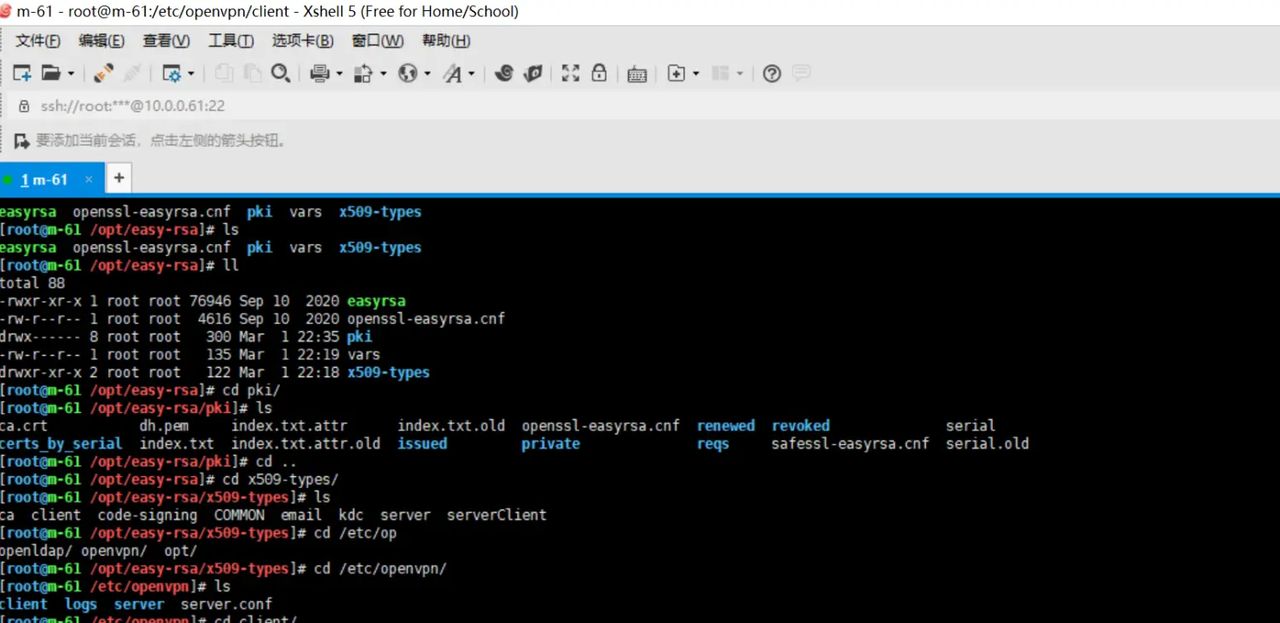
4.检查证书
ls /opt/easy-rsa/pki/ca.crt
ls /opt/easy-rsa/pki/reqs/server.req
ls /opt/easy-rsa/pki/private/server.key
ls /opt/easy-rsa/pki/issued/server.crt
ls /opt/easy-rsa/pki/dh.pem
ls /opt/easy-rsa/pki/reqs/client.req
ls /opt/easy-rsa/pki/private/client.key
ls /opt/easy-rsa/pki/issued/client.crt
第2章 openvpn服务端配置
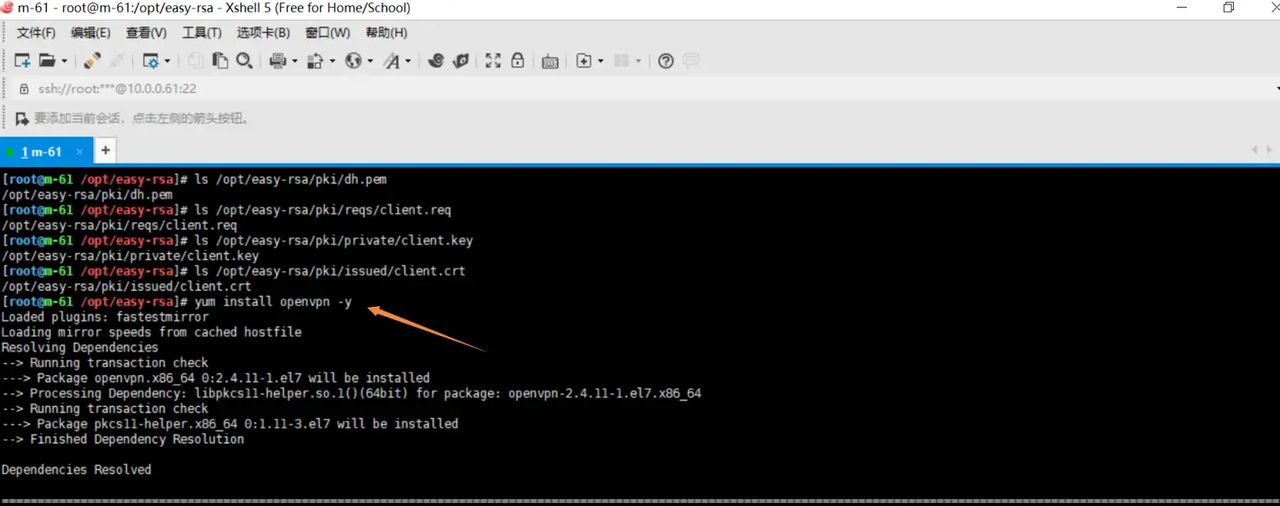
1.安装openvpn服务端
yum install openvpn -y
2.准备证书和目录
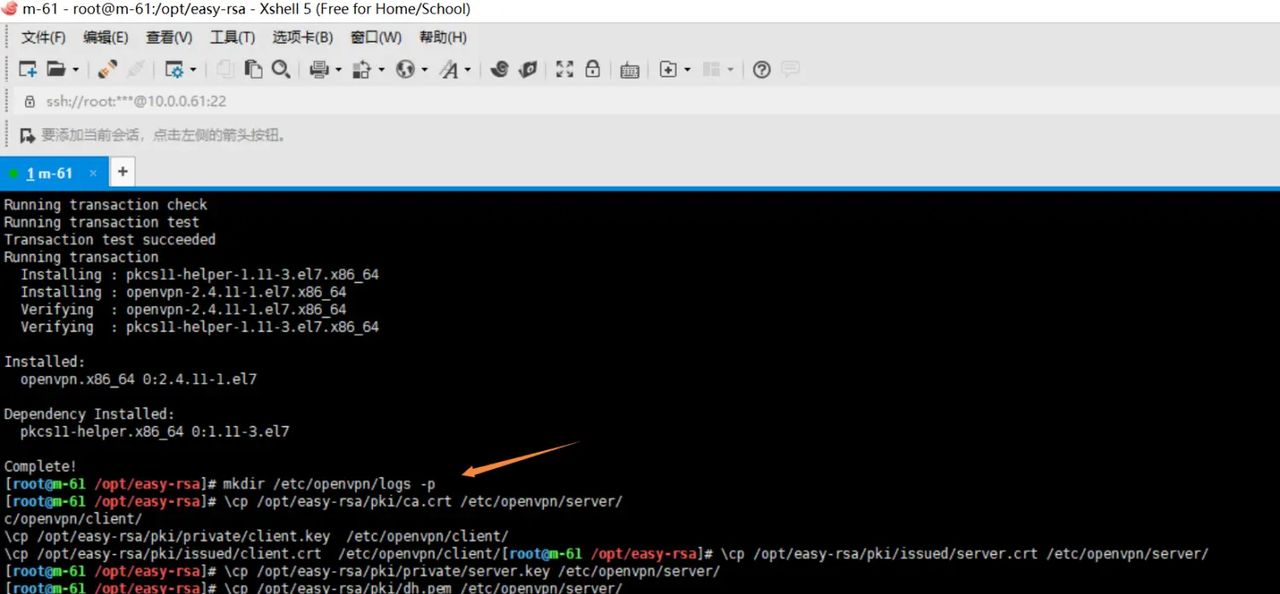
mkdir /etc/openvpn/logs -p
cp /opt/easy-rsa/pki/ca.crt /etc/openvpn/server/
cp /opt/easy-rsa/pki/issued/server.crt /etc/openvpn/server/
cp /opt/easy-rsa/pki/private/server.key /etc/openvpn/server/
cp /opt/easy-rsa/pki/dh.pem /etc/openvpn/server/
cp /opt/easy-rsa/pki/ca.crt /etc/openvpn/client/
cp /opt/easy-rsa/pki/private/client.key /etc/openvpn/client/
cp /opt/easy-rsa/pki/issued/client.crt /etc/openvpn/client/
3.创建配置文件
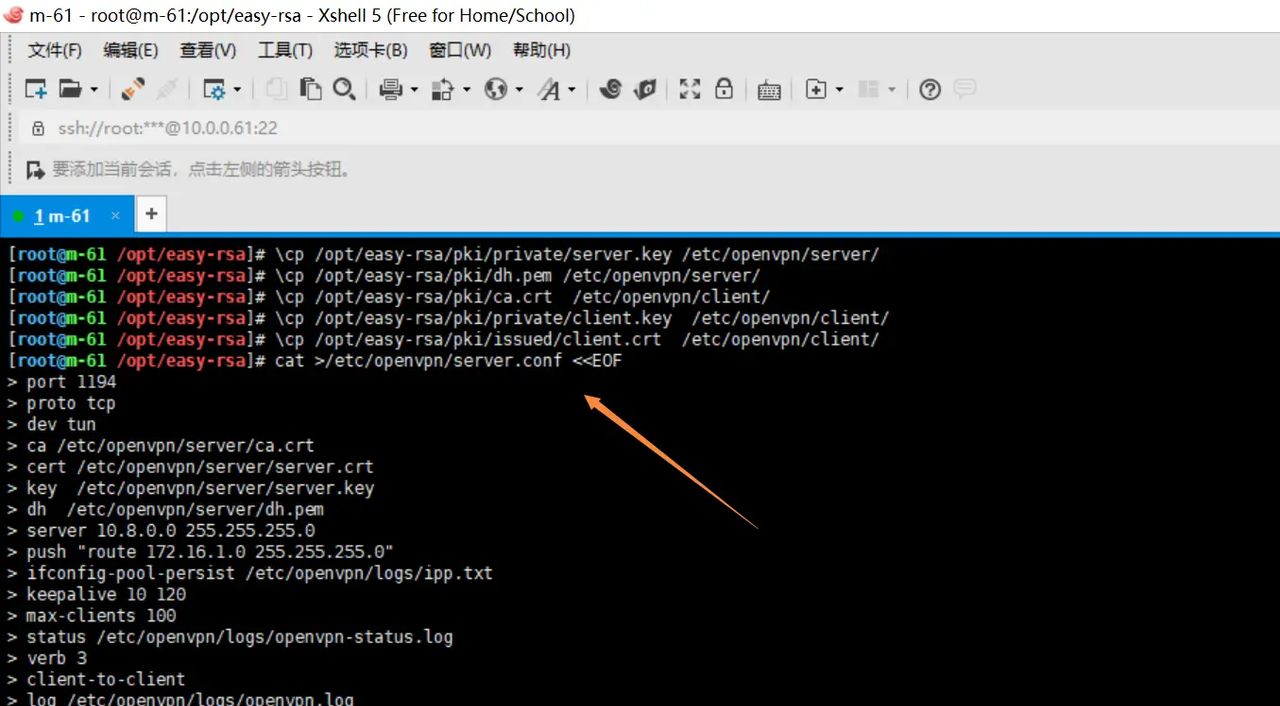
cat >/etc/openvpn/server.conf <<EOF
port 1194
proto tcp
dev tun
ca /etc/openvpn/server/ca.crt
cert /etc/openvpn/server/server.crt
key /etc/openvpn/server/server.key
dh /etc/openvpn/server/dh.pem
server 10.8.0.0 255.255.255.0
push “route 172.16.1.0 255.255.255.0”
ifconfig-pool-persist /etc/openvpn/logs/ipp.txt
keepalive 10 120
max-clients 100
status /etc/openvpn/logs/openvpn-status.log
verb 3
client-to-client
log /etc/openvpn/logs/openvpn.log
persist-key
persist-tun
duplicate-cn
EOF
4.开启内核转发
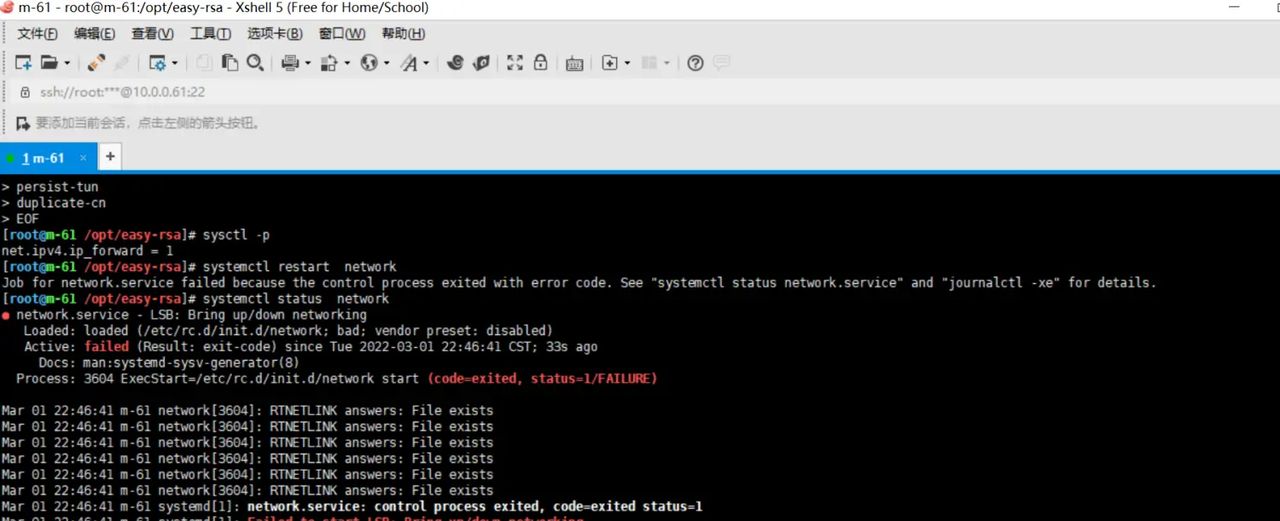
echo “net.ipv4.ip_forward = 1” >> /etc/sysctl.conf
sysctl -p
systemctl restart network
5.设置防火墙
iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -d 172.16.1.0/24 -j SNAT –to-source 172.16.1.61
6.启动服务端
systemctl enable openvpn@server.service
systemctl start openvpn@server.service
第3章 客户端安装
1.windows下客户端安装
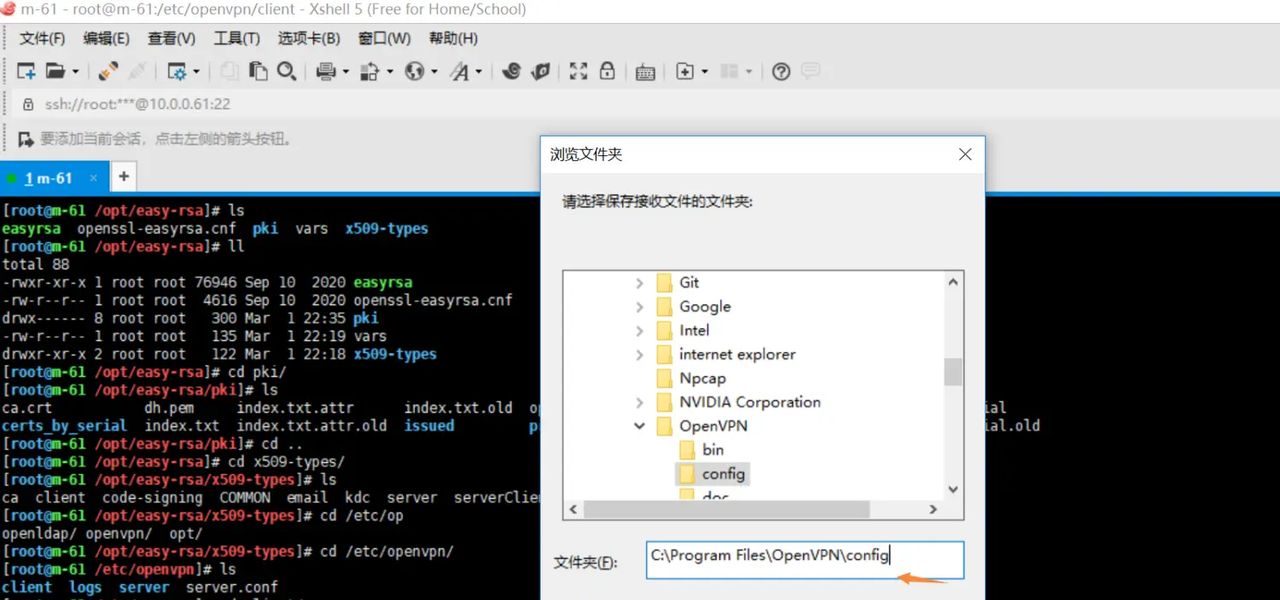
下载安装openvpn软件
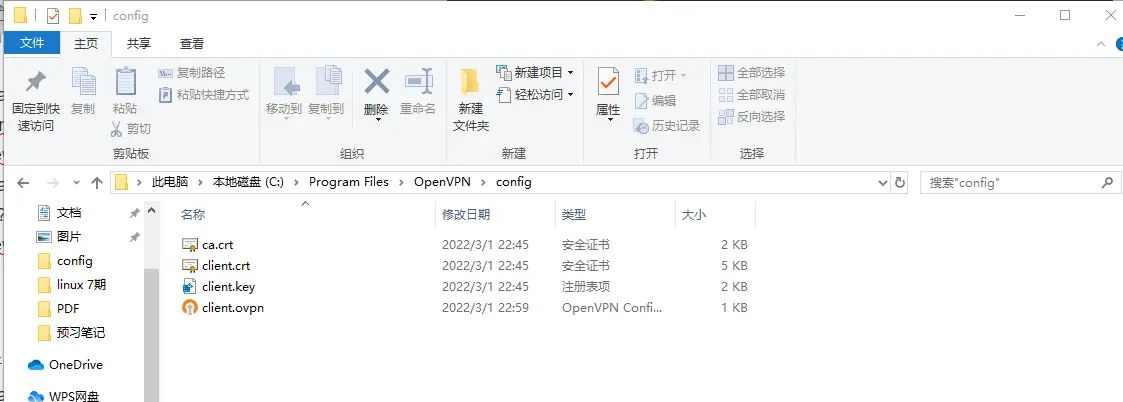
将配置文件放到软件的安装目录下的config目录下
点击连接按钮
2.创建客户端文件
client
dev tun
proto tcp
remote 10.0.0.61 1194
resolv-retry infinite
nobind
ca ca.crt
cert client.crt
key client.key
verb 3
persist-key
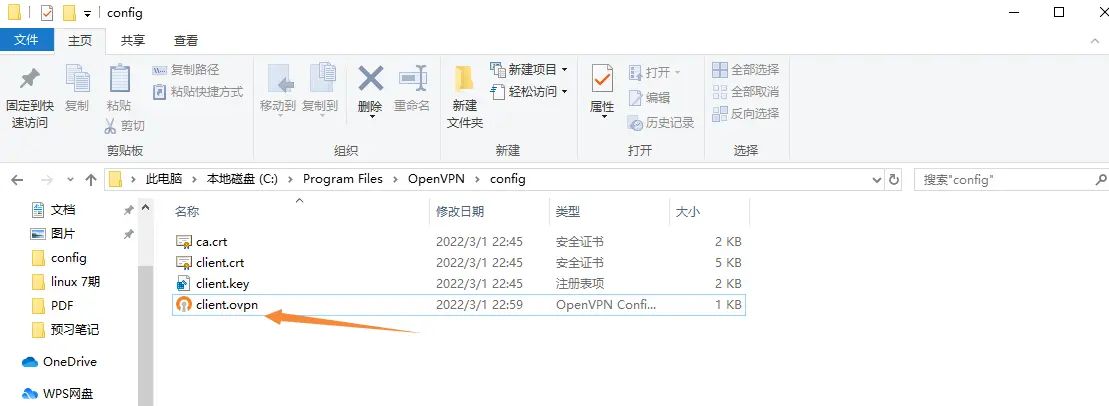
后缀名是ovpn
发送到电脑设置目录里面
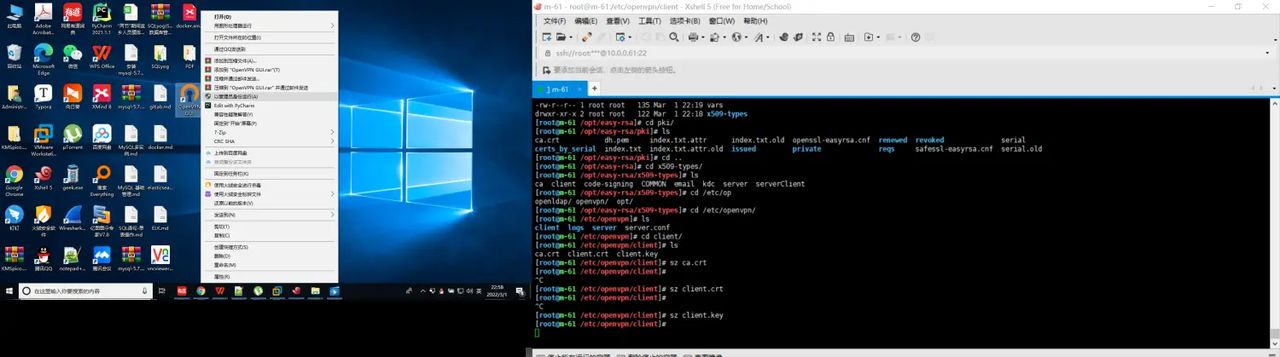
打开openvpn
注意:以管理员方式运行
连接成功
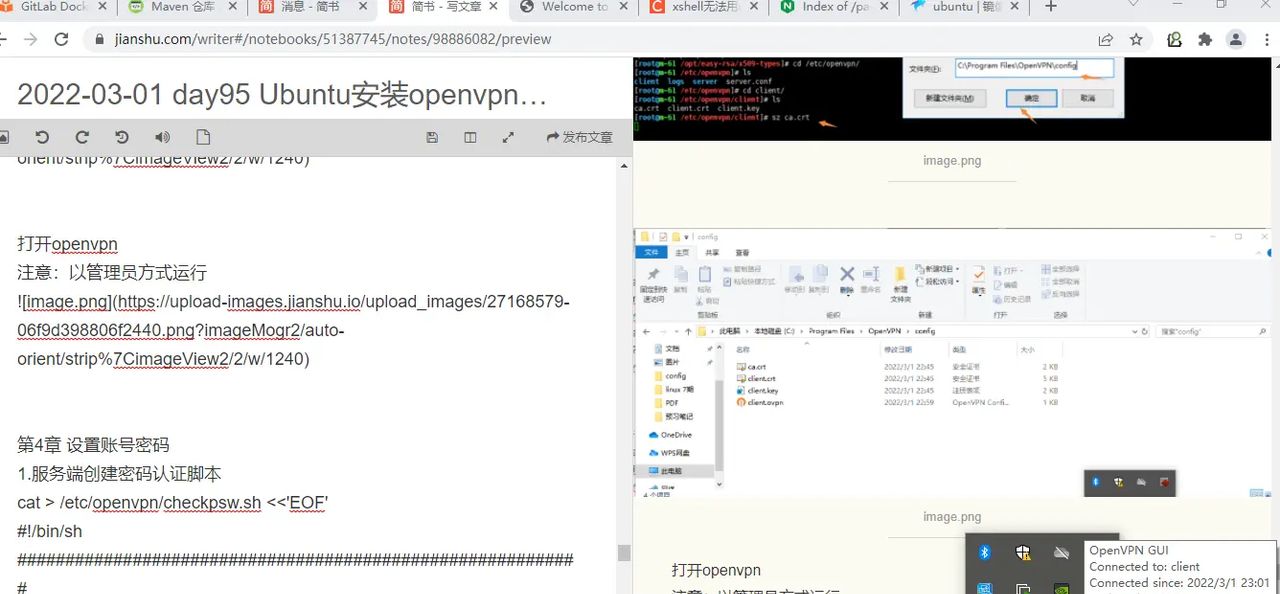
ping测试
第4章 设置账号密码
1.服务端创建密码认证脚本
cat > /etc/openvpn/checkpsw.sh << EOF
#!/bin/sh
###########################################################
# checkpsw.sh (C) 2004 Mathias Sundman <mathias@openvpn.se>
#
# This script will authenticate OpenVPN users against
# a plain text file. The passfile should simply contain
# one row per user with the username first followed by
# one or more space(s) or tab(s) and then the password.
PASSFILE="/etc/openvpn/psw-file"
LOG_FILE="/etc/openvpn/logs/openvpn-password.log"
TIME_STAMP=`date "+%Y-%m-%d %T"`
###########################################################
if [ ! -r "${PASSFILE}" ]; then
echo "${TIME_STAMP}: Could not open password file "${PASSFILE}" for reading." >> ${LOG_FILE}
exit 1
fi
CORRECT_PASSWORD=`awk !/^;/&&!/^#/&&$1==" ${username} "{print $2;exit} ${PASSFILE}`
if [ "${CORRECT_PASSWORD}" = "" ]; then
echo "${TIME_STAMP}: User does not exist: username="${username}", password=
"${password}"." >> ${LOG_FILE}
exit 1
fi
if [ "${password}" = "${CORRECT_PASSWORD}" ]; then
echo "${TIME_STAMP}: Successful authentication: username="${username}"." >> ${LOG_FILE}
exit 0
fi
echo "${TIME_STAMP}: Incorrect password: username="${username}", password=
"${password}"." >> ${LOG_FILE}
exit 1
EOF
chmod +x /etc/openvpn/checkpsw.sh
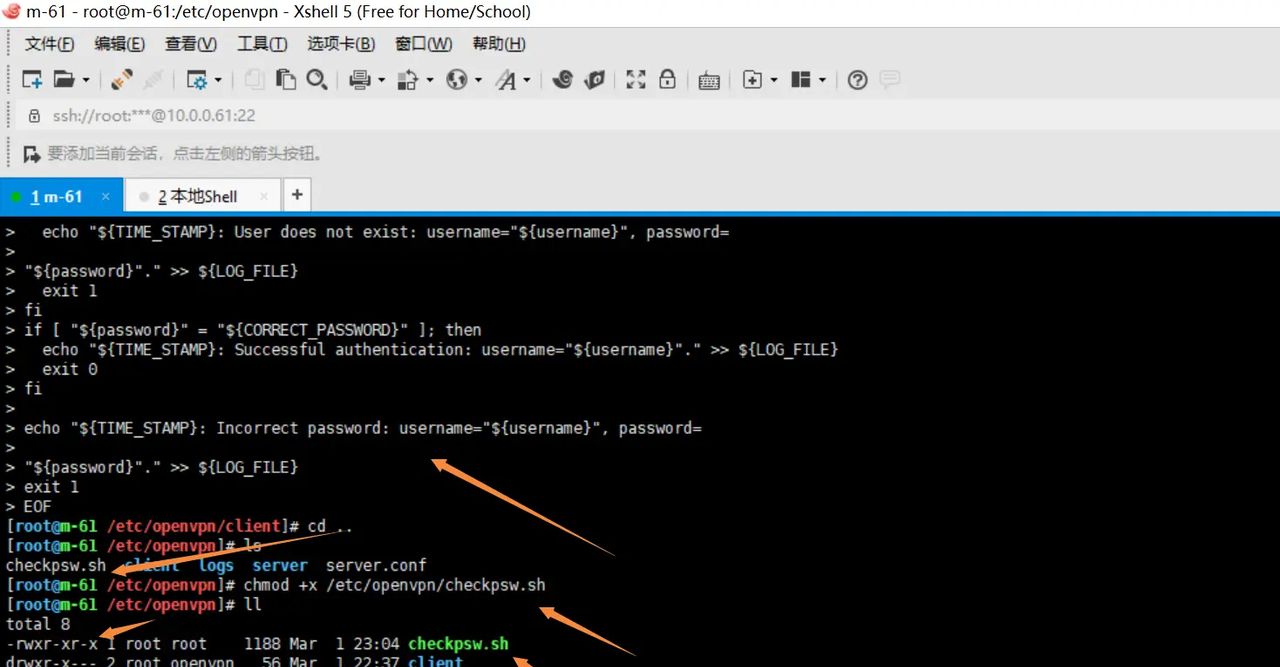
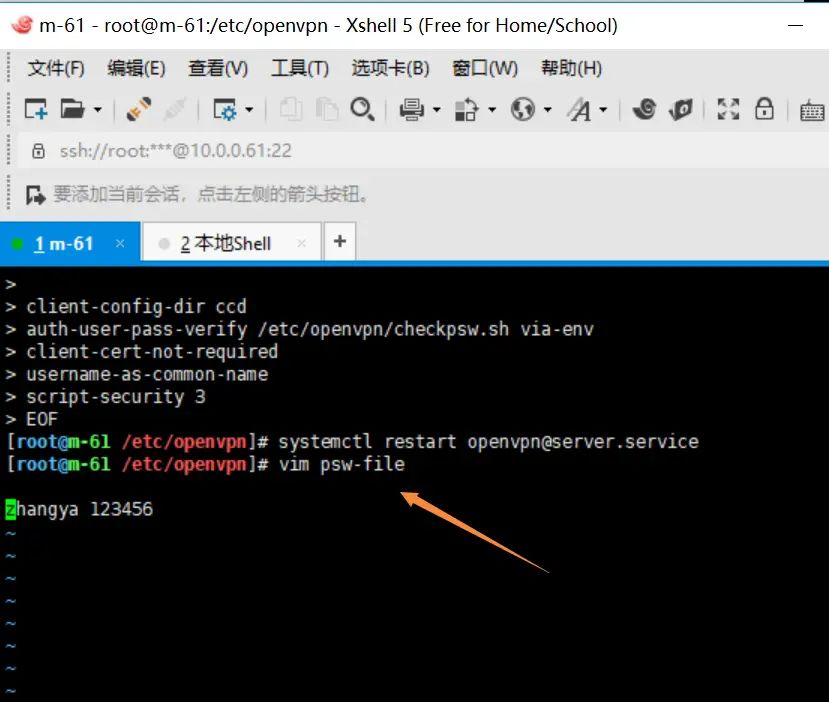
2.服务端创建密码文件
cat >/etc/openvpn/psw-file <<EOF
zhangya 123456
EOF
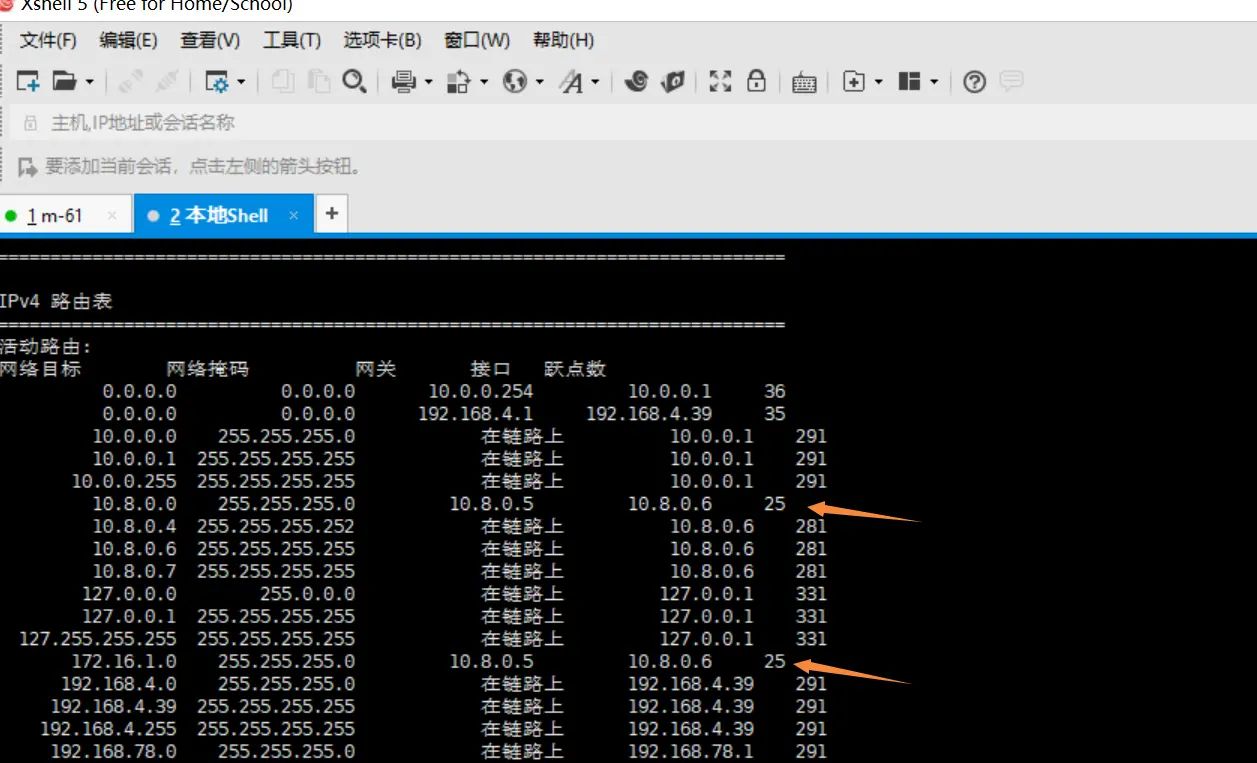
路由表查看
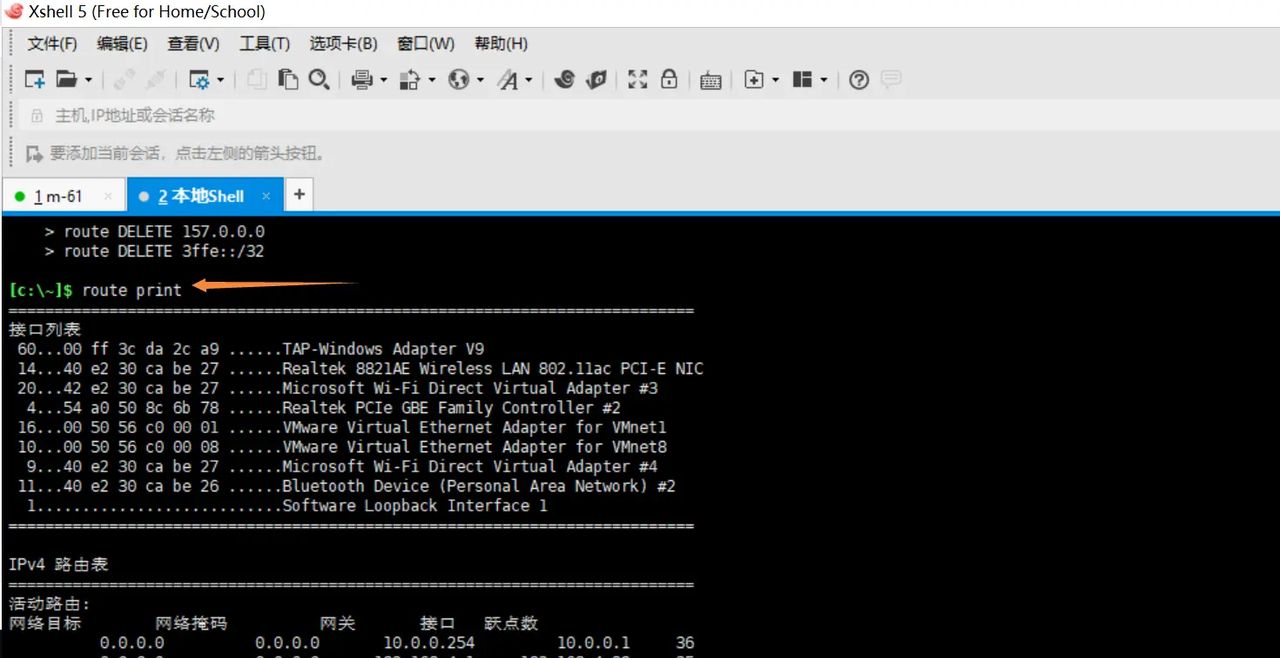
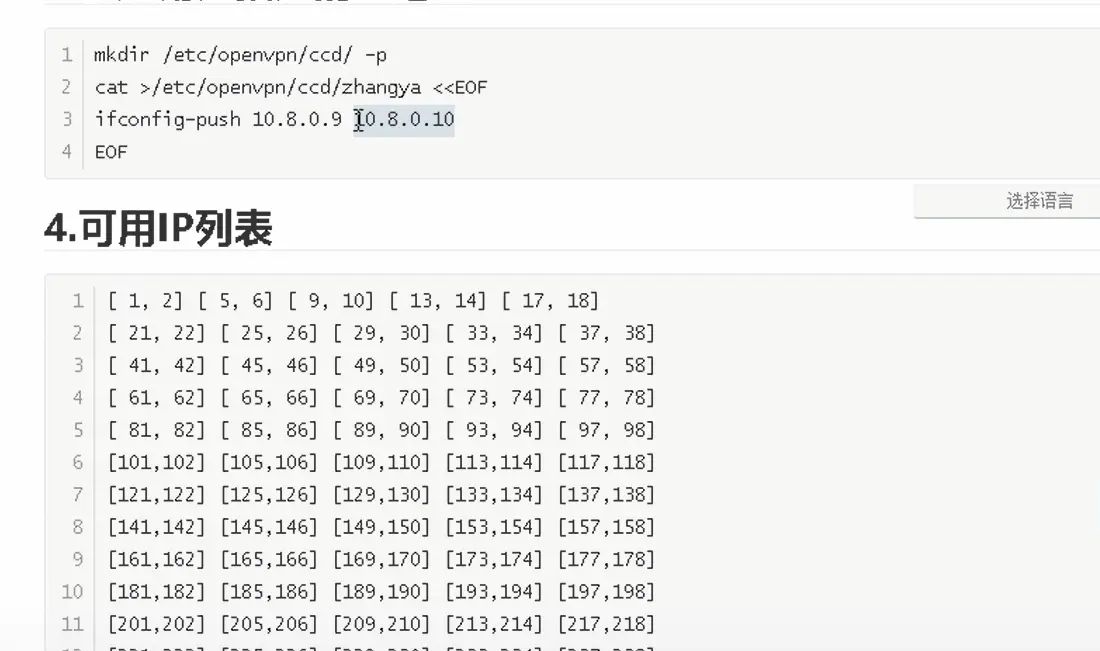
3.创建用户指定的IP地址
也可以手动配ip地址给zhangya用户
但是10.8.0.5 和10.8.0.6已经使用了
mkdir /etc/openvpn/ccd/ -p
cat >/etc/openvpn/ccd/zhangya <<EOF
ifconfig-push 10.8.0.9 10.8.0.10
EOF
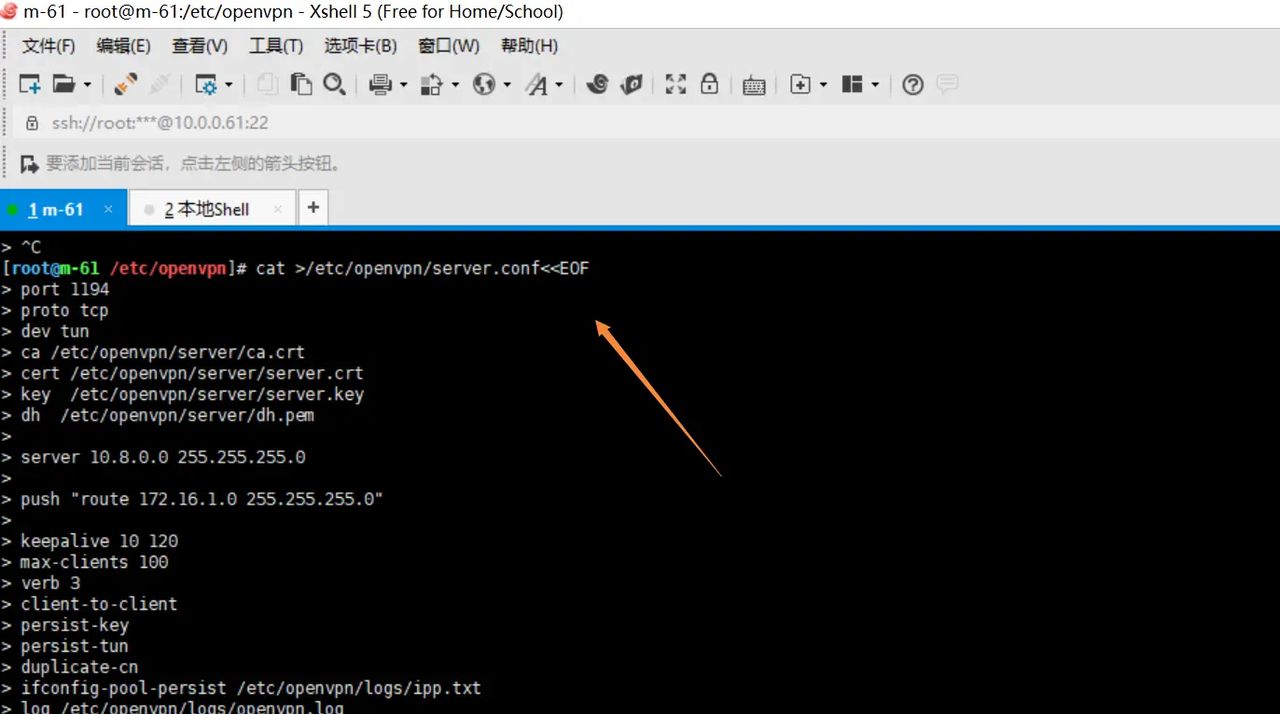
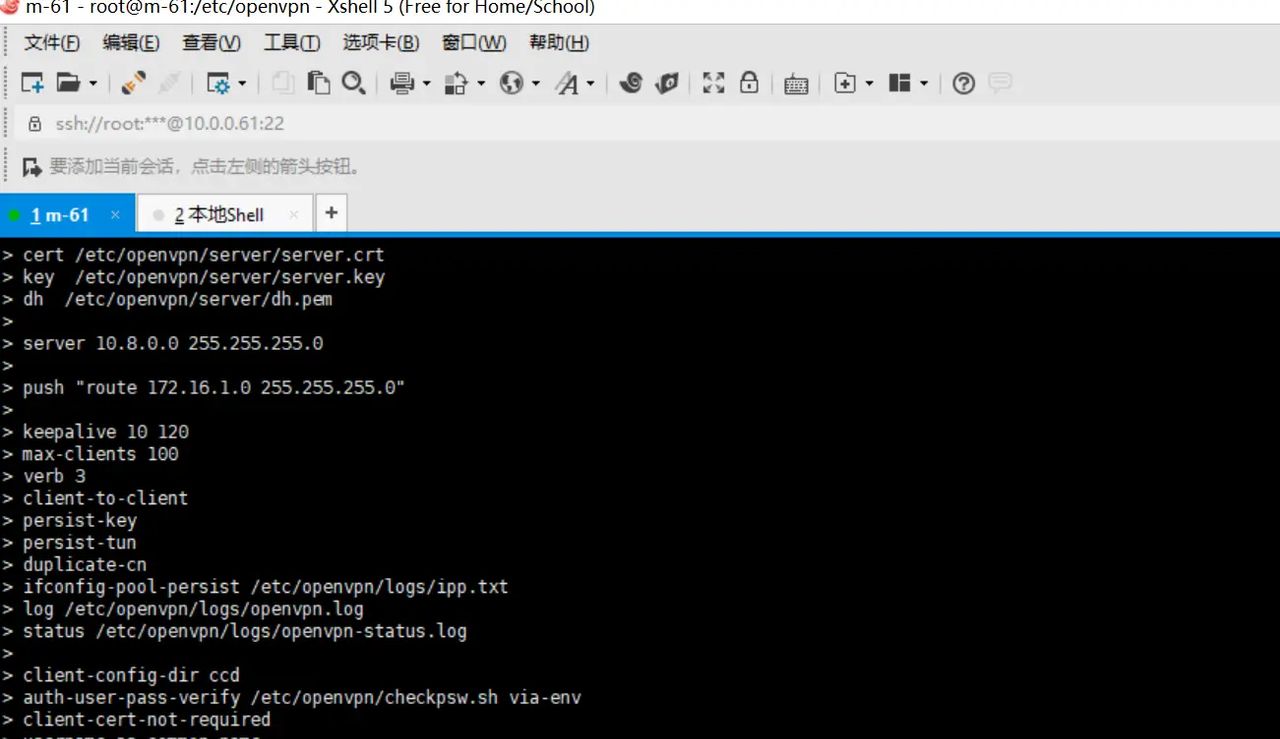
4.修改服务端配置以支持密码认证
cat >/etc/openvpn/server.conf<<EOF
port 1194
proto tcp
dev tun
ca /etc/openvpn/server/ca.crt
cert /etc/openvpn/server/server.crt
key /etc/openvpn/server/server.key
dh /etc/openvpn/server/dh.pem
server 10.8.0.0 255.255.255.0
push “route 172.16.1.0 255.255.255.0”
keepalive 10 120
max-clients 100
verb 3
client-to-client
persist-key
persist-tun
duplicate-cn
ifconfig-pool-persist /etc/openvpn/logs/ipp.txt
log /etc/openvpn/logs/openvpn.log
status /etc/openvpn/logs/openvpn-status.log
client-config-dir ccd
auth-user-pass-verify /etc/openvpn/checkpsw.sh via-env
client-cert-not-required
username-as-common-name
script-security 3
EOF
systemctl restart openvpn@server.service
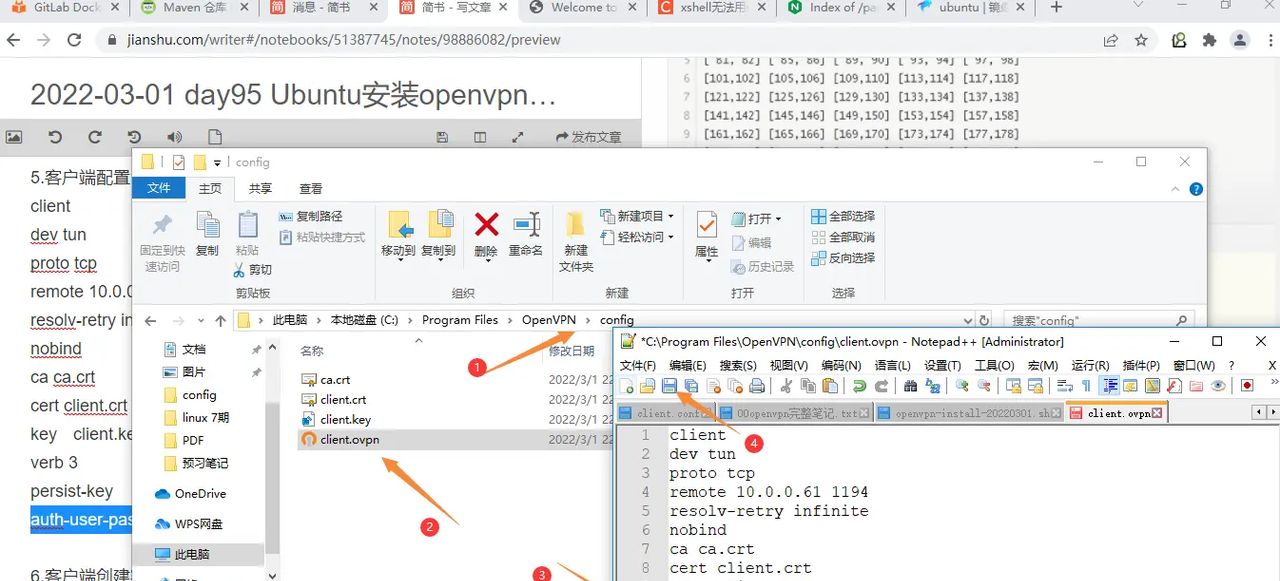
5.客户端配置
client
dev tun
proto tcp
remote 10.0.0.61 1194
resolv-retry infinite
nobind
ca ca.crt
cert client.crt
key client.key
verb 3
persist-key
auth-user-pass pass.txt
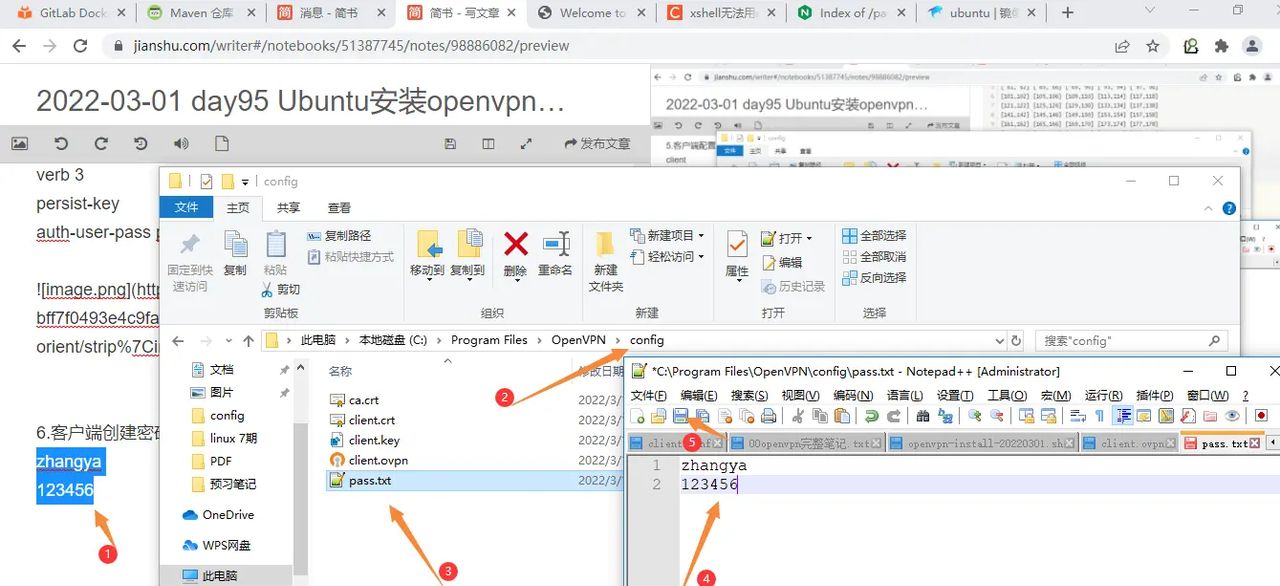
6.客户端创建密码文件
zhangya
123456
删除离职员工账号
把里面文本内容删除就行了
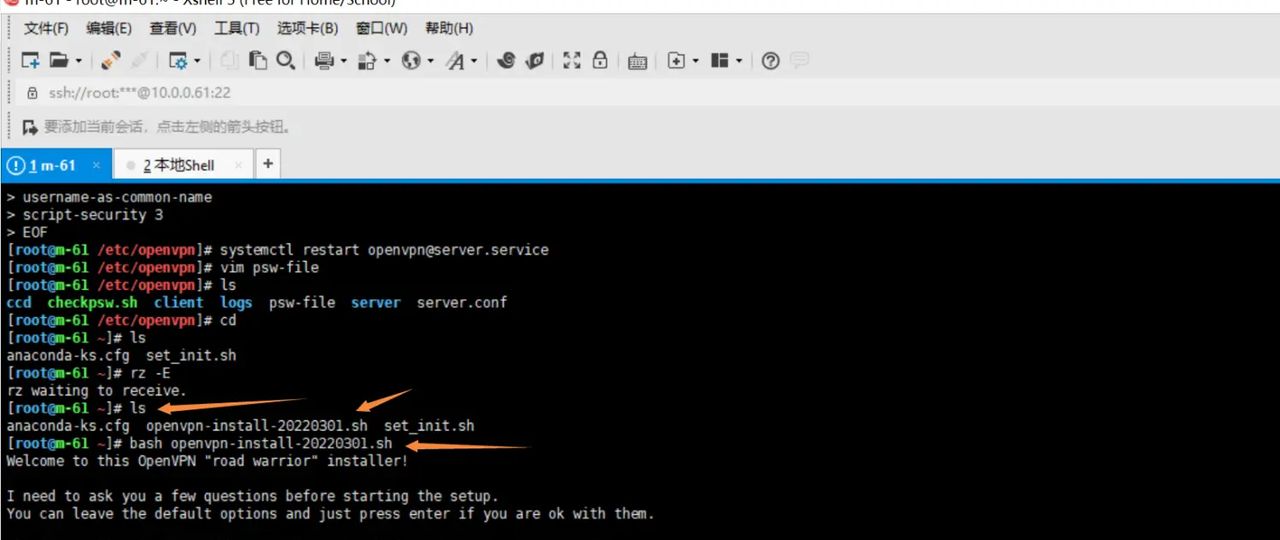
自动化牛逼脚本
#!/bin/bash
#
# https://github.com/Nyr/openvpn-install
#
# Copyright (c) 2013 Nyr. Released under the MIT License.
if grep -qs "Ubuntu 16.04" "/etc/os-release"; then
echo Ubuntu 16.04 is no longer supported in the current version of openvpn-install
Use an older version if Ubuntu 16.04 support is needed: https://git.io/vpn1604
exit
fi
# Detect Debian users running the script with "sh" instead of bash
if readlink /proc/$$/exe | grep -q "dash"; then
echo "This script needs to be run with bash, not sh"
exit
fi
if [[ "$EUID" -ne 0 ]]; then
echo "Sorry, you need to run this as root"
exit
fi
if [[ ! -e /dev/net/tun ]]; then
echo "The TUN device is not available
You need to enable TUN before running this script"
exit
fi
if [[ -e /etc/debian_version ]]; then
OS=debian
GROUPNAME=nogroup
elif [[ -e /etc/centos-release || -e /etc/redhat-release ]]; then
OS=centos
GROUPNAME=nobody
else
echo "Looks like you aren t running this installer on Debian, Ubuntu or CentOS"
exit
fi
newclient () {
# Generates the custom client.ovpn
cp /etc/openvpn/server/client-common.txt ~/$1.ovpn
echo "<ca>" >> ~/$1.ovpn
cat /etc/openvpn/server/easy-rsa/pki/ca.crt >> ~/$1.ovpn
echo "</ca>" >> ~/$1.ovpn
echo "<cert>" >> ~/$1.ovpn
sed -ne /BEGIN CERTIFICATE/,$ p /etc/openvpn/server/easy-rsa/pki/issued/$1.crt >> ~/$1.ovpn
echo "</cert>" >> ~/$1.ovpn
echo "<key>" >> ~/$1.ovpn
cat /etc/openvpn/server/easy-rsa/pki/private/$1.key >> ~/$1.ovpn
echo "</key>" >> ~/$1.ovpn
echo "<tls-auth>" >> ~/$1.ovpn
sed -ne /BEGIN OpenVPN Static key/,$ p /etc/openvpn/server/ta.key >> ~/$1.ovpn
echo "</tls-auth>" >> ~/$1.ovpn
}
if [[ -e /etc/openvpn/server/server.conf ]]; then
while :
do
clear
echo "Looks like OpenVPN is already installed."
echo
echo "What do you want to do?"
echo " 1) Add a new user"
echo " 2) Revoke an existing user"
echo " 3) Remove OpenVPN"
echo " 4) Exit"
read -p "Select an option [1-4]: " option
case $option in
1)
echo
echo "Tell me a name for the client certificate."
echo "Please, use one word only, no special characters."
read -p "Client name: " -e CLIENT
cd /etc/openvpn/server/easy-rsa/
EASYRSA_CERT_EXPIRE=3650 ./easyrsa build-client-full $CLIENT nopass
# Generates the custom client.ovpn
newclient "$CLIENT"
echo
echo "Client $CLIENT added, configuration is available at:" ~/"$CLIENT.ovpn"
exit
;;
2)
# This option could be documented a bit better and maybe even be simplified
# ...but what can I say, I want some sleep too
NUMBEROFCLIENTS=$(tail -n +2 /etc/openvpn/server/easy-rsa/pki/index.txt | grep -c "^V")
if [[ "$NUMBEROFCLIENTS" = 0 ]]; then
echo
echo "You have no existing clients!"
exit
fi
echo
echo "Select the existing client certificate you want to revoke:"
tail -n +2 /etc/openvpn/server/easy-rsa/pki/index.txt | grep "^V" | cut -d = -f 2 | nl -s )
if [[ "$NUMBEROFCLIENTS" = 1 ]]; then
read -p "Select one client [1]: " CLIENTNUMBER
else
read -p "Select one client [1-$NUMBEROFCLIENTS]: " CLIENTNUMBER
fi
CLIENT=$(tail -n +2 /etc/openvpn/server/easy-rsa/pki/index.txt | grep "^V" | cut -d = -f 2 | sed -n "$CLIENTNUMBER"p)
echo
read -p "Do you really want to revoke access for client $CLIENT? [y/N]: " -e REVOKE
if [[ "$REVOKE" = y || "$REVOKE" = Y ]]; then
cd /etc/openvpn/server/easy-rsa/
./easyrsa --batch revoke $CLIENT
EASYRSA_CRL_DAYS=3650 ./easyrsa gen-crl
rm -f pki/reqs/$CLIENT.req
rm -f pki/private/$CLIENT.key
rm -f pki/issued/$CLIENT.crt
rm -f /etc/openvpn/server/crl.pem
cp /etc/openvpn/server/easy-rsa/pki/crl.pem /etc/openvpn/server/crl.pem
# CRL is read with each client connection, when OpenVPN is dropped to nobody
chown nobody:$GROUPNAME /etc/openvpn/server/crl.pem
echo
echo "Certificate for client $CLIENT revoked!"
else
echo
echo "Certificate revocation for client $CLIENT aborted!"
fi
exit
;;
3)
echo
read -p "Do you really want to remove OpenVPN? [y/N]: " -e REMOVE
if [[ "$REMOVE" = y || "$REMOVE" = Y ]]; then
PORT=$(grep ^port /etc/openvpn/server/server.conf | cut -d " " -f 2)
PROTOCOL=$(grep ^proto /etc/openvpn/server/server.conf | cut -d " " -f 2)
if pgrep firewalld; then
IP=$(firewall-cmd --direct --get-rules ipv4 nat POSTROUTING | grep -s 10.8.0.0/24 " " ! " " -d 10.8.0.0/24 -j SNAT --to | cut -d " " -f 10)
IP_LAN=$(ifconfig eth1|awk NR==2{print $2} )
# Using both permanent and not permanent rules to avoid a firewalld reload.
firewall-cmd --remove-port=$PORT/$PROTOCOL
firewall-cmd --zone=trusted --remove-source=10.8.0.0/24
firewall-cmd --permanent --remove-port=$PORT/$PROTOCOL
firewall-cmd --permanent --zone=trusted --remove-source=10.8.0.0/24
firewall-cmd --direct --remove-rule ipv4 nat POSTROUTING 0 -s 10.8.0.0/24 ! -d 10.8.0.0/24 -j SNAT --to $IP_LAN
firewall-cmd --permanent --direct --remove-rule ipv4 nat POSTROUTING 0 -s 10.8.0.0/24 ! -d 10.8.0.0/24 -j SNAT --to $IP_LAN
else
systemctl disable --now openvpn-iptables.service
rm -f /etc/systemd/system/openvpn-iptables.service
fi
if sestatus 2>/dev/null | grep "Current mode" | grep -q "enforcing" && [[ "$PORT" != 1194 ]]; then
semanage port -d -t openvpn_port_t -p $PROTOCOL $PORT
fi
systemctl disable --now openvpn-server@server.service
rm -rf /etc/openvpn/server
rm -f /etc/sysctl.d/30-openvpn-forward.conf
if [[ "$OS" = debian ]]; then
apt-get remove --purge -y openvpn
else
yum remove openvpn -y
fi
echo
echo "OpenVPN removed!"
else
echo
echo "Removal aborted!"
fi
exit
;;
4) exit;;
esac
done
else
clear
echo Welcome to this OpenVPN "road warrior" installer!
echo
# OpenVPN setup and first user creation
echo "I need to ask you a few questions before starting the setup."
echo "You can leave the default options and just press enter if you are ok with them."
echo
echo "First, provide the IPv4 address of the network interface you want OpenVPN"
echo "listening to."
# Autodetect IP address and pre-fill for the user
IP=$(ip addr | grep inet | grep -v inet6 | grep -vE 127.[0-9]{1,3}.[0-9]{1,3}.[0-9]{1,3} | grep -oE [0-9]{1,3}.[0-9]{1,3}.[0-9]{1,3}.[0-9]{1,3} | head -1)
IP_LAN=$(ifconfig eth1|awk NR==2{print $2} )
read -p "IP address: " -e -i $IP IP
# If $IP is a private IP address, the server must be behind NAT
if echo "$IP" | grep -qE ^(10.|172.1[6789].|172.2[0-9].|172.3[01].|192.168) ; then
echo
echo "This server is behind NAT. What is the public IPv4 address or hostname?"
read -p "Public IP address / hostname: " -e -i $IP PUBLICIP
fi
echo
echo "Which protocol do you want for OpenVPN connections?"
echo " 1) UDP (recommended)"
echo " 2) TCP"
read -p "Protocol [1-2]: " -e -i 1 PROTOCOL
case $PROTOCOL in
1)
PROTOCOL=udp
;;
2)
PROTOCOL=tcp
;;
esac
echo
echo "What port do you want OpenVPN listening to?"
read -p "Port: " -e -i 1194 PORT
echo
echo "Which DNS do you want to use with the VPN?"
echo " 1) Current system resolvers"
echo " 2) 1.1.1.1"
echo " 3) Google"
echo " 4) OpenDNS"
echo " 5) Verisign"
read -p "DNS [1-5]: " -e -i 1 DNS
echo
echo "Finally, tell me your name for the client certificate."
echo "Please, use one word only, no special characters."
read -p "Client name: " -e -i client CLIENT
echo
echo "Okay, that was all I needed. We are ready to set up your OpenVPN server now."
read -n1 -r -p "Press any key to continue..."
if [[ "$OS" = debian ]]; then
apt-get update
apt-get install openvpn iptables openssl ca-certificates -y
else
# Else, the distro is CentOS
yum install epel-release -y
yum install openvpn iptables openssl ca-certificates -y
fi
# Get easy-rsa
EASYRSAURL= https://github.com/OpenVPN/easy-rsa/releases/download/v3.0.5/EasyRSA-nix-3.0.5.tgz
wget -O ~/easyrsa.tgz "$EASYRSAURL" 2>/dev/null || curl -Lo ~/easyrsa.tgz "$EASYRSAURL"
tar xzf ~/easyrsa.tgz -C ~/
mv ~/EasyRSA-3.0.5/ /etc/openvpn/server/
mv /etc/openvpn/server/EasyRSA-3.0.5/ /etc/openvpn/server/easy-rsa/
chown -R root:root /etc/openvpn/server/easy-rsa/
rm -f ~/easyrsa.tgz
cd /etc/openvpn/server/easy-rsa/
# Create the PKI, set up the CA and the server and client certificates
./easyrsa init-pki
./easyrsa --batch build-ca nopass
EASYRSA_CERT_EXPIRE=3650 ./easyrsa build-server-full server nopass
EASYRSA_CERT_EXPIRE=3650 ./easyrsa build-client-full $CLIENT nopass
EASYRSA_CRL_DAYS=3650 ./easyrsa gen-crl
# Move the stuff we need
cp pki/ca.crt pki/private/ca.key pki/issued/server.crt pki/private/server.key pki/crl.pem /etc/openvpn/server
# CRL is read with each client connection, when OpenVPN is dropped to nobody
chown nobody:$GROUPNAME /etc/openvpn/server/crl.pem
# Generate key for tls-auth
openvpn --genkey --secret /etc/openvpn/server/ta.key
# Create the DH parameters file using the predefined ffdhe2048 group
echo -----BEGIN DH PARAMETERS-----
MIIBCAKCAQEA//////////+t+FRYortKmq/cViAnPTzx2LnFg84tNpWp4TZBFGQz
+8yTnc4kmz75fS/jY2MMddj2gbICrsRhetPfHtXV/WVhJDP1H18GbtCFY2VVPe0a
87VXE15/V8k1mE8McODmi3fipona8+/och3xWKE2rec1MKzKT0g6eXq8CrGCsyT7
YdEIqUuyyOP7uWrat2DX9GgdT0Kj3jlN9K5W7edjcrsZCwenyO4KbXCeAvzhzffi
7MA0BM0oNC9hkXL+nOmFg/+OTxIy7vKBg8P+OxtMb61zO7X8vC7CIAXFjvGDfRaD
ssbzSibBsu/6iGtCOGEoXJf//////////wIBAg==
-----END DH PARAMETERS----- > /etc/openvpn/server/dh.pem
# Generate server.conf
echo "port $PORT
proto $PROTOCOL
dev tun
sndbuf 0
rcvbuf 0
ca ca.crt
cert server.crt
key server.key
dh dh.pem
auth SHA512
tls-auth ta.key 0
topology subnet
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt" > /etc/openvpn/server/server.conf
NETWORK=$(echo "172.16.1.61"|sed -r s#([0-9]+.[0-9]+.[0-9]+).[0-9]+$#1.0#g )
echo "push "route ${NETWORK} 255.255.255.0"" >> /etc/openvpn/server/server.conf
#change by zhangya 20190628
#echo push "redirect-gateway def1 bypass-dhcp" >> /etc/openvpn/server/server.conf
# DNS
#case $DNS in
# 1)
# # Locate the proper resolv.conf
# # Needed for systems running systemd-resolved
# if grep -q "127.0.0.53" "/etc/resolv.conf"; then
# RESOLVCONF= /run/systemd/resolve/resolv.conf
# else
# RESOLVCONF= /etc/resolv.conf
# fi
# # Obtain the resolvers from resolv.conf and use them for OpenVPN
# # change by zhangya 20190628
# #grep -v # $RESOLVCONF | grep nameserver | grep -E -o [0-9]{1,3}.[0-9]{1,3}.[0-9]{1,3}.[0-9]{1,3} | while read line; do
# # echo "push "dhcp-option DNS $line"" >> /etc/openvpn/server/server.conf
# #done
# ;;
# 2)
# echo push "dhcp-option DNS 1.1.1.1" >> /etc/openvpn/server/server.conf
# echo push "dhcp-option DNS 1.0.0.1" >> /etc/openvpn/server/server.conf
# ;;
# 3)
# echo push "dhcp-option DNS 8.8.8.8" >> /etc/openvpn/server/server.conf
# echo push "dhcp-option DNS 8.8.4.4" >> /etc/openvpn/server/server.conf
# ;;
# 4)
# echo push "dhcp-option DNS 208.67.222.222" >> /etc/openvpn/server/server.conf
# echo push "dhcp-option DNS 208.67.220.220" >> /etc/openvpn/server/server.conf
# ;;
# 5)
# echo push "dhcp-option DNS 64.6.64.6" >> /etc/openvpn/server/server.conf
# echo push "dhcp-option DNS 64.6.65.6" >> /etc/openvpn/server/server.conf
# ;;
#esac
echo "keepalive 10 120
cipher AES-256-CBC
user nobody
group $GROUPNAME
persist-key
persist-tun
status openvpn-status.log
verb 3
crl-verify crl.pem" >> /etc/openvpn/server/server.conf
# Enable net.ipv4.ip_forward for the system
echo net.ipv4.ip_forward=1 > /etc/sysctl.d/30-openvpn-forward.conf
# Enable without waiting for a reboot or service restart
echo 1 > /proc/sys/net/ipv4/ip_forward
if pgrep firewalld; then
# Using both permanent and not permanent rules to avoid a firewalld
# reload.
# We don t use --add-service=openvpn because that would only work with
# the default port and protocol.
firewall-cmd --add-port=$PORT/$PROTOCOL
firewall-cmd --zone=trusted --add-source=10.8.0.0/24
firewall-cmd --permanent --add-port=$PORT/$PROTOCOL
firewall-cmd --permanent --zone=trusted --add-source=10.8.0.0/24
# Set NAT for the VPN subnet
firewall-cmd --direct --add-rule ipv4 nat POSTROUTING 0 -s 10.8.0.0/24 ! -d 10.8.0.0/24 -j SNAT --to $IP_LAN
firewall-cmd --permanent --direct --add-rule ipv4 nat POSTROUTING 0 -s 10.8.0.0/24 ! -d 10.8.0.0/24 -j SNAT --to $IP_LAN
else
# Create a service to set up persistent iptables rules
echo "[Unit]
Before=network.target
[Service]
Type=oneshot
ExecStart=/sbin/iptables -t nat -A POSTROUTING -s 10.8.0.0/24 ! -d 10.8.0.0/24 -j SNAT --to $IP_LAN
ExecStart=/sbin/iptables -I INPUT -p $PROTOCOL --dport $PORT -j ACCEPT
ExecStart=/sbin/iptables -I FORWARD -s 10.8.0.0/24 -j ACCEPT
ExecStart=/sbin/iptables -I FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT
ExecStop=/sbin/iptables -t nat -D POSTROUTING -s 10.8.0.0/24 ! -d 10.8.0.0/24 -j SNAT --to $IP_LAN
ExecStop=/sbin/iptables -D INPUT -p $PROTOCOL --dport $PORT -j ACCEPT
ExecStop=/sbin/iptables -D FORWARD -s 10.8.0.0/24 -j ACCEPT
ExecStop=/sbin/iptables -D FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT
RemainAfterExit=yes
[Install]
WantedBy=multi-user.target" > /etc/systemd/system/openvpn-iptables.service
systemctl enable --now openvpn-iptables.service
fi
# If SELinux is enabled and a custom port was selected, we need this
if sestatus 2>/dev/null | grep "Current mode" | grep -q "enforcing" && [[ "$PORT" != 1194 ]]; then
# Install semanage if not already present
if ! hash semanage 2>/dev/null; then
if grep -qs "CentOS Linux release 7" "/etc/centos-release"; then
yum install policycoreutils-python -y
else
yum install policycoreutils-python-utils -y
fi
fi
semanage port -a -t openvpn_port_t -p $PROTOCOL $PORT
fi
# And finally, enable and start the OpenVPN service
systemctl enable --now openvpn-server@server.service
# If the server is behind a NAT, use the correct IP address
if [[ "$PUBLICIP" != "" ]]; then
IP=$PUBLICIP
fi
# client-common.txt is created so we have a template to add further users later
echo "client
dev tun
proto $PROTOCOL
sndbuf 0
rcvbuf 0
remote $IP $PORT
resolv-retry infinite
nobind
persist-key
persist-tun
remote-cert-tls server
auth SHA512
cipher AES-256-CBC
setenv opt block-outside-dns
key-direction 1
verb 3" > /etc/openvpn/server/client-common.txt
# Generates the custom client.ovpn
newclient "$CLIENT"
echo
echo "Finished!"
echo
echo "Your client configuration is available at:" ~/"$CLIENT.ovpn"
echo "If you want to add more clients, you simply need to run this script again!"
fi
相关文章